Manual of resistance to surveillance capitalism
- 0 Comments about fork
- 1 Introduction
- 2 Golden rules
- 3 Computer
- 3-1 Operating Systems
- 3-2 Services and programs
- 4 Smartphone
- 4-1 Operating Systems
- 4-2 Applications
- 5 Browsers
- 5-1 Firefox
- 5-2 Tor Browser
- 6 Service instances
- 6-1 Searx
- 6-2 Invidious
- 6-3 Videoconference
- 6-4 DNS
- 7 Additional resources and sources
- 8 Configurations
- 8-1 Operating systems
- 8-2 Apps and software
- 8-3 Firefox
I have seen the need to fork this document of Valentin Delacour hosted here under his approval and license to give it more visibility, readability, comfort, improvement in some aspects and participation. If someone forks any of the 2 they should do the same.
I think that we should share how much more the better and the knowledge about good practices to follow regarding security, privacy and open source that are detailed are no exception.
We are open to changing the format of this document, for now I have thought that this is a good way, but it could be improved.
I don't consider myself an expert on the subject. In fact I do not follow all the recommendations to the letter. But I would like over time to leave aside services that I think I should not use for various reasons, change ways of accessing certain content, use other strategies, etc.
To actively participate you can:
I recommend you participate in:
- Official Telegram Group
- Official Discord Group - Although due to various privacy and security reasons we do not recommend it.
- Official Element group - Request invitation
The objective of the group is to collectively promote good customs in terms of privacy, security and also open source/free programs/apps, services and operating systems to resist the collection and exploitation of personal data by private companies.
I think that they take advantage of the ignorance of the majority to do things that they should not and benefit from it behind our backs. The good thing is that there are people who realize it because they understand the subject and share it with the community.
This document has been copied 1: 1 with very slight modifications in version 7/12/2020 and from now on it will undergo modifications following the following strategies:
- Following updates of the original file
- Pull requests from the community
- Own discoveries
The most notable improvements are:
- It encourages a more orderly, effective, public participation
- Images of the apps to better identify them
- Links to them to find them quickly
Now, the document begins. Put on your belt curves are coming!
The main objective of this document is to propose tools and alternatives to protect data and privacy from predation by private companies under the current system of surveillance capitalism. Now, follow the following recommendations also allows to improve, in certain measures, the protection against other entities such as state services or pirates, for example.
This list is intended for all persons aware or aware of the importance of data protection in our society, regardless of your knowledge of the subject. It is not intended for people needing anonymity total part of their function to risks such as political opponents or some journalists, even if some proposed options might suit them. Effectively, privacy does not necessarily equal anonymity.
The list format was chosen in order to make your query as efficient as possible possible. This approach precludes detailing true explanations. So I invite you to look for the ones they need on their own or in additional resources mentioned in point 6 of the document. With the purpose of proposing the more reputable and practical options without being too stuffy, the list does not have to vocation to be exhaustive and remains subjective despite seeking to have the greatest possible objectivity.
This list proposes a first prioritization (order of appearance and presence or not of parentheses) subjective based on the privacy/usability report in order to help them choose between the different options mentioned. A second prioritization (colors) is based solely on estimated privacy:
🟢green (true respect for privacy)
🔵blue (respect for privacy under conditions or presence of a problematic item)
🔴red (does not guarantee privacy but still being preferable to the GAFAM options)
⚫colorless (lack of elements to form an estimate, or a prioritization is not relevant for entry into question). The presence of an asterisk indicates that the mentioned option is still in development phase.
I hope this document will help you improve the protection of your data personal and those of her close ones. Although being the fruit of several years of searches and experiments, this work obviously remains perfectible. Any suggestion or comment is then more than welcome to the email: "[email protected]". Several months after the present version of the document, you must assume that certain information given will be obsolete. The document being frequently updated, you are invited to get the latest version on the following website: “https://codeberg.org/PrivacyFirst/PrivacyFirst/issues”.
- Avoid using GAFAM services and programs (Google, Amazon, Facebook, Apple and Microsoft) WHENEVER possible. It is best to remove your eventual accounts.
- Always review all the settings and authorizations of what is used and optimize them to limit the collection of personal data as much as possible.
- Only install the necessary programs/applications as they are potential accesses to your personal data.
- Use free/open source programs (their codes are public and also verifiable) instead of proprietary/closed source whenever possible.
- Favor the popular free options over the unknown ones (they will be more reviewed/reliable).
- If a company offers its services for free, in general, the product it sells is you (your personal data). Due to the model imposed by the surveillance capitalism, pay now or protect them from also being the product.
- Update your programs/operating systems frequently to benefit from the latest fixes for exploitable security flaws and think about replacing the ones that no longer seem to be up to date.
- Don't use third-party antivirus, they are true vacuum cleaners of personal data. Their contribution is negligible as long as good numerical habits are maintained. Prudence and a good configuration are the best antivirus.
- Privilege Web Apps or shortcuts from the browser to access services instead of applications to install to limit access and the possibilities of collecting personal information.
- Use temporary emails to create accounts for unimportant sites/services.
- Always disable Wi-Fi, Bluetooth, and geolocation on your smartphone when not in use and don't connect to public Wi-Fi without using a VPN.
- Do not use connected objects (their purpose is to collect as much personal data as possible) or not connect them to the internet when they are essential.
Windows is currently the worst operating system in terms of privacy and security. The only OS that is easy to use and truly protecting data are the free (therefore free) Linux distributions. There is a multitude of them whose characteristics vary considerably. Here is a small selection of those offering the best user experience (always respecting privacy) or guaranteeing the best data protection. It should be remembered that each of them proposes one or more interfaces (desktop) different in terms of experience, resource consumption and appearance. There is abundant documentation online to choose which one layout and desktop environment will best suit the capabilities of your computer and your preferences as well as how to easily install it on his computer.
Desktop :
🟢![]() Linux Mint : great for beginners
Linux Mint : great for beginners
🟢![]() MX Linux : suits beginners
MX Linux : suits beginners
🟢![]() Solus : suits beginners
Solus : suits beginners
🟢![]() Parrot Home OS : improved security and privacy (confirmed users)
Parrot Home OS : improved security and privacy (confirmed users)
🟢![]() Qubes OS : extreme security (advanced users)
Qubes OS : extreme security (advanced users)
🟢![]() Whonix : anonymity by Tor and extreme security (advanced users)
Whonix : anonymity by Tor and extreme security (advanced users)
USB live (RAM) :
🟢![]() MX Linux : suits beginners
MX Linux : suits beginners
🟢![]() Tails : anonymity by Tor (confirmed users)
Tails : anonymity by Tor (confirmed users)
🟢![]() Parrot Home OS : improved security and privacy (confirmed users)
Parrot Home OS : improved security and privacy (confirmed users)
Raspberry Pi :
🟢![]() LibreELEC : multimedia center for TV
LibreELEC : multimedia center for TV
🟢![]() Plasma BigScreen* : multimedia center for TV (voice command with Mycroft AI)
Plasma BigScreen* : multimedia center for TV (voice command with Mycroft AI)
🟢![]() Raspberry Pi OS : classic operating system
Raspberry Pi OS : classic operating system
🟢![]() Batocera : console emulator, retrogaming
Batocera : console emulator, retrogaming
🟢![]() RetroPie : console emulator, retrogaming
RetroPie : console emulator, retrogaming
Browser :
Search engine :
🔴![]() Startpage (proxy Google)
Startpage (proxy Google)
Office automation :
Mail :
Video platform :
🔵![]() Invidious (proxy Youtube)
Invidious (proxy Youtube)
🔵![]() CloudTube (proxy Youtube)
CloudTube (proxy Youtube)
🔵![]() FreeTube (Youtube/Invidious client)
FreeTube (Youtube/Invidious client)
🔵![]() LBRY
LBRY
Instant messaging :
Video conferencing :
🟢![]() Jami
Jami
Social network :
Proxy de red social :
🔵![]() Nitter (Twitter)
Nitter (Twitter)
🔵![]() Libreddit (Reddit)
Libreddit (Reddit)
🔵![]() Bibliogram (Instagram)
Bibliogram (Instagram)
Translator :
Maps :
File sharing :
Colaboration :
Password manager :
Media player :
🟢![]() VLC
VLC
VPN :
🟢IVPN
Cloud :
🟢![]() Disroot (Nextcloud)
Disroot (Nextcloud)
🔵![]() Kdrive (Infomaniak)
Kdrive (Infomaniak)
Temporary mail:
Notes :
System cleaning and optimization :
Image editing and drawing :
🟢![]() Gimp
Gimp
Vector graphics editing :
Page layout :
Audio editing :
Video editing :
Metadata suppression :
Encryption tool :
Network traffic analysis:
Windows programs/games under Linux :
⚫![]() Wine
Wine
Android, in its default configuration, is currently the worst operating system in terms of privacy. Its purpose is to continuously send personal data to Google's servers to exploit and sell them. The most recommended solution today is to use a modified version of Android (custom ROM) to respect privacy. If you do not want to install or buy a smartphone with a respectful operating system (serious mistake), remember that you should absolutely avoid all Chinese brands and also Samsung. In an effort not to be fully and continuously profiled, it is essential to never connect with a Google account and use a tracker blocker. Apple's operating system (iOS), despite its marketing based on respect for privacy, also collects and exploits the personal data of its users, although without common measure to Android by default. Apple controls and limits its users more than Android, but it also offers more security and privacy protections against third parties.
Android modified for privacy :
🟢![]() CalyxOS : Android degooglized and secure with microG for better compatibility
CalyxOS : Android degooglized and secure with microG for better compatibility
🟢![]() GrapheneOS : the most private and secure degooglized Android available
GrapheneOS : the most private and secure degooglized Android available
🟢![]() /e/ OS : Degooglized LineageOS but with microG and integrated services (/e/ account)
/e/ OS : Degooglized LineageOS but with microG and integrated services (/e/ account)
🔵![]() LineageOS for microG : LineageOS with microG for better compatibility
LineageOS for microG : LineageOS with microG for better compatibility
🔵![]() Volla OS: Safe Android, without Google apps but not totally degooglized
Volla OS: Safe Android, without Google apps but not totally degooglized
🔵![]() LineageOS : Android without Google apps but not totally degooglized
LineageOS : Android without Google apps but not totally degooglized
Preinstalled hardware :
Fairphone 3 y 3+ : /e/ OS (version only available on project site /e/)
Gigaset GS290 : /e/ OS (version only available on project site /e/)
Volla Phone : Volla OS, UBports, Sailfish OS and others
Other models with /e/ OS pre-installed are available at the /e/ project site:
The proposed applications for Android and derivatives must be searched first in the free F-Droid application store (guarantee that they do not have third-party trackers) and only if they are not, in the Aurora Store. These stores must be downloaded directly from their respective official web pages.
Android and derivatives :
App store :
🔵![]() Aurora Store (proxy Play Store)
Aurora Store (proxy Play Store)
Browser :
🔵![]() Fennec (Firefox)
Fennec (Firefox)
Instant messaging :
Video conferencing :
🟢![]() Jami
Jami
Video platform :
🔴![]() Newpipe (cliente Youtube)
Newpipe (cliente Youtube)
🟢![]() Tubelab (cliente Peertube)
Tubelab (cliente Peertube)
🔵![]() LBRY
LBRY
Maps/GPS navigation:
🟢![]() Maps (OpenStreetMap)
Maps (OpenStreetMap)
Ad/Tracker Blocker:
Mail client :
Alias manager for mail :
Password manager client :
Two-factor authentication :
Web Apps :
VPN :
🟢IVPN
Mastodon, Friendica, Peertube and PixelFed client:
🟢![]() Tusky (Mastodon)
Tusky (Mastodon)
Respectful client Facebook/Twitter/Instagram :
Metadata suppression :
Encryption tool for cloud :
Radio :
Event organization :
Redirector of content YouTube, Twitter, Instagram and Google Map :
Replacement application system for Android of origin :
Keyboard :
Notes :
SMS :
Schedule :
🟢![]() Etar
Etar
File manager :
Gallery :
Audioplayer :
PDF :
Contacts :
Camera :
Voice recorder :
Call manager :
Clock :
Calculator :
To go further :
Application network isolator and traffic monitor:
Third Party Tracker Developer :
Privacy manager for applications :
🟢![]() App Warden (root)
App Warden (root)
Application stop (background):
Applications Isolator :
Network anonymization by Tor :
Location simulator :
Replacement of Google Services:
Microphone usage blocker :
Browser :
Instant messaging :
Video conferencing :
🟢![]() Jami
Jami
Ad/Tracker Blocker :
Video platform :
🔵![]() LBRY
LBRY
Mail client :
Alias manager for mail :
Password manager client :
🟢![]() Strongbox - KeePass & PwSafe
Strongbox - KeePass & PwSafe
Two-factor authentication :
Encryption tool for cloud :
Compartmentalization (using different browsers with different settings, depending on the tasks) is a recommended method to preserve privacy without sacrificing too much browsing comfort. For example, it would be to use Firefox with a restrictive configuration for general navigation. Then, use another profile of the same Firefox or Firefox ESR, configured in a less restrictive way for sites that do not load correctly or that require a connection to a personal account, and another browser for the consultation of the most recalcitrant sites to a configuration for the privacy protection (Brave or Ungoogled Chromium without settings are ideal for that task). It is also conceivable to use another browser solely dedicated to e-banking or also Tor Browser for anonymous browsing.
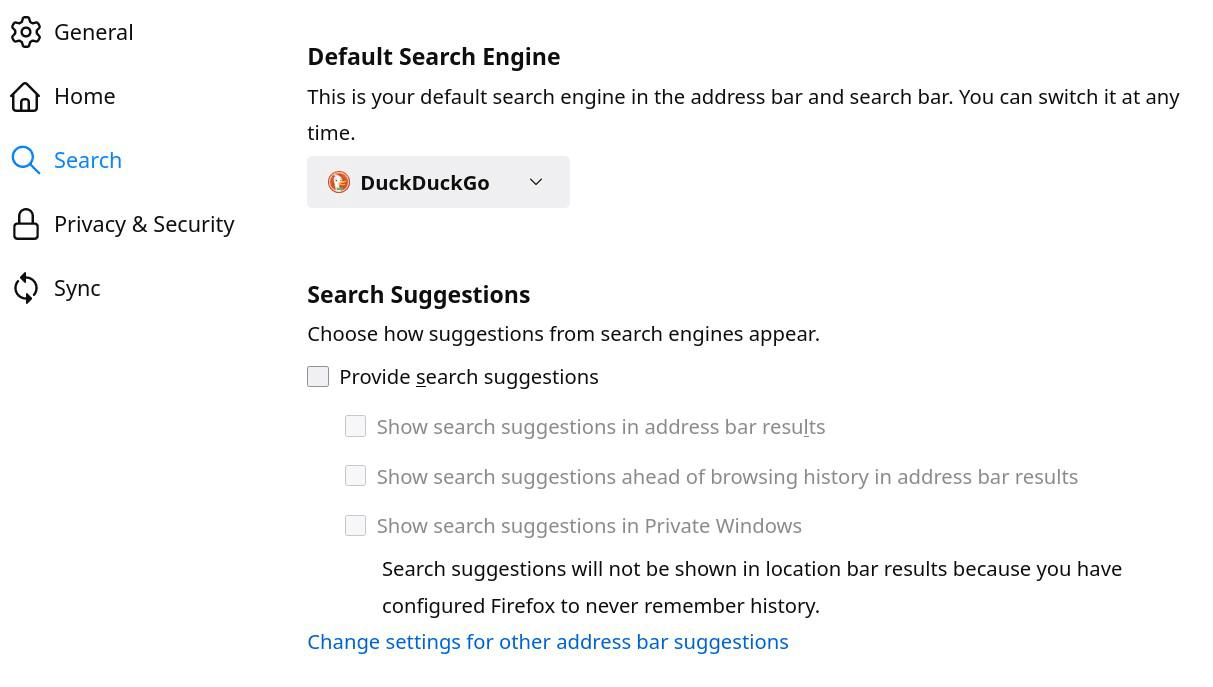
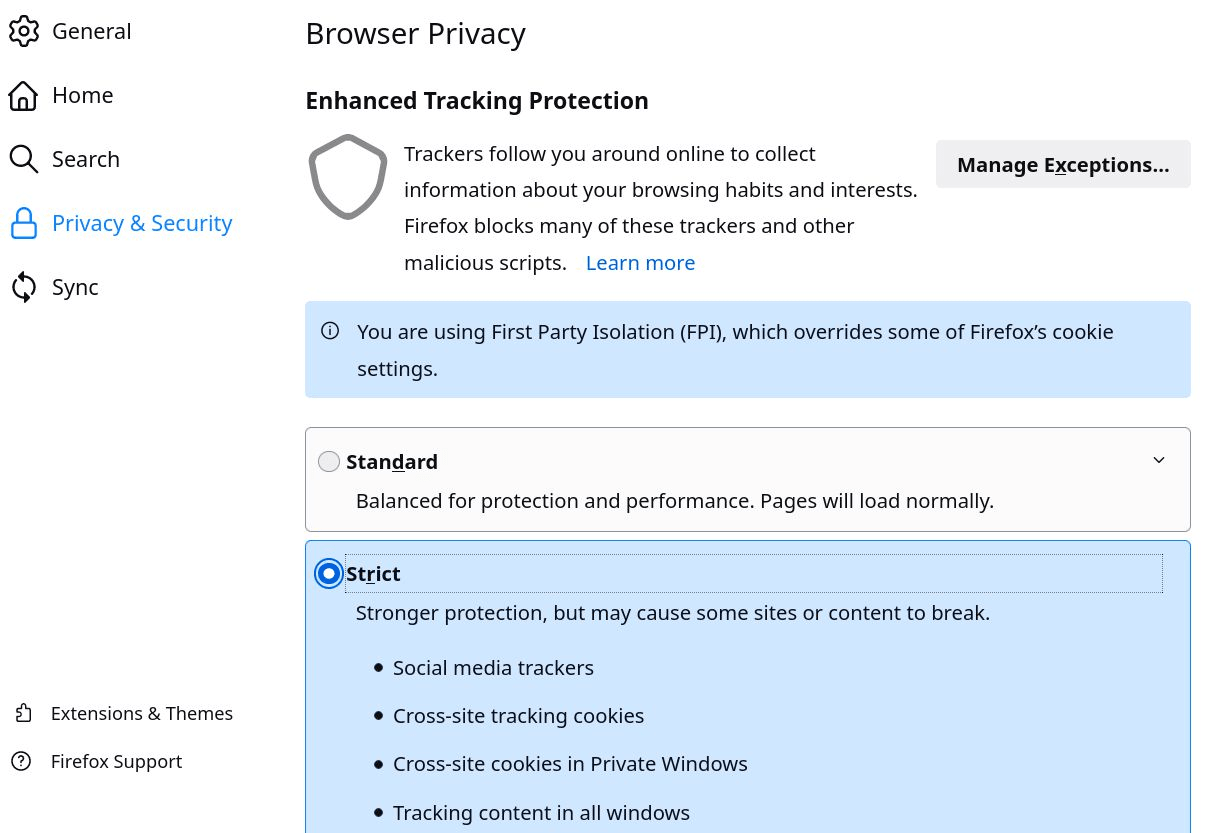
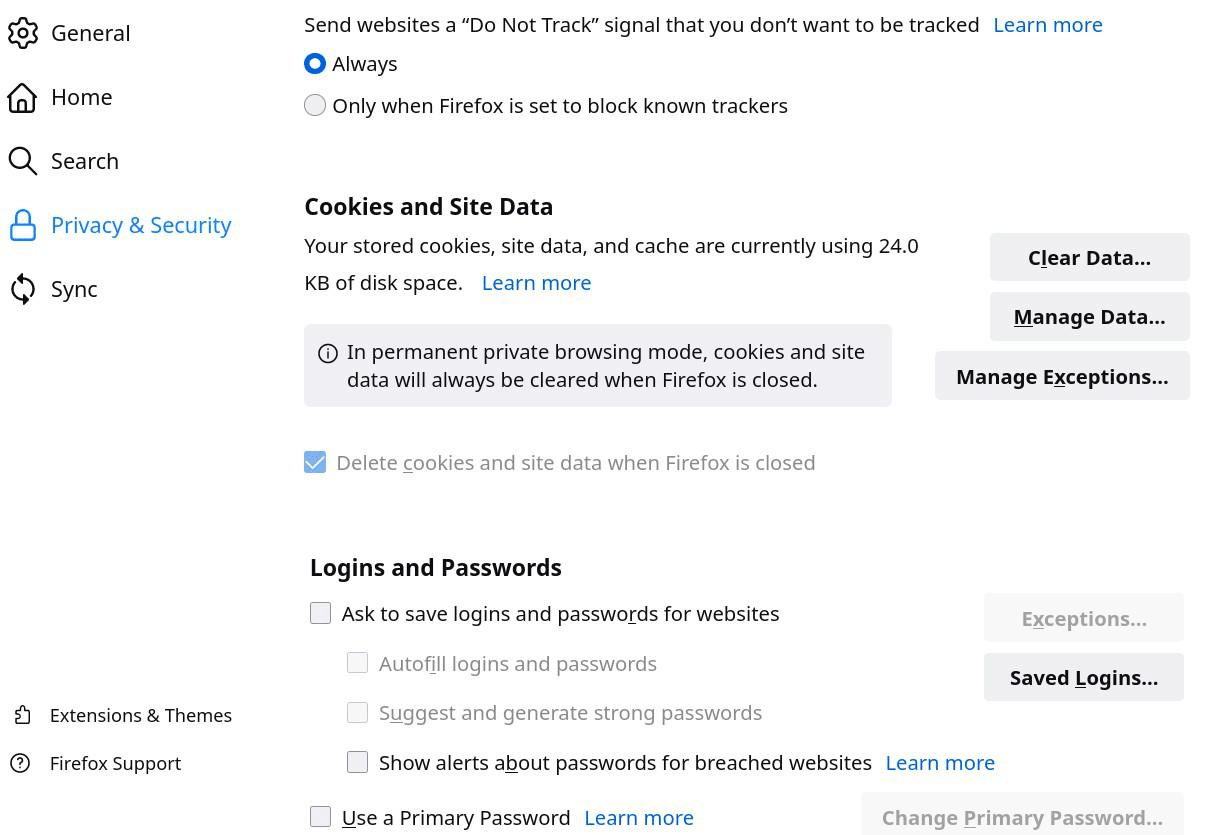
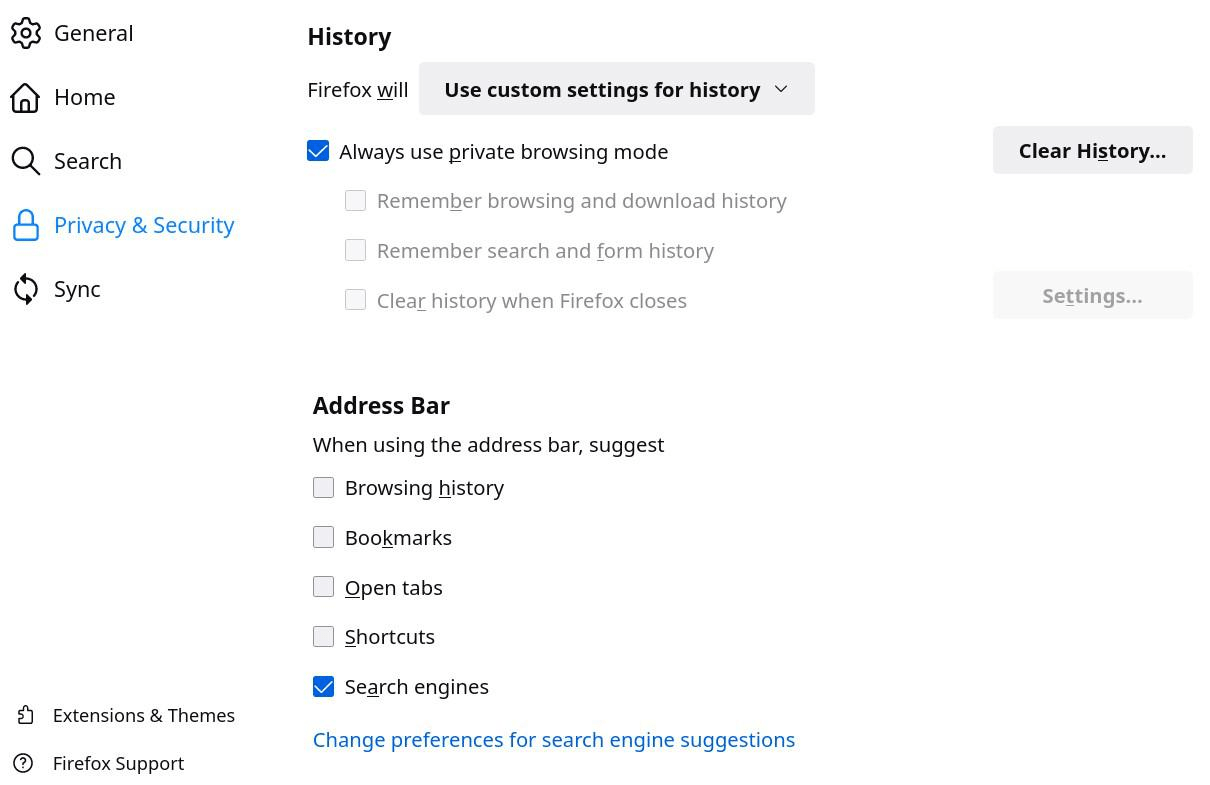
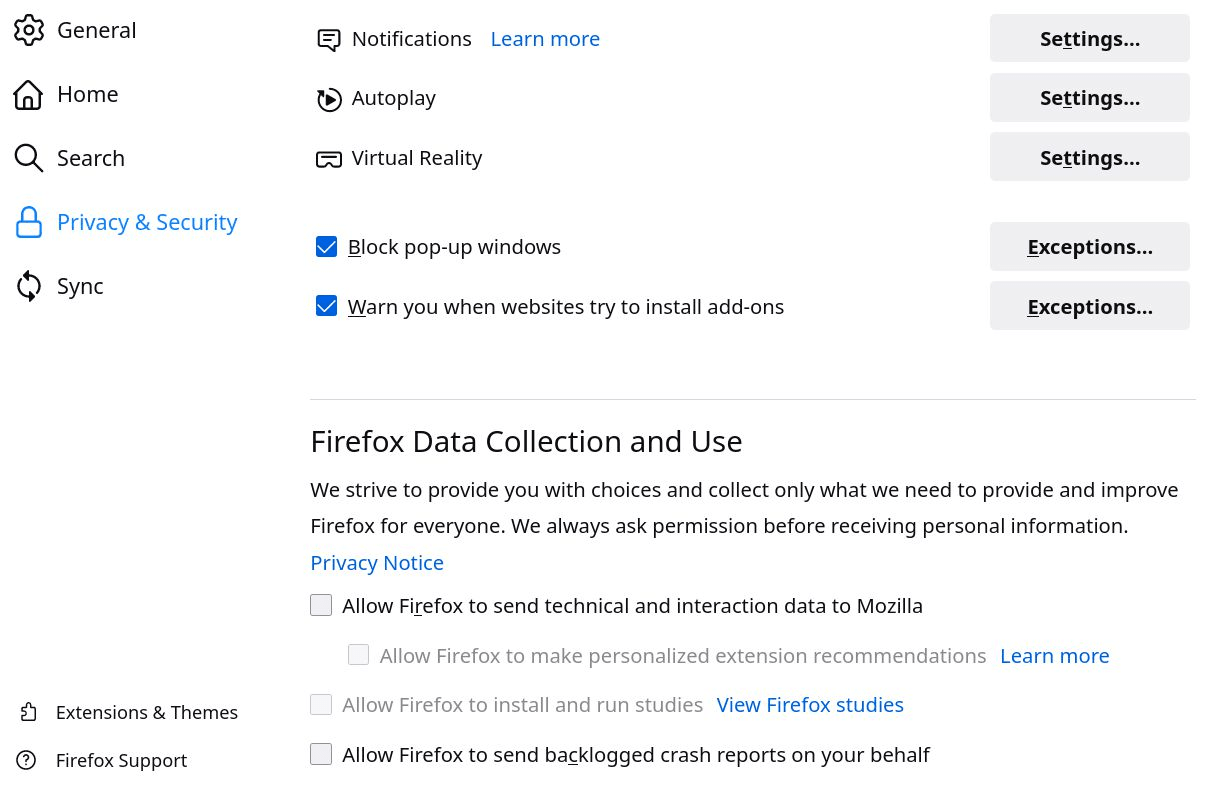
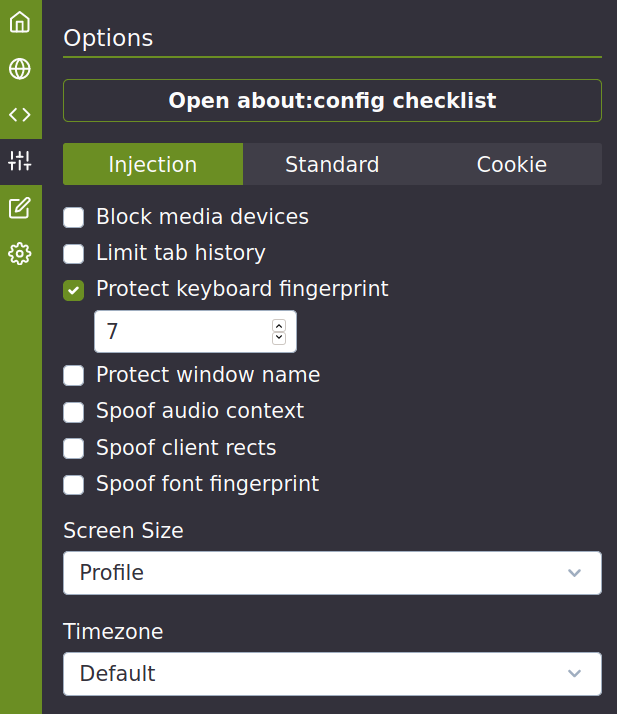
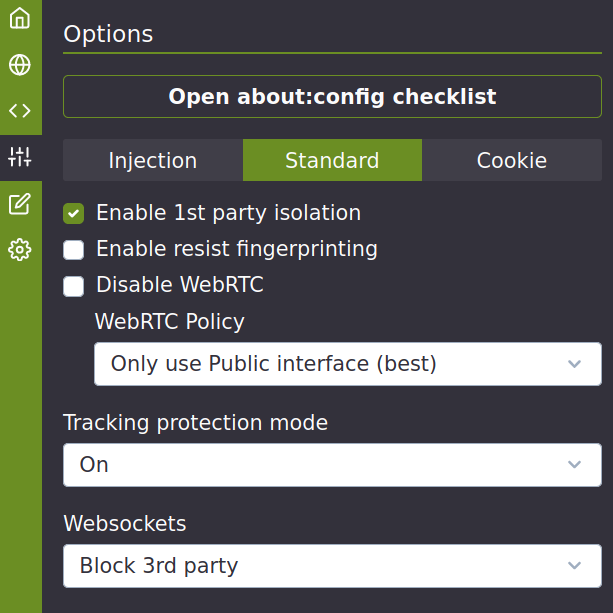
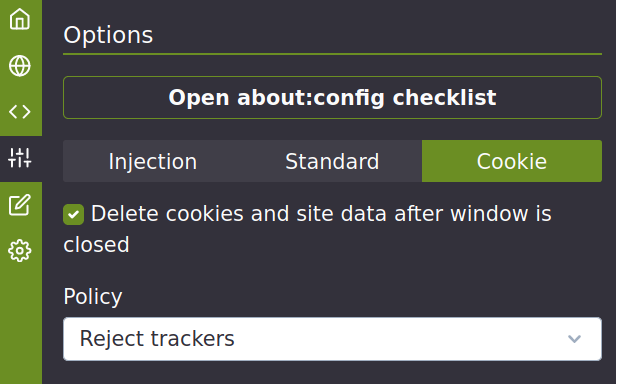
For Firefox to protect privacy, it needs to be configured appropriately (settings, extensions and about: config). All necessary settings are developed in point 8.3 of the document. These settings also apply to LibreWolf and, to a certain extent, for the mobile version of Firefox (Fennec).
Extensions :
Complete list :
![]() uBlock Origin - Chrome - Firefox
uBlock Origin - Chrome - Firefox
![]() Decentraleyes - Chrome - Firefox - Finished development? - Alternative?
Decentraleyes - Chrome - Firefox - Finished development? - Alternative?
![]() CanvasBlocker - Chrome - Firefox
CanvasBlocker - Chrome - Firefox
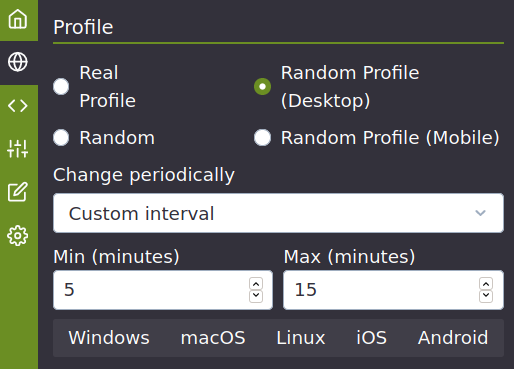
![]() Chameleon Finished development? - Alternative?
Chameleon Finished development? - Alternative?
![]() Cookie AutoDelete - Chrome - Firefox
Cookie AutoDelete - Chrome - Firefox
![]() Privacy Redirect - Chrome - Firefox
Privacy Redirect - Chrome - Firefox
![]() HTTPS Everywhere - Chrome - Firefox
HTTPS Everywhere - Chrome - Firefox
Light list :
![]() uBlock Origin - Chrome - Firefox
uBlock Origin - Chrome - Firefox
![]() Decentraleyes - Chrome - Firefox
Decentraleyes - Chrome - Firefox
![]() Cookie AutoDelete - Chrome - Firefox
Cookie AutoDelete - Chrome - Firefox
![]() HTTPS Everywhere - Chrome - Firefox
HTTPS Everywhere - Chrome - Firefox
The concept of Tor is to make Internet traffic pass through a network by anonymizing it. In the effort that the fingerprint of your browser (given among others by its configuration) does not betray your identity, Tor browsers are designed to have the same footprint regardless of users. To avoid making the footprint of your Tor browser unique, no extensions should be installed and no modifications should be made to the "about: config" settings. To preserve the given anonymity, it is also necessary not to connect to accounts that could de facto override it. The Tor network's anonymization method slows down uploads. Well, it is not recommended to use it for streaming or voluminous downloads.
Searx is a meta search engine that does not transmit personal data to used search engines. It allows, if one wishes, a very advanced configuration. The different instances (available there: https://searx.space/) do not offer all the same guarantees of privacy protection (IP address log or not, etc.)
🟢https://search.disroot.org : Google results (Startpage), no IP address log, good UI
🔵https://searx.nogafam.es : Google results included, IP address, log good UI
🟢https://search.disroot.org : Google results included, no IP address log
Invidious gives access to YouTube content (proxy) without transmitting the personal data of its users to Google. Unfortunately, its different instances (available there: https://instances.invidio.us/) frequently suffer from problems caused by Google's measures taken to prevent their operation. The Invidious instances that currently appear to be the most functional are
⚫https://invidious.snopyta.org
Jitsi Meet :
🟢FDN
BigBlueButton :
Intercontinental :
With filters against ads, trackers and malicious domains :
🟢NixNet (DoH, DoT)
🟢BlahDNS (DoH, DoT, DNSCrypt)
🔵Adguard (DoH, DoT, DNSCrypt)
🔵NextDNS (DoH, DoT, DNSCrypt)
NixNet DoH : https://adblock.any.dns.nixnet.xyz/dns-query BlahDNS DoH (Japón) : https://doh-jp.blahdns.com/dns-query
Without filters :
🟢DNSWatch (not encrypted)
🟢UncensoredDNS (DoT)
DNS.Watch IPv4 : 84.200.69.80, 84.200.70.40 DNS.Watch IPv6 : 2001:1608:10:25::1c04:b12f, 2001:1608:10:25::9249:d69b
Europe :
With filters against ads, trackers and malicious domains :
🟢BlahDNS (DoH, DoT, DNSCrypt)
🟢LibreDNS (DoH, DoT)
BlahDNS DoH (Alemania) : https://doh-de.blahdns.com/dns-query LibreDNS DoH (Alemania) : https://doh.libredns.gr/ads
Without filters :
🟢Snopyta (DoH, DoT)
🟢Digitale Gesellschaft (DoH, DoT)
🟢PowerDNS (DoH)
🟢FDN (not encrypted)
General
Excellent resources for understanding surveillance capitalism and its threats :
https://www.nogafam.es/blog/presentacion
The Social Media Dilemma, Jeff Orlowski (film) Nothing to Hide, Marc Meillassoux (documentary film) The Age of Surveillance Capitalism, Shoshana Zuboff (book)
Easy tutorials for privacy :
https://spreadprivacy.com/tag/device-privacy-tips
Great channels about privacy (with tutorials):
The Hated One : https://www.youtube.com/channel/UCjr2bPAyPV7t35MvcgT3W8Q
Techlore : https://www.youtube.com/channel/UCs6KfncB4OV6Vug4o_bzijg
Associations for the defense of privacy (information) :
https://ssd.eff.org/ https://www.laquadrature.net/es/ https://www.eff.org/deeplinks
Associations proposing excellent services respectful of privacy:
https://disroot.org/es/ https://komun.org/ https://framasoft.org/en/ https://snopyta.org/ https://www.drycat.fr/en
Good data protection practices:
Excellent site listing respectful services and programs:
Recommended operators:
https://www.eff.org/pages/quien-defiende-tus-datos
Telegram groups and channels
Privacidad, protección de datos y más : t.me/privacid t.me/techloregroup t.me/techloreofficial t.me/NoGoolag
Linux y libre : Proyecto tic tac LinuxMintEs mxantixes
Operating Systems
Linux :
Privacy-friendly Android :
Firefox
Firefox advanced configuration
MX Linux
Flash plugin : Enter the following command in the terminal to remove the proprietary Flash plugin : sudo apt purge --remove adobe-flashplugin flashplugin-installer pepperflashplugin-nonfree
Advert Blocker : Select all the options except "UNBLOCK" and then confirm.
Wi-Fi configuration : Right click on the Wi-Fi icon, modify the connections, select the active Wi-Fi, under Wi-Fi select Cloned MAC Address: Random. Under IPv6 settings, select IPv6 Confidentiality Extensions : On (preferred temporary address).
F-Droid
In order to find and download some applications from F-Droid, it is necessary add your repositories. For this, go to the F-Droid settings, then under "repositories", activate the "Guardian Project" repository and finally press the "+" and enter the desired addresses mentioned.
Bromite : https://fdroid.bromite.org/fdroid/repo
Langis (modified version of Signal to be used only if notifications do not arrive with the classic version of Signal (Aurora Store)): https://gitlab.com/TheCapsLock/fdroid-patched-apps/raw/master/fdroid/repo
Telegram
Start secret chats so that conversations are end-to-end encrypted extreme and do not go through the Telegram servers: contact profiles> the three dots above> start secret chat
Disable link preview in secret chats to avoid requesting links Telegram servers:
Settings> Privacy and security> Secret chats> Link preview
Blokada
Blocklists > enable the following blacklists:
- Energized : Basic (or Blu if RAM memory less than 4gb)
- DuckDuckGo Tracker Radar
- Exodus Privacy
- (Goodbye Ads : Samsung or Xiaomi (they only work for the models of those brands)) Encryption > select a DNS server from the following: DoH: Blah DNS, Digitale Gesellschaft (Europe), (OpenNIC). ((Not encrypted: DNS.Watch, Uncensored DNS, French Data Network (Europe))).
Newpipe
It may happen that Newpipe stops working due to modifications of part from Google on Youtube. In an effort to benefit as quickly as possible and automatically updates correcting these problems, it is recommended install Newpipe directly from its official site instead of F-Droid: https://newpipe.schabi.org/
FreeTube
Use Invidious as a proxy to avoid transmitting your data to Google: Settings : - Player Settings: enable "Proxy Videos Through Invidious"
- Advanced Settings: enter a functional Invidious instance
In case of problem, change the instance or simply deactivate "Proxy Videos Through Invidious ".
General configuration
Extension settings
It is important to authorize these extensions to work in private browsing and activate its automatic updates.
uBlock :
- Settings : activate everything under "Privacy"
- Filter Lists : activate ALL lists, except under “Regions” (only activate for languages used)
- (Add the lists from filterlists.com: Energized: Ultimate Protection, Xtreme + IP + Social extension)
- Follow the tutorial on the following web page to set the filtering rules dynamic (optional but recommended): https://www.maketecheasier.com/ultimate-ublock-origin-superusers-guide/
Chameleon :
Decentraleyes : No configuration necessary
CanvasBlocker : General: - check "Expert mode" - Presets > open > Stealth mode - Random number generator: non persistent APIs : check "Protect Window api" + accept captcha exception Misc : uncheck "Block data URL pages"
ClearURLs : request types: beacon,csp_report,font,image,imageset,main_frame,media,object,object_subrequest, other,ping,script,speculative,stylesheet,sub_frame,web_manifest,websocket,xbl,xml_dtd,xmlhttprequest,xslt
Cookie AutoDelete :
- Automatic Cleaning Options: activate all
- Extension Options: disable "Show notification after cookie cleanup"
Privacy Redirect : General : - select the desired instances Advanced : - enable "Always proxy videos through Invidious"
- Select "DASH" under "Invidious video quality"
(HTTPS Everywhere) :
- Only necessary for Firefox versions in which the "HTTPS-Only Mode" not yet implemented: Firefox ESR and mobile (Fennec)
- No configuration necessary
about:config settings
Access these settings by entering about: config in the Firefox address bar. Those various settings improve privacy, security, and performance. Items in parentheses are generally not desirable in all cases.
accessibility.blockautorefresh = true
((accessibility.force_disabled = 1))
beacon.enabled = false
browser.cache.offline.capacity = 0
browser.cache.offline.enable = false
browser.display.use_document_fonts = 0
browser.send_pings.max_per_link = 0
browser.sessionhistory.max_entries = 15
Maximum number of pages available with "precedent", Firefox lightens
browser.sessionhistory.max_total_viewers = 4
Maximum number of pages loaded with "precedent", Firefox lightens
browser.sessionstore.interval = 50000
browser.sessionstore.privacy_level = 2
(browser.startup.homepage_override.buildID = delete)
browser.urlbar.autofill.enabled = false
(browser.urlbar.maxRichResults = 0)
browser.urlbar.speculativeConnect.enabled = false
browser.urlbar.trimURLs = false
browser.xul.error_pages.expert_bad_cert = true
captivedetect.canonicalURL = delete
device.sensors = false for all elements
dom.allow_cut_copy = false
dom.battery.enabled = false
dom.enable_performance = false
dom.enable_resource_timing = false
dom.event.clipboardevents.enabled = false
dom.event.contextmenu.enabled = false
dom.push = false for all elements + delete addresses and identifiers
dom.serviceWorkers.enabled = false
dom.vr.oculus.enabled = false
dom.webaudio.enabled = false
gamepad = false for all elements
geo = delete all addresses
geo.enabled = false
(gfx.font_rendering.graphite.enabled = false)
google = false for all items + clear addresses
javascript.options.baselinejit = false
javascript.options.ion = false
javascript.options.native_regexp = false
layers.acceleration.force-enabled = true
layout.css.visited_links_enabled = false
mathml.disabled = true
((media.gmp-widevinecdm.enabled = false))
((Disable DRM, yes DRM videos not necessary))
media.navigator.enabled = false
media.video_stats.enabled = false
network.captive-portal-service.enabled = false
network.dnsCacheEntries = 4000
network.dnsCacheExpiration = 43200
network.dnsCacheExpirationGracePeriod = 43200
network.IDN_show_punycode = true
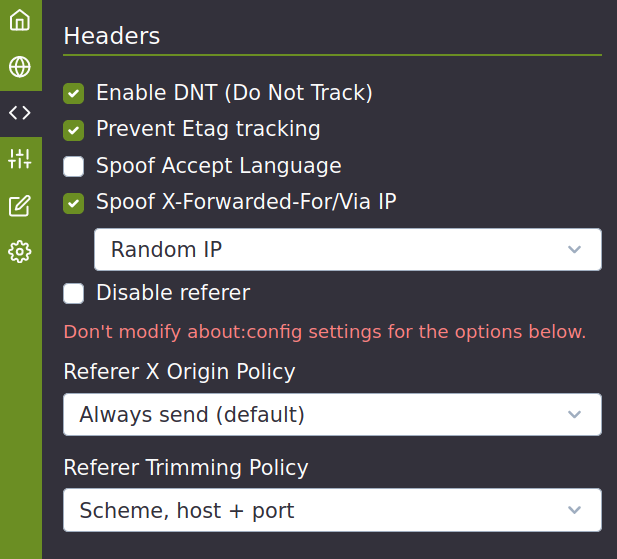
network.http.referer.XOriginPolicy = 0
network.http.referer.XOriginTrimmingPolicy = 2
network.http.referer.spoofSource = true
network.http.referer.trimmingPolicy = 2
network.http.speculative-parallel-limit = 0
network.manage-offline-status = false
normandy = false for all elements + clear addresses and identifiers
pocket = false for all items + clear addresses and identifiers
privacy.clearOnShutdown.offlineApps = true
privacy.spoof_english = 2
privacy.trackingprotection.socialtracking.enabled = true
report (reporter/reporting) = false for all items + delete addresses
safebrowsing = false for all items + clear addresses and identifiers
security.cert_pinning.enforcement_level = 2
security.mixed_content.upgrade_display_content = true
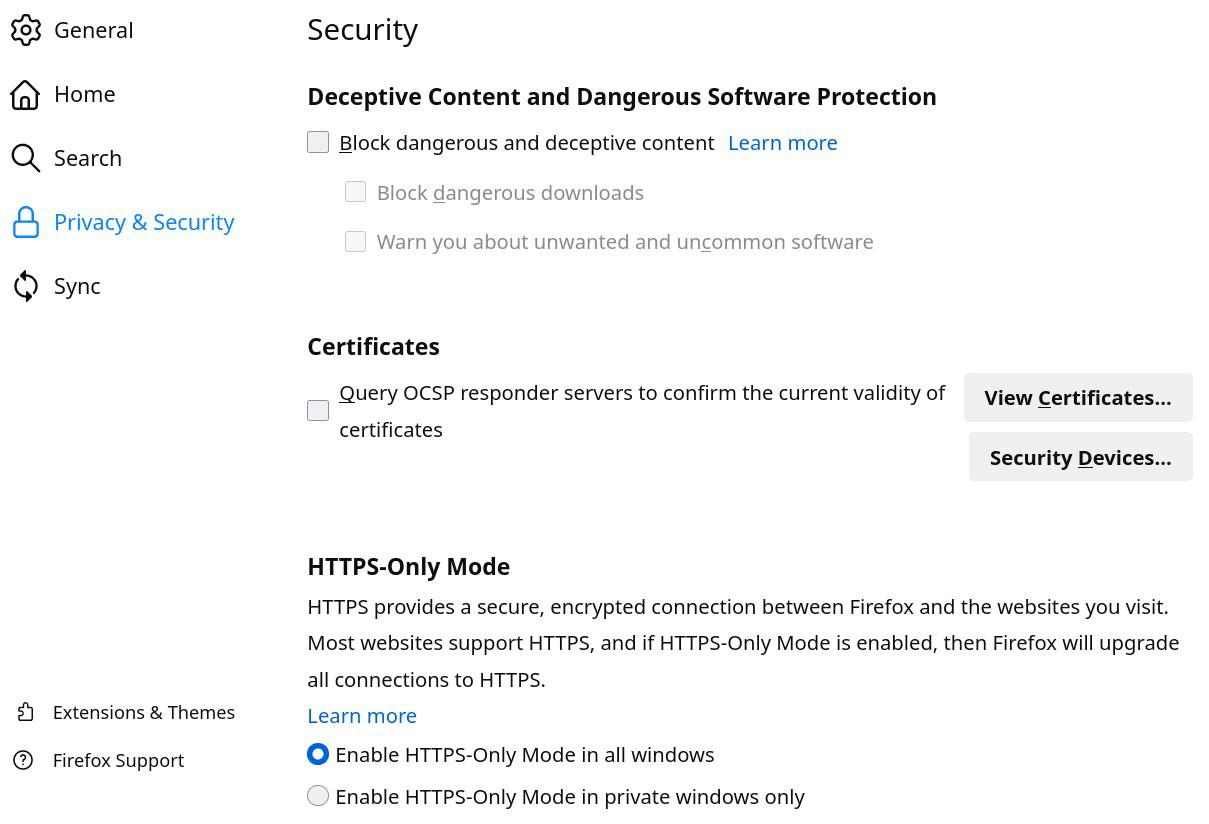
security.OCSP.enabled = 0
security.ssl.enable_false_start = false
security.ssl.enable_ocsp_must_staple = false
security.ssl.enable_ocsp_stapling = false
security.ssl.require_safe_negotiation = true
security.ssl3.rsa_des_ede3_sha = false
security.tls.enable_0rtt_data = false
security.tls.version.min = 3
telemetry = false for all items + clear addresses and identifiers
ui.use_standins_for_native_colors = true
webgl.disabled = true
webgl.enable-debug-renderer-info = false
webgl.enable-webgl2 = false
Only if Chameleon extension is not used :
(privacy.resistFingerprinting = true)
(Better to put "false" and fake the fingerprint with Chameleon)
These should be configured directly with Chameleon if it is installed:
media.peerconnection.ice.default_address_only = true
media.peerconnection.ice.no_host = true
((media.peerconnection.enabled = false))
privacy.firstparty.isolate = true