-
Notifications
You must be signed in to change notification settings - Fork 2
GSoC_2014_Advanced_Fuzzing
This project aims to improve the fuzzing functionality provided by ZAP. A stable version of the current HTTP-multifuzz add-on will be created and several new features will be added (detailed list below). Beyond that, the same fuzzing options will be provided in all other add-ons employing fuzzing mechanisms (i.e. plugnhack, SSE and Websockets).
In the course of this project the following new features will be provided:
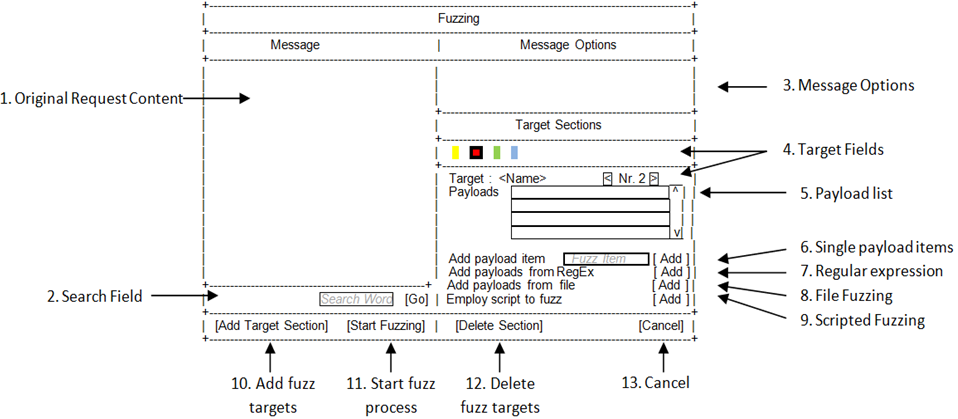
- Development of a stable HTTP - multifuzzing add-on
- Revised choice and administration of payloads:
- Revised UI (see sketch)
- Use of regular expressions as payloads
- Inclusion of scripts as payload resources
- Inclusion of scripts for request manipulation
- Inclusion of scripts for the detection of changes in response
- Revised UI (see sketch)
- New administration / manipulation of fuzzing results based on JBroFuzz-project
- Additional user interfaces
- Grouping of results and summarize category distinctions
- Graphing results
- Additional user interfaces
- Ex- and import of results into external (.csv)-files
- Documentation of the fuzzing tool and its use
This section presents an overview of when the individual features are planned to be implemented.
In addition to the listed steps, a new version of the multi-fuzzing add-on will be released at the end of each week.
Changes to core files will be kept to a minimum and specifically listed in the tables below.
Please note however, that this is not a final schedule and may be subject to changes should new features be added or problems arise.
| Goal | Status |
|---|---|
| Introduction to community | Done |
| Setup of project wiki page | Done |
| Specification of add-on design e.g. UML diagram / flow chart | Ongoing |
| Preparation of current add-on | Done |
| Goal | Status |
|---|---|
| Final preparation of HTTP multi-fuzzing add-on | Done |
| 1. Shift of files to core | Done |
| Goal | Status |
|---|---|
| Design and implementation of GUI (similar to sketch) | Done |
| Implementation of search option for request field | Done |
| Reconciliation with HTTP add-on | Done |
| Goal | Status |
|---|---|
| Implementation of length based fuzzing; Issue 625 | Done |
| Implementation of regular expression payloads | Done |
| Goal | Status |
|---|---|
| Study of usage of scripts in e.g. Active Scan Rules | Done |
| Adaptation for fuzzing purposes (request manipulation) | Done |
| Implementation of scripting payloads | Done |
| Goal | Status |
|---|---|
| Implementation of response inspection by scripts | Done |
| Testing / Feedback | Done |
| 2. Shift of files to core | Done |
| Goal | Status |
|---|---|
| Implementation of SSE | Done |
| Goal | Status |
|---|---|
| Study of JBroFuzz | Done |
| GUI design for result manipulation | Done |
| Goal | Status |
|---|---|
| GUI design for result manipulation | Done |
| Implementation of result manipulation | Done |
| Goal | Status |
|---|---|
| Implementation of result manipulation | Done |
| Testing / Feedback | Done |
| Goal | Status |
|---|---|
| Overall structure of Fuzz results | Done |
| Implementation of ex-/import options | Done |
| Goal | Status |
|---|---|
| Finalizing fuzz result ex-/import | Done |
| Clean up of code base | Done |
| Goal | Status |
|---|---|
| Update project documentation | Done |
| Final commit | Done |
In the course of the project this section will be updated to provide guidance for the use of the features created and point to further documentation.
The new features that have been implemented so far are:
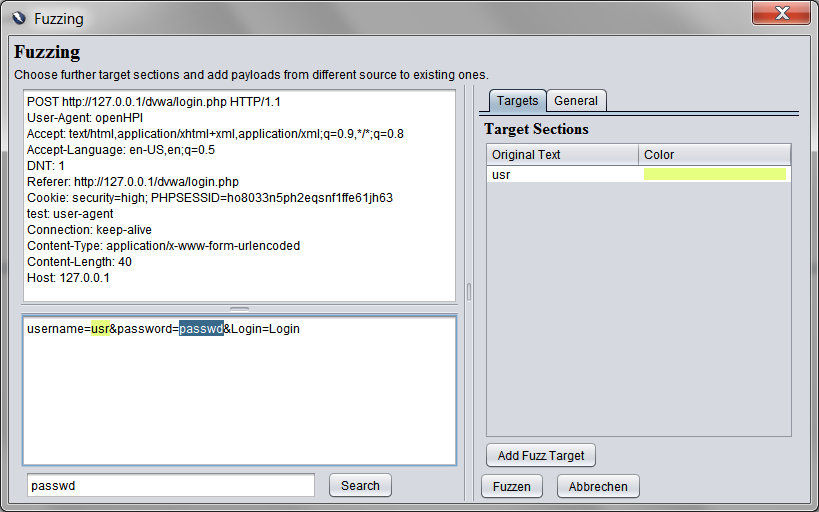
This dialog is opened by right-clicking on the request to be fuzzed and selecting "Advanced Fuzz...". On the left side, the initial request is displayed and selected targets are marked up. Furthermore, it is possible to search through the request using the search bar underneath. On the right hand side two tabs are defined:
Targets
This tab contains an overview of the defined target sections. To add a new target simply select the appropriate section on the left side and press "Add Fuzz Target". This will automatically open the payload definition dialog (see below). Already defined target sections can be edited by selecting an entry in the table which will open a payload definition dialog for the matching target section.
General
This tab contains the options affecting the entire request that have been included in previous versions of the fuzzing tool.
Once at least one non-empty target section has been defined the fuzzing process can be started using the "Start"-button.
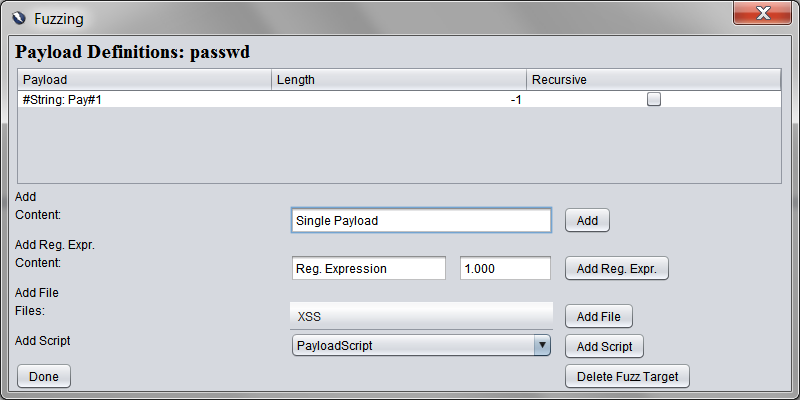
This dialog administrates the payloads inserted for one particular target. On top there is an overview of already defined payloads. Underneath there are four possible ways of adding new payloads:
1. Single Payloads
Inserting a string in the text field and clicking add will replace the target with that exact string during the fuzz process. No further options need to be selected.
2. Regular Expressions
This will generate (all) strings matching the particular expression and insert them instead of the target. However, due to the use of a custom generator only a limited number of operators is accessible. Valid expressions can contain:
- literals
- concatenation and bracketing
- the union operator '|'
- '?', '
*' and '+' as usual repetition operators
- [b-c] as a range of possible characters
- '.', '\w' for any character or letter
- '\d' for any digit
- '\s' for any whitespace
To define a regex payload enter the expression in the first field and choose a maximum number of tokens that are in fact generated (if this is set higher than the actual number of matching strings less payloads are created). Click 'Add' and choose a maximum number of signs generated tokens can have.
3. Fuzz Files
To insert payloads from a pre-defined file choose the appropriate category and file in the drop-down menu and click "add".
4. Payload Scripts
To generate payloads via a script, a script has to be created and enabled previous to the start of the fuzzing process. Instructions how this can be done are included in the template. Active scripts will be shown in a drop down menu and can be added by selecting the appropriate one and clicking "Add".
Beyond that, string payloads and payloads from a file can be trimmed to a specific length, by setting the length parameter of the payload to the desired length.
This can also be combined with the recursive fuzzing option which is available for file payloads only. If set, the payloads from this file will be recursively concatenated / trimmed to reach a certain target length (The default value is the length of the target section, but can be overruled by the length field).
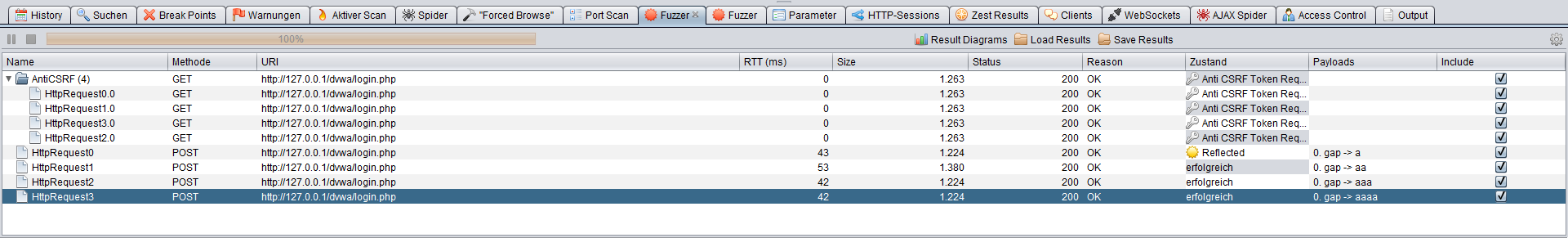
1. Grouping and Graphical presentation
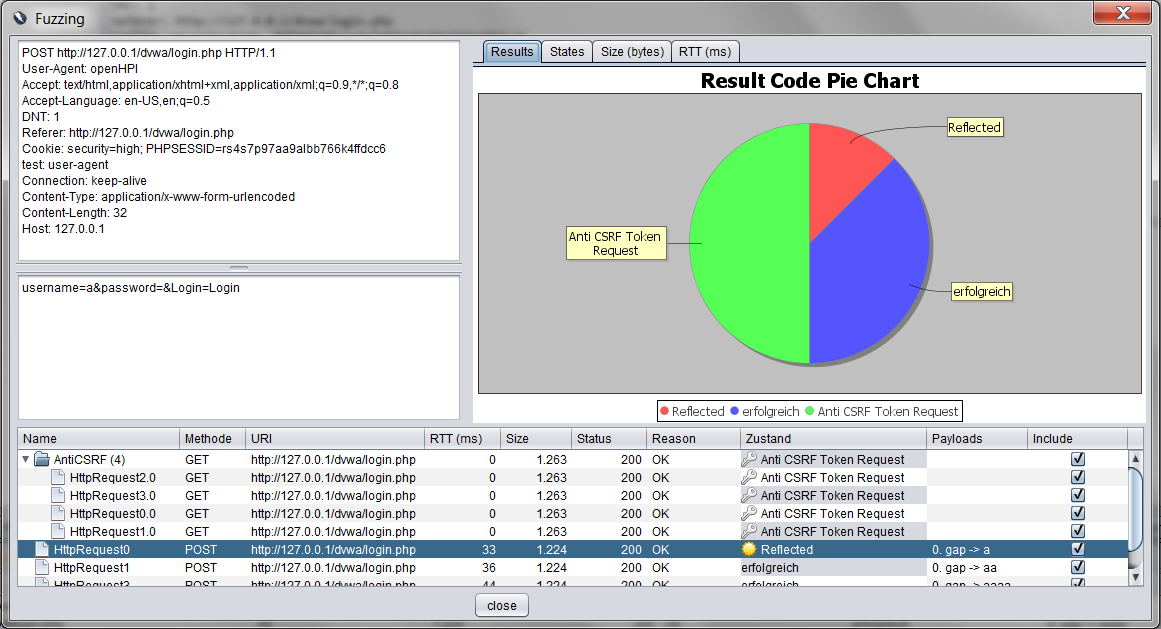
Once the fuzzing is completed, a list of the results will be shown in the fuzzing tab:
Selecting and right-clicking on an entry will allow to change its label or assign it to a new group of results or to an existing one. Groups can be collapsed and expanded in the table at will.
The "Result Diagram" button opens a new dialog consisting of three components.
On the bottom of that dialog the same table of all fuzzing results is shown. Groups and names that are defined in this dialog will be available after closing it.
Furthermore, the dialog shows the message, corresponding to the currently selected entry, for closer inspection.
Lastly, there is a tabbed panel which contains several different diagrams. The specific diagrams that are available vary with the message type. The data sets which are used to construct these diagrams correspond to the results with a selected "Include"-option.
2. Result ex-/import
Apart from the Diagrams button, two buttons for the ex- and import of fuzzing results have been created. These save the requests currently contained in the table into a file of your choice and load them at a later point from those files. While the assigned labels for requests are kept, group information is lost in that process.